- Leadership Team
- Our Clients
- Project Management
- Outsourced IT
- Education Services
- Consumer Services
- Infrastructure
- Training and Support
- Training Guides
- Training and Certifications
- Certified Trainers
- Jamf Certifications
- Jamf Certified Trainers
- Jamf Onboarding
- Remote Monitoring
- Technical Articles
- Remote Support
Technical professionals. Trusted advisors. Certified expertise.

A Guide for Configuring the macOS Catalina Kerberos Single Sign-On Extension

The Kerberos single sign-on (SSO) extension on macOS Catalina10.15 will log users into native apps (for apps that support Kerberos authentication) and sync local user passwords with a directory service such as Microsoft Active Directory. With the Kerberos SSO extension, users do not have to provide their user name and password to access native apps, file servers, proxy servers, and URLs that support Kerberos authentication. The Kerberos SSO extension is sandboxed (this guide explains the ramifications of sandboxing) and requires a mobile device management (MDM) solution (that supports the Extensible Single Sign-on (SSO) configuration profile payload) to enable the extension.
Corporate Headquarters New York
80 Orville Drive Suite 100 Bohemia, NY 11716 Tel: (866) 518-9672 This email address is being protected from spambots. You need JavaScript enabled to view it.
Connecticut
65 High Ridge Road #510 Stamford, CT 06905 Tel: (866) 518-9672 This email address is being protected from spambots. You need JavaScript enabled to view it.
3321 SW 194th Terrace Miramar, FL 33029 Tel: (866) 518-9672 This email address is being protected from spambots. You need JavaScript enabled to view it.
218 Barksdale Drive Broussard LA 70518 This email address is being protected from spambots. You need JavaScript enabled to view it.
4 Knollwood Place Joliet, IL 60433 This email address is being protected from spambots. You need JavaScript enabled to view it.
10 Grosvenor Court Rayners Road London SW15 2AX UK
- White Papers
Stay Connected
- Read our Blog
- Read the News
- Staff Email
- Training Policies
- Privacy Policy
© Copyright 2023, HCS Technology Group. All Rights Reserved.

Mobile Jon's Blog
Demystifying kerberos single sign-on for ios.
- September 9, 2017
- 16 Comments
Hello everyone,
Well a few articles in and people still think I’m not 100% stupid. As we say in Boston, that is wicked pissah. I want to take a moment or two to editorialize what it’s like to be a mobile systems engineer in the enterprise world. We are MORE stuck with stigmas that almost any position. People just think we’re administrators and not as talented as other infrastructure architects or engineers. I think that’s perfectly okay! I got my job at BlackBerry working next to people that were principal’s at Microsoft for 10 years so I’m used to an uphill battle.
So now I have setup what I wanted to blog about today….an aspect of “identity management.” Yes I know that is becoming the most ridiculous word ever lately. So many things are being lumped into those two words. So let’s rewind three years ago, Apple thought about how could they actually make their product enterprise grade. Then almost like the “Brilliant!” guys from that beer commercial some time back, they decided let’s give people Single Sign-On, but let’s “NOT” really tell them how to do it, make it work, or make it even remotely easy to accomplish it.
WTF is Kerberos?
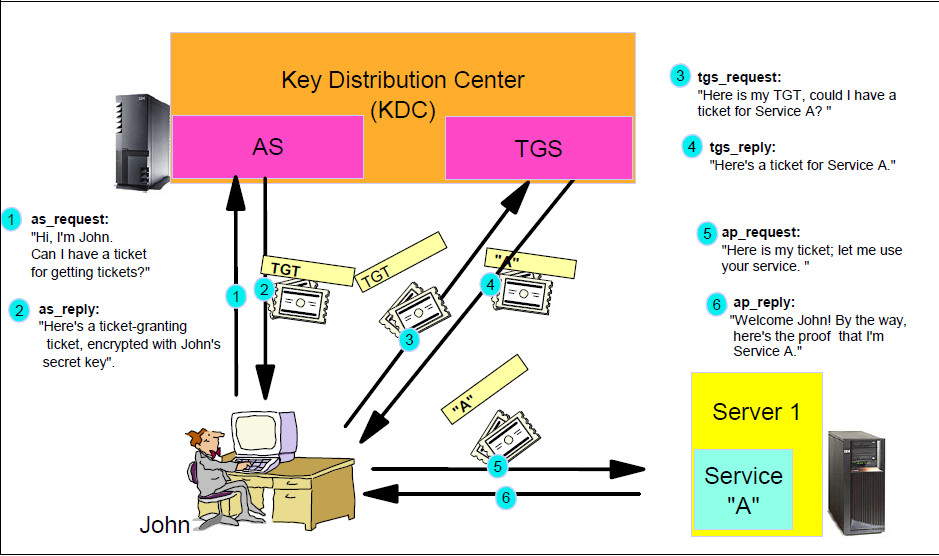
I try not to make any assumptions. So people ask what “exactly” is kerberos? This is kerberos!

Technically, I’m right that is Kerberos of greek mythology from the kids movie Hercules. I also remember Kerberos quite well from my World of Warcraft and Final Fantasy days, but obviously you don’t want to hear about 40-man raids in a top raiding guild. Okay…moving on!
Kerberos is a network authentication protocol developed and maintained by MIT since the 80s. The image below is one of my favorite images. For our purposes, to keep it really simple since this isn’t a class on Kerberos, we use kerberos with certificate-based authentication on iOS to authenticate seamlessly to applications. The useful thing about Kerberos with CBA (Certificate-Based Authentication) is that you are able to use it without being domain-joined to achieve Single Sign-On in a seamless way if you build your environment correctly
What are the requirements in iOS?
A major part of the reason I decided to write this article is that the information out there is VERY inconsistent. I know everyone hates BlackBerry and blah blah, but don’t you wish your MDM vendor was even in the same ballpark on documentation? I know that I do.
So, for requirements it’s straight forward:
- Either publically or over VPN, you must publish SRV records with your servers running a KDC aka _kerberos._tcp
- You need to build a properly-configured Single Sign-On Payload (sounds much easier than it actually is, we’ll cover that later)
- Deliver the KDC service certificate to the device
- Allow the device to reach your KDC servers over Port 88
- Deliver certificates that meet the Kerberos requirements (which we’ll also cover later)
It’s very possible that I’m missing a few things that people will nerd/kerberos rage on me later, but these have been the key items that I have to make sure I catch on my implementations. I hope for your sake that you have a SSO product that has a cloud KDC to simplify many of these steps, such as VMWare Identity Manager
iOS Single Sign-On Payload
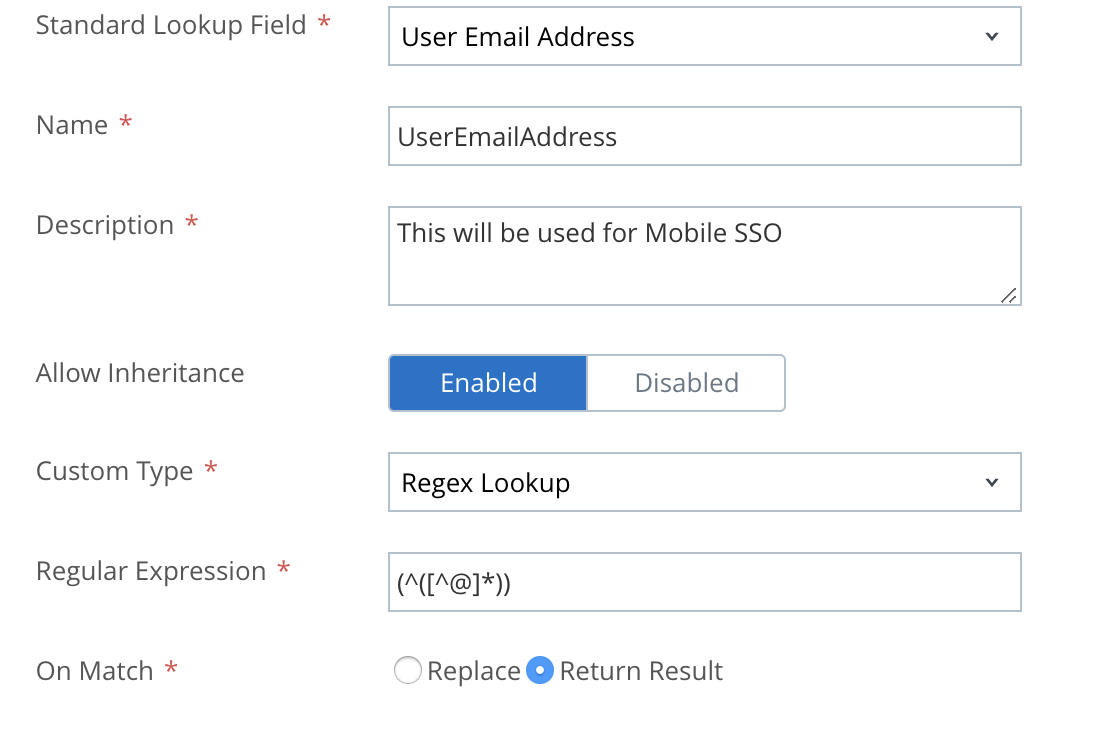
I know you think this is just I’ll write this and that and it will be easy in 10 lines of code (or JSON for that matter). So before you do anything, you need to analyze how your AD structure is. This is what I mean, the two things that really matter to you is your sAMAccountName and your UPN (User Principal Name). Sure most companies will be JTowles is my username and [email protected] is my UPN. Now in the O365 world, the best practice is SMTP=UPN which is why I said it like that.
The problem you COULD run into is if you do something different with your username like TowlesJ, which will break your attempts all together. Let me explain how it works, then I’ll cover it more in certificate requirements. Your email address up to the @ sign must match your username aka Kerberos Principal Name. Failure to do so, will cause Kerberos Authentication to fail. Simply, you will need to engineer around the issue, which you can do in some MDM’s which I will cover in a moment. Essentially, when the authentication happens, it will require that your Kerberos Principal Name in the payload correlate to an entry in one of two fields of the certificate it presents to your KDC. Most times, you will be leveraging some form of Kerberos Constrained Delegation to get Kerberos tickets and have a seamless flow.
Likely the issue you are asking yourself is, will I need to manually create this flow for every single user if my username doesn’t match? The answer is no! Depending on your MDM, it will hopefully be able to leverage lookup values, which you can likely work with RegEx expressions to achieve. For example, perhaps you use a Regex express to take your email address and strip out the @ and domain to make your email address and kerberos principal name match. This screenshot below shows how you would accomplish exactly that. The typical best practice is to pass the username into the Kerberos Principal name field, but in some circumstances we must be engineers
So that’s the first part of your Kerberos SSO Profile. The other key parts are:
- Realm (which is your realm in ALL CAPS, typically the domain) aka EXAMPLE.COM
- You tie the renewal certificate to another component of your payload like your SCEP profile or however your MDM is accomplishing certificate automation.
- URL Prefixes for Kerberos Authentication (this is whatever KDC endpoints you are hitting) which is typically either a cloud Kerberos endpoint or some authentication layer in your environment
- com.apple.mobilesafari (iOS Safari, because duh!)
- com.apple.SafariViewController (this is for apps that open a Safari window inside of their application)
- Whatever Apps you are enabling for SSO
D on’t forget to add in the KDC certificates so that you can actually authenticate. It turns out that Kerberos likes security.
Certificate Requirements
I found the certificate stuff to be the hardest part of making this actually work. Part of the problem is that vendors (whether its Apple being distant or your MDM) they all feel like its not their job to help make it work end-to-end. I suggest before getting started to install the Enterprise SSO Apple Profile to help with debugging via xCode.
So, its two parts really first what you need to do on the CA and then what you need to do on the MDM side.
On the CA side, these are the requirements:
- Grant the OID1.3.6.1.5.2.3.4 (Kerberos Client Authentication) to the Template
- Grant the OID1.3.6.1.5.5.7.3.2 (Client Authentication) to the Template
- Make sure your service account has access to read/enroll the certificate along with giving authenticated users read only access or your generations will fail.
On the MDM side, these are the requirements:
- Create the Subject Name with your NTID
- UPN with the user’s UPN as the value
- Email with the user’s email as the value
- Optionally create a DNS field for UID if you are doing device compliance (i.e. DNS Name UID=(Whatever the UID of the device is)
- Make sure the certificate can be used for signing and encryption
- Make sure the template you provide on the iOS side matches the template name (NOT THE TEMPLATE DISPLAY NAME) from your CA
Like I said earlier, make sure that the content before the @ sign on one of your SANs matches the Kerberos principal name in the profile. Failure to do this will result in authentication failures. I also strongly suggest to keep this separate from your WiFi or VPN payloads as you may have to update it frequently to add new applications or tweak it.
Final Thoughts
I will say from experience that this can be a very frustrating chore getting actual seamless Mobile SSO working, but it is so rewarding once you are successful. You should definitely make sure that you setup proper step-up/step-down methods in your SSO posture. Failure to do so could create a major issue for your users. It’s one thing, to have to put in your username and password but an entirely different situation to not be able to access a critical application. As an engineer, you always need to plan for the worst case scenario and have a break glass policy. I hope this helps people as I know these issues were not without their pain points for me.
16 thoughts on “Demystifying Kerberos Single Sign-On for iOS”
Very interesting article! I came to your blog looking for a solution to a certain case. We have airwatch and we use iOS mobile SSO. Authentication goes to ADFS 3.0 which federates different apps. During the first login for some days of inactivity login to such app from iOS can take up to 30-40s. No issues when we do not use iOS mobile SSO. Any thoughts, did you saw something similar?
Do you run VIDM yourself or is it in their cloud?
We run it on premises in our DCs.
Do you use their cloud KDC or internal KDC for Mobile SSO for iOS
Thanks for follow up!
Internal KDC, all is on prem. ADFS is on 2012 R2.
Adfs doesn�t matter at all for this. Essentially what Kerberos for mobile SSO is doing is authenticating against the default policy for VIDM. In this circumstance, I would suggest using VIDM as the identity provider. The biggest issues with authentication happen because VIDM nodes aren�t very good at authentication. I suggest using the VIDM connectors as your authenticators preferably as VMWare ESCs. I�ve found in private clouds that VIDM connectors will auth about 5 times faster than individual nodes. I would also suggest using a hybrid KDC deployment over internal KDC for VIDM. The reason is that you don�t want to open traffic up to TCP/88 from external devices when something is already in place. What I tend to find in a lot of environments is that port 88 is blocked on most wireless networks so you might be running into a few challenges there. The optimal architecture for running VIDM is a cluster in the DMZ and your connectors over ESCs internally handling certs, radius, and Kerberos.
It�s a stronger security posture and eliminates some of the challenges
Just to follow up, it�s not an ADFS issue at all, it tends to be an end to end issue. I would definitely be using VIDM as my default IDP and then use ADFS for the apps themselves. Kerberos of course is handled on the nodes for Mobile SSO for iOS vs desktop Kerberos on the connectors
One other thing I thought of, have you checked the public DNS entries to make sure you aren�t having issues there? If I was you I�d probably install the iOS Kerberos debugging profile to see if it tells you more. PCAPs on the iOS device might help also to see where the latency is getting created
We face this issue in internal network. We have Cisco ISE and CDA which ensures that we have the same vlan, no matter if WiFi or lan. Btw as realm we have AD domain name, which is UPN as well and is not routable.
I wonder if it has anything to do with the DNS records at all. Did you try to hit a specific node instead of the load balancer to rule things out? I would honest try to nail down the individual timing of each action. Internal KDC is really a few settings: DNS, the KDC servers you specify in the run-time Config and the cert itself. That�s outside of the stuff like OCSP etc.
I�d honestly try to build a test environment with the cloud KDC and see if it�s faster. I prefer cloud KDC personally
Great article, Thanks for the info. We have Jamf as our iOS MDM and SSO is the key to user acceptance (Lots of internal hosted sites through per app which is a pain). Going to give this a spin later. wish me luck!

MOBILEJON, This is a very detailed article you put together. Would you be chance have any suggestions on what may be keeping our mobile SSO auth from working. We are using AirWatch v1811 with VIDM on-premise connected to Cloud KDC. Our users samaccount doesn’t match our UPN in AD. So when our users enroll in Airwatch their username lookup value is short login ID not email formatted value that we have set for UPN.
When using lookup value in AirWatch some will cause profile install failure stating incorrect value used for “PrincipleName”. Breakdown of the error reported by IOS.
Error Code 1000 The profile �iOS Mobile SSO/V_12� is invalid. Error Code 2000 The payload �iOS Mobile SSO/V_12� is invalid. Error Code 2004 The field �PrincipalName� contains an invalid value. Profile iOS Mobile SSO
Hi Brandon,
So you need your certificate to have a SAN as NT Principal Name that matches the principal name of your Kerberos Profile.
So your Kerberos Profile will ALWAYS have your NTID aka samAccountName. The certificate basically needs the NT Principal Name field to match that. So if you are using DCOM you can add a SAN that matches that. I believe you can either just do a SAN attribute that matches it called NT Principal Name or an email address starting with the NT Principal Name (e.g)
Your kerberos profile should have Kerberos Principal Name as {EnrollmentUser} , Realm as VMWAREIDENTITY.COM , and Renewal Certificate as your CA or the AW SCEP certificate.
So if my KRB Prin is jjtowles then I should have an entry in the SAN called jjtowles also. If you can’t achieve that, let me know.
This has been a great resource but unfortunately I have not been to get SSO to work in my environment . I quickly tried in the VMTestDrive sandboxes of IDM & UEM and was successful.
I believe that my problem is with the on-prem KDC not quite right. I have port 88 open and the SRV records set but I keep getting this error: _gss_mg_error: captured unable to reach any KDC in realm MONCTON.CA, tried 2 KDCs (-1765328228) from underlaying mech kerberos 5
Is there a way to disable on-prem KDC and use CLOUD? I have also had to deal with SAM & UPN not being the same.
Check out this article: https://docs.vmware.com/en/VMware-Identity-Manager/3.3/idm-administrator/GUID-E8A58680-78D4-4163-833E-EDD7DED32ECB.html?hWord=N4IghgNiBcIEoFNIFsQF8g
I always recommend using the cloud KDC for On-Premise if your security team is good with that
You will also need this article I believe to change where it�s currently pointed: https://docs.vmware.com/en/VMware-Identity-Manager/3.3/vidm-install/GUID-F8BDC75E-150B-4FC3-AA70-B330E26551D3.html?hWord=N4IghgNiBcIEoFNIFsQF8g
Let me know what you think Cancel reply
Copyright © 2024 Mobile Jon’s Blog, All rights reserved.
Discover more from Mobile Jon's Blog
Subscribe now to keep reading and get access to the full archive.
Continue reading
Device Harmony
Device Management
Endpoint Detection & Response
Integrations
iOS & iPadOS
Resources Hub
Customer Stories
MacAdmins Community
Security Details
Technology Partners
Become a Partner
Register a Deal
Partner Portal
About Kandji
News & Press
Extensible Enterprise SSO Framework: Kerberos Extension and What’s New with Big Sur

Apple’s Extensible Enterprise SSO (single sign-on) framework has big implications for device management and authentication. In this article, we’re going to take a look at how the Kerberos single sign-on extension works, what it can do for you, and how you can configure and deploy it. We’ll also discuss how Kandji’s SSO Extension Profile makes it easy to leverage the Kerberos Extension.
Here's an overview of this guide:
A Primer on SSO Extensions
- What’s the Kerberos Single Sign-On Extension?
Building and Deploying a Kerberos Configuration Profile
- What’s New in macOS Big Sur Kerberos Extensions?
At the World Wide Developers Conference (WWDC) 2019 , Apple introduced the Extensible Enterprise Single Sign-On (SSO) framework. SSO lets users access multiple applications with a single set of credentials, simplifying the authentication process and streamlining the login experience for both native and Safari-based applications.
What makes this possible are redirect and credential SSO extensions, which let identity providers (IdPs) build programs that can achieve seamless SSO experiences. One such program is the Microsoft Enterprise SSO plug-in for Apple devices, which we’ll talk about later in this article.
Using these extensions requires a device management (MDM) solution – to enable them, you need to deploy the extensible SSO MDM profile (and associated domains for redirect credentials). We’ll get into more depth on what these extensions are and how they’re deployed next.
What are Redirect Extensions?
Redirect extensions are intended for modern authentication methods, such as OpenID Connect, OAuth, and SAML2. You can use them for authentication with Safari and native applications.
Deploying redirect extensions requires an MDM payload and associated domains. The payload must be delivered using your business’ MDM solution. For the information regarding the payload’s redirect configuration, you can read our Identity and SSO guide .
As for associated domains, these simply ensure that you own the traffic that’s being redirected. You need to configure associated domains in the host app that contains your extensions, which you can read about in Apple’s support documentation.
What are Credential Extensions?
Credential extensions are intended for challenge/response authentication. These extensions request data and then get challenged for authentication, unlike redirect extensions, which request credentials before data. They can also be used for Safari and native apps.
If you want to deploy a credential extension, you don’t need to worry about associated domains, which were necessary for redirect deployment. You just need to deliver a credential payload using your business’ MDM solution. You can find information on this payload in the guide we mentioned earlier.
What’s the Kerberos SSO Extension?
The Kerberos Single Sign-on extension is a credential extension designed to manage Kerberos/Active Directory credentials, synchronize local and Directory passwords, and support authentication via smart cards, MDM-provided certificate-based identity, and username/password. Included in iOS 13, iPadOS, and macOS Catalina, this extension is a replacement for Enterprise Connect.
Though Kandji fully supports Apple’s Extensible Enterprise SSO framework, most IdPs are still in the process of developing support for it. If you’re curious if your IdP is working on this extension or are uncertain when it will be ready, we recommend encouraging them so you can leverage the Extensible Enterprise SSO framework (for macOS and iOS) as soon as possible.
Microsoft released a public preview, available for iOS, called Microsoft Enterprise SSO plug-in for Apple devices. This plug-in can achieve SSO for Azure AD accounts across any compatible iOS apps that leverage Microsoft Authentication Library (MSAL). For information about enabling this SSO extension with your MDM solution or using it in an application, you can read Microsoft's documentation .
Why is Microsoft the only one that’s ready? We can only speculate, but so far they’ve developed the most comprehensive solution. While we haven’t heard anything official from Microsoft, we can speculate that the macOS version of the Extensible Enterprise SSO Extension may be ready by the end of 2020.
Transitioning from Enterprise Connect
The Kerberos Single Sign-on extension replaced a similar tool called Enterprise Connect. Transitioning to Kerberos isn’t necessary if you’re upgrading your Mac computers to macOS 10.15 (Enterprise Connect will still function as usual). Still, Apple advises businesses to begin making plans to transition to Kerberos.
In the support documentation on the Kerberos Single Sign-on extension, Apple says Kerberos will meet the needs of the vast majority of organizations. However, if your business meets the following criteria, you may not be able to transition from Enterprise Connect, or you may only be able to achieve a partial transition:
- If you use an MDM solution that doesn’t support user-approved MDM (UAMDM) enrollment, or if you aren’t using an MDM solution at all.
- If you have Mac computers running on macOS 10.14 or earlier. In this case, Apple advises that you leave these systems on Enterprise Connect until you upgrade them to macOS 10.15.
- If you’re using an Active Directory functional level of Windows Server 2003 or earlier.
Functions of the Kerberos Single Sign-On Extension
Before we break down how you can build and deploy a configuration profile for this extension, we’re going to do a quick survey of the functions that Kerberos authentication (for macOS and iOS) can perform. For complete details of what the Kerberos Single Sign-on extension can do, you can read the support documentation that we mentioned earlier.
Live password testing : You can use the Kerberos extension to test user passwords in most configurations of Active Directory. This includes informing users of password requirements while creating a new password, as you can see in the image below.
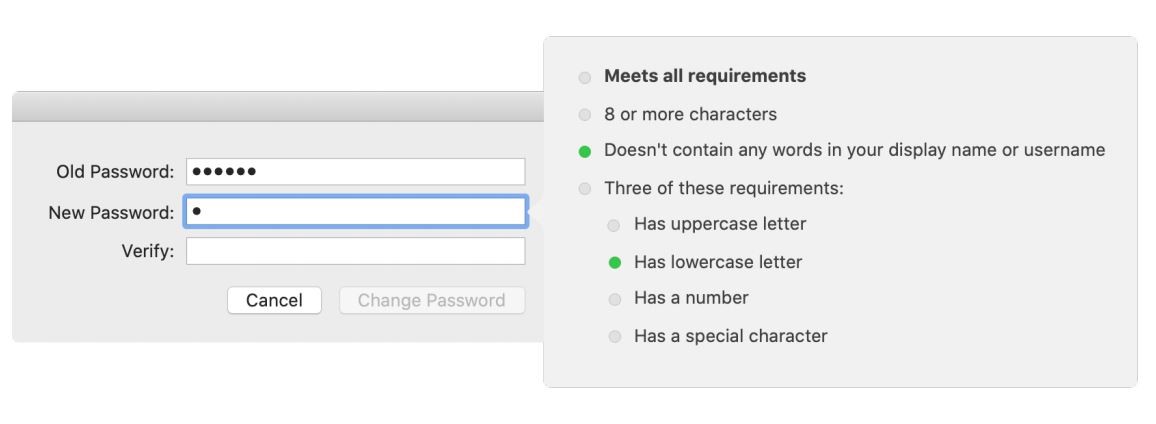
Image source: apple.com
Password requirements display : If you can’t use the live password testing function, you can configure the Kerberos Single Sign-on extension to display your business’ password requirements as users enter their new passwords. This requires setting “pwReqText” in your configuration profile to a string containing the text you want to appear.
Changing or disabling password functionality : If you don’t allow password changes against Active Directory, then you might not be able to use the standard password change functions of the Kerberos Single Sign-on extension. To disable this function, set “allowPasswordChanges” to FALSE in the configuration profile.
Password change website support – (Mac) : You can configure the Kerberos Single Sign-on extension to open a password change website when users select “Change Password” or interact with a password expiration notice. Apple only recommends using this feature for local accounts – mobile accounts aren’t supported. To do this, set “pwChangeURL” in your configuration profile to the URL of your password change page.
Password sync – ( Mac) : You can use the Kerberos Single Sign-on extension to sync users’ local account passwords with their Active Directory passwords. This requires setting “syncLocalPassword” to TRUE in the configuration profile.
Smart card support - (Mac) : You can also use smart card-based identities for Kerberos authentication (Mac only). However, token-based drivers are not supported, so the smart cards must have a CryptoTokenKit driver available. To use this function, you must make sure that your Active Directory domain is configured to support smart card authentication.
Distributed notifications - (Mac) : When an event occurs, macOS apps and services can use distributed notifications to communicate relevant information with other apps and services. You can use the Kerberos extension to post the following distributed notifications:
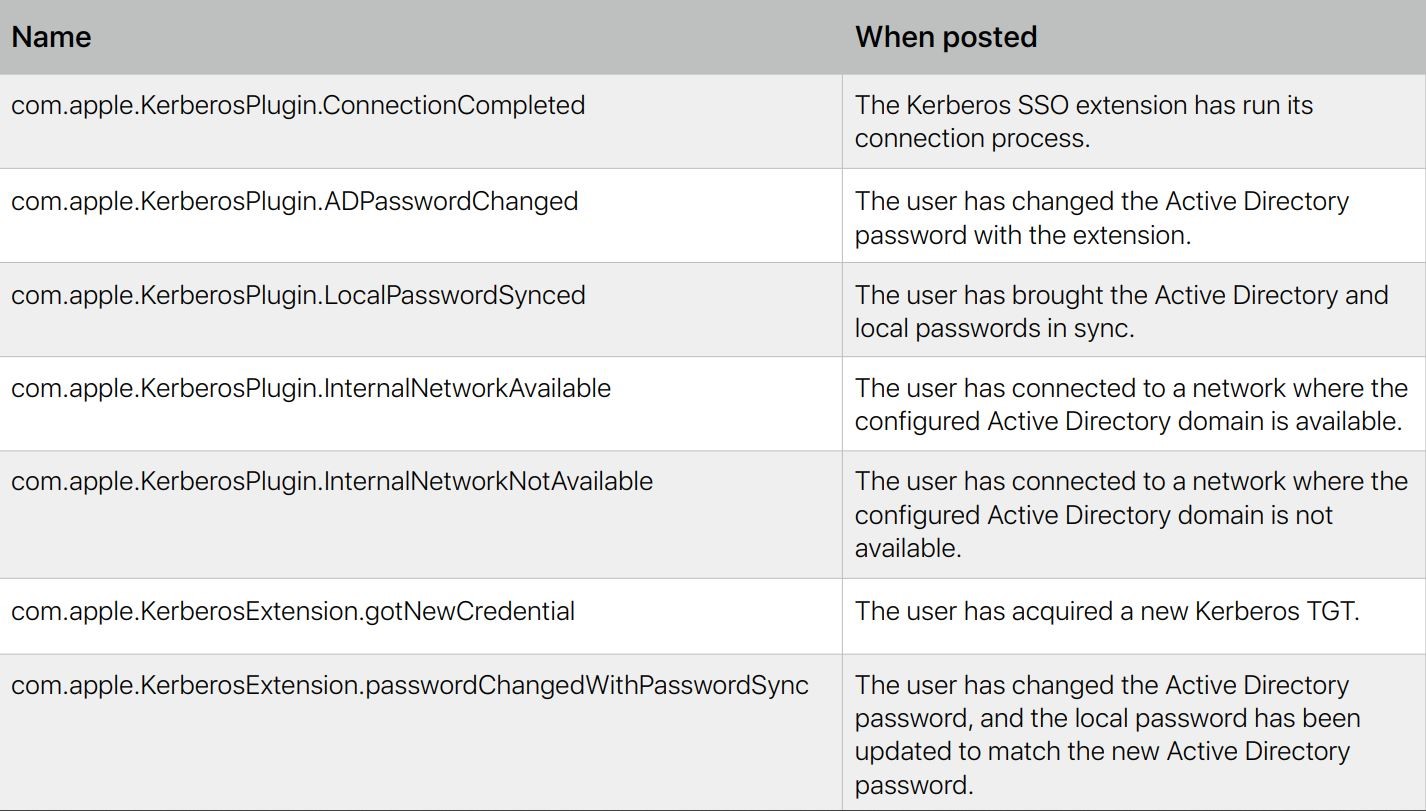
Kerberos Extension Command-line support (Mac ) : If you want to access helpful information and have more control over the Kerberos Single Sign-on extension, you can use a command-line tool called app-sso . This tool can perform functions such as initiating a sign-in, password change, and sign-out. You can also use app-sso to print information, which can be uploaded to your MDM solution.
Mobile Accounts (Mac ) : As we covered earlier, Apple recommends using the Kerberos Single Sign-on extension with a local account. However, if you still choose to use mobile accounts with the Kerberos extension, you must be aware that, according to Apple's Kerberos guide:
If you use the Kerberos SSO extension to change your Active Directory password and you’re logged in to your Mac with the same user account you’re using with the Kerberos SSO extension, password changes function as they do from the Users & Groups preference pane. But if you perform an external password change—meaning you change your password on a website, or your help desk resets it—the Kerberos SSO extension can’t bring your mobile account password back in sync with your Active Directory password. Using a password change URL with the Kerberos extension and a mobile account is unsupported.
Quote source: apple.com/business
Domain-realm mapping : While Apple’s operating systems can almost always determine domain-realm mapping, you may need to define a custom domain-realm map if your Kerberos realm authenticates with a resource using a different domain. You can define your domain-realm map in the configuration profile.
Using the Kerberos Single Sign-on extension requires building a configuration profile and delivering the profile to your devices using an MDM solution. On macOS, manually adding the profile isn’t supported – it requires user-approved MDM enrollment and installation in the System scope. In this section, we’ll walk you through the process of building the configuration profile and completing the user setup process.
How to Build a Kerberos SSO Extension Configuration Profile:
Here at Kandji, we built a new SSO Extension Profile with built-in support for the Kerberos single sign-on extension. Using Kandji’s SSO Extension Profile takes the manual work out of creating a Kerberos extension.
Kandji’s SSO Extension Profile also includes an easy-to-use interface, so you don’t have to create and upload a plist file to fill in all the Kerberos keys and options. Kandji supports all the Kerberos options we discussed earlier in this post. Here’s a sample of what it looks like:
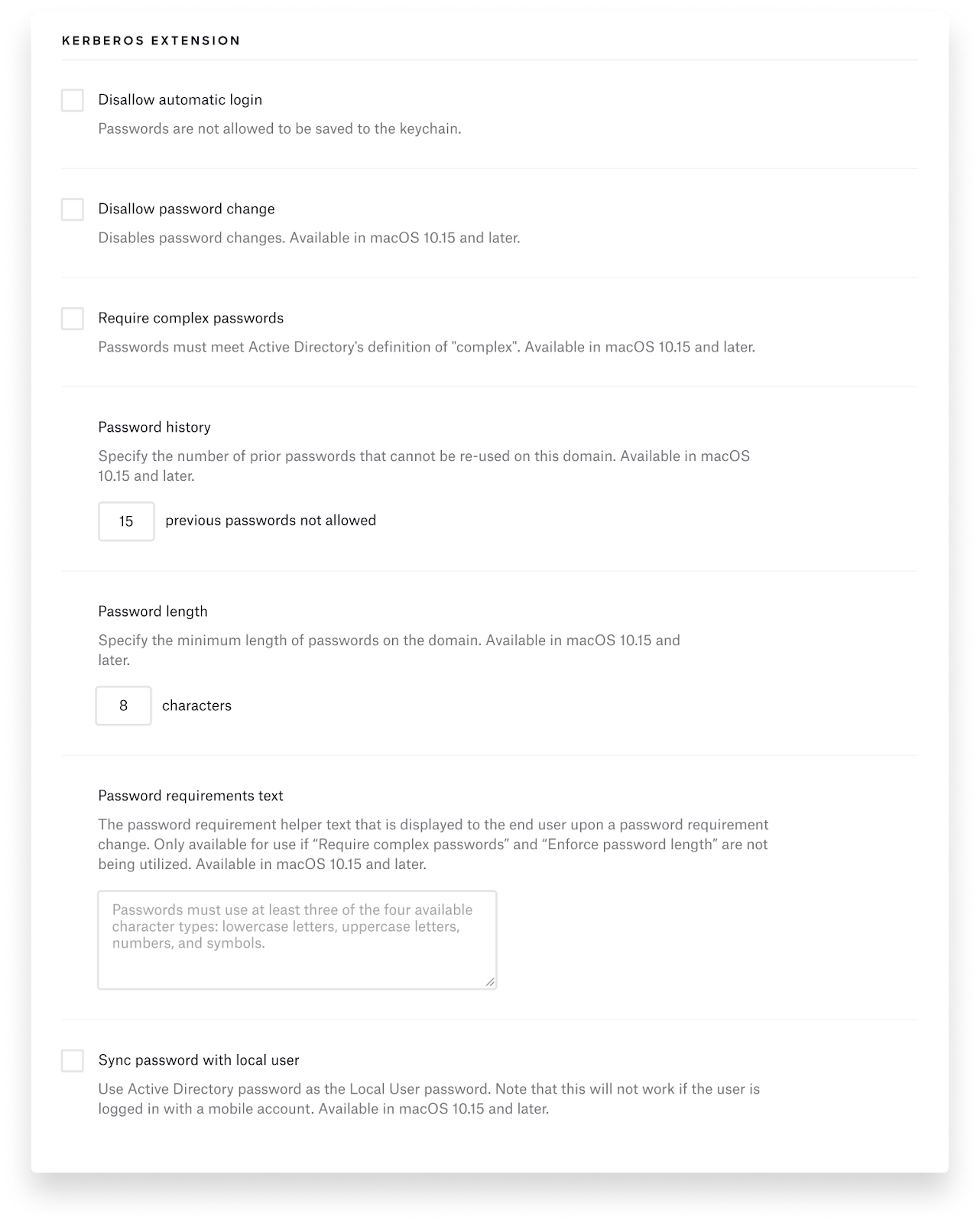
This makes it easy for IT administrators to use Apple’s new Extensible Enterprise SSO capabilities. To learn how to take advantage of this new profile, read our SSO Extension Profile support article .
iOS and iPadOS User Setup
- Connect Your Device: Connect your device to a network where your organization’s Active Directory domain is available.
- Access a Platform that Supports Kerberos Authentication : Open a Safari website that supports Kerberos authentication, or launch an app that supports Kerberos authentication.
- Sign in to the Platform : Enter your Kerberos or Active Directory login credentials to sign in to the platform. Answer the prompt asking if you want to sign in automatically. Next, select Sign In.
After a moment, your website or app will load. If you chose to automatically log in to the Kerberos Single Sign-on extension, you won’t have to enter your credentials until you change your password. If you didn’t choose to sign in automatically, you will need to log in again once your Kerberos credential expires. This usually takes 10 hours.
macOS User Setup
1. Authenticate to the Kerberos SSO extension : You can access a platform that supports Kerberos authentication for macOS in several ways:
- If your Mac is connected to the network where your Active Directory domain is available, you’ll be prompted to authenticate after the Extensible SSO configuration profile is installed.
- If you’re using a Safari website or app that accepts Kerberos authentication for macOS, you’ll be prompted to authenticate.
- If you connect your Mac to a network where your Active Directory is available, you’ll be prompted to authenticate.
- If you select the Kerberos SSO extension menu extra, you can click Sign In to authenticate.
2. Enter Login Credentials : Once the authentication prompt appears, you’ll need to enter your Active Directory username and password. Once this is completed, answer the prompt asking if you want to sign in automatically. Next, select Sign In.
Just like the iOS and iPadOS setup process, if you chose to log in to the Kerberos Single Sign-on extension automatically, you won’t have to enter your credentials until you change your password. If you didn’t choose to sign in automatically, you will need to log in again once your Kerberos credential expires. This usually takes 10 hours.
On macOS, you’ll receive a notification if your password is close to expiring. To change your password, simply click on this notification and begin the password change process. If you enabled the password sync function that we discussed earlier, you may need to enter your Active Directory and local passwords, then click OK to sync your passwords.
What’s New With the macOS Big Sur Kerberos Extension ?
At WWDC 2020 , Apple announced some exciting updates for the macOS Big Sur Kerberos Extension. In this section, we’re going to take a look at what’s new:
Menu-extra Updates : The menu-extra for macOS is now more representative of the state of the extension. It will show a “solid” key icon if all of the extension requirements are met. These requirements include having a credential, active network connection, functioning DNS, and an unexpired Kerberos ticket. If these requirements are unfulfilled, it will indicate what’s missing and show a “faded” key icon.
Customizable UI : Because all organizations don’t use the same name for their identities, Apple has included the ability to customize the label that’s shown in the Kerberos extension so it can match the name of your identity and organization. Apple also added the capability to add help text to guide users through login issues. This text is displayed beneath the login panel, so it can include contact information for your IT help desk so users can easily get the support they need.
Better Support for Per-App VPN : The Kerberos Single Sign-on extension will now trigger Per-App VPN for authentication-only requests. This lets you log in without manually triggering the VPN or having a separate network request. On macOS, the extension also supports app-to-per-app VPN.
User-Channel Support for Certificate-Based Kerberos or PKINIT : Referencing user-level certificate identities in a system-level scoped profile has always been available while configuring the Kerberos extension. However, with Apple’s latest improvement will make it much easier for MDM vendors to bundle configurations and certificates together.
More Control Over First Login Experience : This new feature will delay the first login prompt until the first authentication challenge is received or until an administrator enables it.

See Kandji in Action
Experience Apple device management and security that actually gives you back your time.
Get Started Contact Us
Start Free Trial Contact Us
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Use the Microsoft Enterprise SSO plug-in on iOS/iPadOS devices
- 6 contributors
The Microsoft Enterprise SSO plug-in provides single sign-on (SSO) to apps and websites that use Microsoft Entra ID for authentication, including Microsoft 365. This plug-in uses the Apple single sign-on app extension framework. It reduces the number of authentication prompts users get when using devices managed by Mobile Device Management (MDM), including any MDM that supports configuring SSO profiles.
Once set up, apps that support the Microsoft Authentication Library (MSAL) automatically take advantage of the Microsoft Enterprise SSO plug-in. Apps that don't support MSAL can be allowed to use the extension, including browsers like Safari and apps that use Safari web view APIs. Just add the application bundle ID or prefix to the extension configuration.
For example, to allow a Microsoft app that doesn't support MSAL, add com.microsoft. to the AppPrefixAllowList property. Be careful with the apps you allow, they'll be able to bypass interactive sign-in prompts for the signed in user.
For more information, see Microsoft Enterprise SSO plug-in for Apple devices - apps that don't use MSAL .
Announced in March 2024, Microsoft Entra ID will be moving away from Apple’s Keychain for storing device identity keys. Starting in Q3 2026, all new device registrations will use Apple’s Secure Enclave by default. For more information see Microsoft Enterprise SSO plug-in for Apple devices .
This article applies to:
This article shows how to deploy the Microsoft Enterprise SSO plug-in for iOS/iPadOS Apple devices with Intune, Jamf Pro, and other MDM solutions.
Prerequisites
To use the Microsoft Enterprise SSO plug-in on iOS/iPadOS devices:
The device is managed by Intune.
The device must support the plug-in:
- iOS/iPadOS 13.0 and newer
The Microsoft Authenticator app must be installed on the device.
Users can install the Microsoft Authenticator app manually. Or, admins can deploy the app using Intune. For information on how to install the Microsoft Authenticator app, go to Manage Apple volume-purchased apps .
The device is managed by Jamf Pro.
Users can install the Microsoft Authenticator app manually. Or, admins can deploy the app using Jamf Pro. For a list of options on how to install the Microsoft Authenticator app, go to Managing macOS installers using Jamf Pro (opens Jamf Pro's web site).
Jamf Pro and Intune integration for device compliance is not required to use the SSO app extension.
- The device is managed by a mobile device management (MDM) provider solution.
- The MDM solution must support configuring Single Sign-on MDM payload settings for Apple devices with a device policy.
- The Microsoft Authenticator app must be installed on the device. Users can install the Microsoft Authenticator app manually. Or, admins can deploy the app using an MDM policy.
On iOS/iPadOS devices, Apple requires that the SSO app extension and the Microsoft Authenticator app be installed. Users don't need to use or configure the Microsoft Authenticator app, it just needs to be installed on the device.
Microsoft Enterprise SSO plug-in vs. Kerberos SSO extension
When you use the SSO app extension, you use the SSO or Kerberos Payload Type for authentication. The SSO app extension is designed to improve the sign-in experience for apps and websites that use these authentication methods.
The Microsoft Enterprise SSO plug-in uses the SSO Payload Type with Redirect authentication. The SSO Redirect and Kerberos extension types can both be used on a device at the same time. Be sure to create separate device profiles for each extension type you plan to use on your devices.
To determine the correct SSO extension type for your scenario, use the following table:
For more information on the single sign-on extension, go to Single sign-on app extension .
Create a single sign-on app extension configuration profile
In the Microsoft Intune admin center , create a device configuration profile. This profile includes the settings to configure the SSO app extension on devices.
Sign in to the Microsoft Intune admin center .
Select Devices > Configuration > Create .
Enter the following properties:
- Platform : Select iOS/iPadOS .
- Profile type : Select Templates > Device features .
Select Create :

In Basics , enter the following properties:
- Name : Enter a descriptive name for the policy. Name your policies so you can easily identify them later. For example, a good policy name is iOS: Microsoft Enterprise SSO plug-in .
- Description : Enter a description for the policy. This setting is optional, but recommended.
Select Next .
In Configuration settings , select Single sign-on app extension , and configure the following properties:
SSO app extension type : Select Microsoft Entra ID .

Enable shared device mode :
Not configured : Intune doesn't change or update this setting.
For most scenarios, including Shared iPad, personal devices, and devices with or without user affinity, select this option.
Yes : Select this option only if the targeted devices are using Microsoft Entra shared device mode. For more information, go to Shared device mode overview .
App bundle ID : Enter a list of bundle IDs for apps that don't support MSAL and are allowed to use SSO. For more information, go to Applications that don't use MSAL .
Additional configuration : To customize the end user experience, you can add the following properties. These properties are the default values used by the Microsoft SSO Extension, but they can be customized for your organization needs:
For more information on these properties, and other properties you can configure, see Microsoft Enterprise SSO plug-in for Apple devices .
When you're done configuring the settings and are allowing Microsoft & Apple apps, then the settings look similar to the following values in your Intune configuration profile:

Continue creating the profile, and assign the profile to the users or groups that will receive these settings. For the specific steps, go to Create the profile .
For guidance on assigning profiles, go to Assign user and device profiles .
When the device checks in with the Intune service, it will receive this profile. For more information, go to Policy refresh intervals .
To check that the profile deployed correctly, in the Intune admin center, go to Devices > Configuration > select the profile you created and generate a report:

In the Jamf Pro portal, you create a Computer or Device configuration profile. This profile includes the settings to configure the SSO app extension on devices.
Sign in to the Jamf Pro portal.
To create an iOS/iPadOS profile, select Devices > Configuration > New :

In Name , enter a descriptive name for the policy. Name your policies so you can easily identify them later. For example, a good policy name is: iOS/iPadOS: Microsoft Enterprise SSO plug-in .
In the Options column, scroll down and select Single Sign-On Extensions > Add :

- Payload Type : Select SSO .
- Extension Identifier : Enter com.microsoft.azureauthenticator.ssoextension .
- Team Identifier : No value is needed, leave the field blank.
- Sign-On Type : Select Redirect .
- https://login.microsoftonline.com
- https://login.microsoft.com
- https://sts.windows.net
- https://login.partner.microsoftonline.cn
- https://login.chinacloudapi.cn
- https://login.microsoftonline.us
- https://login-us.microsoftonline.com

In Custom Configuration , you define other required properties. Jamf Pro requires that these properties are configured using an uploaded PLIST file. To see the full list of configurable properties, go to Microsoft Enterprise SSO plug-in for Apple devices documentation .
The following example is a recommended PLIST file that meets the needs of most organizations:

These PLIST settings configure the following SSO Extension options. These properties are the default values used by the Microsoft SSO Extension, but they can be customized for your organization needs:
Select the Scope tab. Enter the computers or devices that should be targeted to receive the SSO Extension MDM profile.
Select Save .
When the device checks in with the Jamf Pro service, it receives the profile.
In the MDM portal, create a device configuration profile. This profile includes the settings to configure the SSO app extension on devices.
Sign in to the MDM portal.
Create a new device configuration profile.
Select a Single Sign-On Extensions or SSO extension option. The name varies depending on the MDM solution you're using.
Optionally, you can configure other properties. These properties are the default values used by the Microsoft SSO Extension, but they can be customized for your organization needs:
Assign the new policy to the devices that should be targeted to receive the SSO Extension MDM profile.
When the device checks in with the MDM service, it receives this profile.
End user experience

If you're not deploying the Microsoft Authenticator app using an app policy, then users must install it manually. Users don't need to use the Authenticator app, it just needs to be installed on the device.
Users sign in to any supported app or website to bootstrap the extension. Bootstrap is the process of signing in for the first time, which sets up the extension.
After users sign in successfully, the extension is automatically used to sign in to any other supported app or website.
You can test single sign-on by opening Safari in private mode (opens Apple's web site) and opening the https://portal.office.com site. No username and password will be required.
Learn more about how the SSO plug-in works and how to troubleshoot the Microsoft Enterprise SSO Extension with the SSO troubleshooting guide for Apple devices .
For information about the Microsoft Enterprise SSO plug-in, go to Microsoft Enterprise SSO plug-in for Apple devices .
For information from Apple on the single sign-on extension payload, go to single sign-on extensions payload settings (opens Apple's web site).
For information on troubleshooting the Microsoft Enterprise SSO Extension, go to Troubleshooting the Microsoft Enterprise SSO Extension plugin on Apple devices .
Was this page helpful?
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources
- How to Use Kerberos on macOS
The Kerberos subsystem has been included in macOS since its initial launch in March 2001. It has evolved along with macOS over time.
At Stanford your SUNetID is your Kerberos identity. They are one and the same.
Kerberos files
The files for working with Kerberos are located in the folder /usr/bin. The primary binary files are:
- The command to authenticate to the Kerberos system: /usr/bin/kinit <SUNetID> . This is also referred to as “acquiring a TGT or ticket-granting ticket."
- The command to display currently held TGTs: /usr/bin/klist .
- The command to delete current TGTs: /usr/bin/kdestroy .
- The command to change your Kerberos password, /usr/bin/kpasswd , is included in the Apple Kerberos system but is not used at Stanford. To change your Kerberos password go to Account Manager .
Kerberos is configured for Stanford in a file that is user-installed in /Library/Preferences/edu.mit.Kerberos. It's a somewhat non-standard file name that has been a part of macOS since the beginning. Learn more about Kerberos on macOS and Kerberos at Stanford .
How to work with Kerberos
There are two methods for working with Kerberos authentication on macOS:
- The traditional method of working from the command line in Terminal.app
- Using the included, but hard to find, Ticket Viewer.app.
Both methods can be used for the basic tasks of authentication to Kerberos.
This document describes the basic Kerberos-related tasks on both of those tools.
Instructions
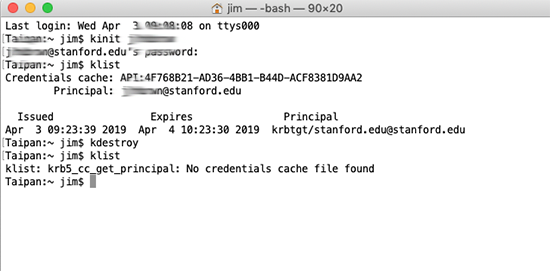
Terminal.app instructions.
This is the traditional method for managing Kerberos credentials, because Kerberos pre-dates most modern graphical operating systems. Each of the four commands listed in the Overview above are manually entered into a terminal window and executed.
Ticket Viewer.app instructions
This app is part of the Kerberos subsystem that is included in macOS by Apple. It can be found at: /System/Library/CoreServices/Ticket\ Viewer.app
Ticket Viewer is a graphical user interface for the Kerberos system and features buttons for each of the four commands listed in the Overview above. A Ticket Viewer shortcut can be added to the Dock by dragging the app from Finder to the desired location on the Dock. When launched, the user is presented with this view:
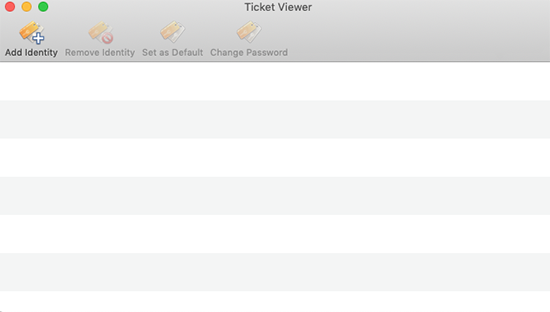
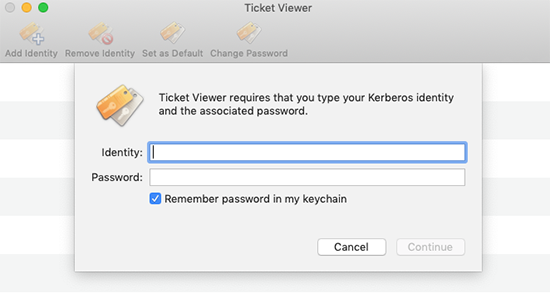
To authenticate (obtain a TGT) click the Add Identity button. A drop-down dialog box for entering your SUNetID and password is displayed.
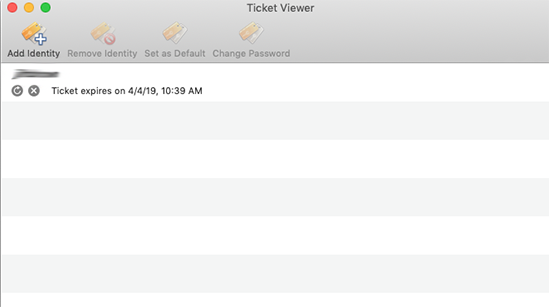
After successful authentication you will see the SUNetID and an expiration date/time.
Auristor AFS client instructions
If the Auristor AFS client for Mac is installed, there will be an addition to System Preferences. This Preference Pane contains options and controls for managing and using Kerberos as well as AFS.
When you launch the Preference Pane you will be presented with this screen:
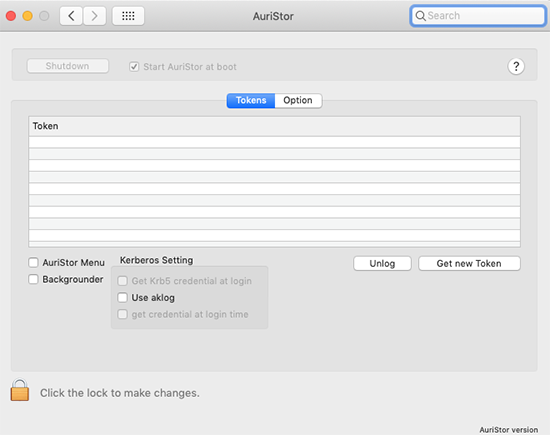
To use this Preference Pane to manage Kerberos, select the checkboxes for Backgrounder and Use aklog .
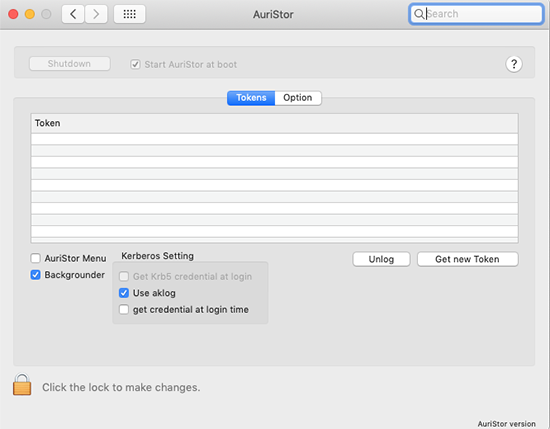
Select the Get new Token button to display a Kerberos authentication dialog box. Enter your SUNetID and Password and an entry will be displayed in the Tokens List.
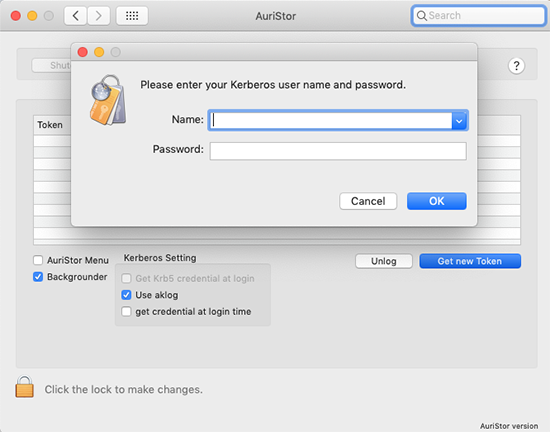
At this point you have successfully acquired a Kerberos TGT as well as an AFS token.
Essential Stanford Software
- Install Kerberos for Windows
- Install Kerberos Commander for Mac
- Microsoft Office
- Microsoft Project Professional
- Microsoft Visio Professional
- AFS at Stanford
- SecureCRT + SecureFX
- Windows Eraser
- Stanford Software Removal Guide
- Explore all services
- Cloud Solutions Q&As
- Get started with IT
- Practice secure computing
- Work Anywhere Guide
- Find answers
- Request something
- View system and project status
- Browser recommendations
- Tech Resources & Support (for students)
University IT
- Organization chart
- Current job openings
- Communities of Practice
- UIT Community (UIT staff only)
UIT Web Editors

- Stanford Home
- Maps & Directions
- Search Stanford
- Emergency Info
- Terms of Use
- Non-Discrimination
- Accessibility
© Copyright Stanford University . Stanford , California 94305 .
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
How can Safari do SPNEGO authentication using default kerberos ticket?
We have a Web site (out intranet site) that uses pass though authentication and signs people in automatically. This application works seamlessly when using a Windows machine. All of our Windows machines are Windows 7 64 bit. We have several Mac OS machines on site and would like to have the Macs also sign people in automatically. They are using AD to sign people in so I am thinking there is a way to make this work.
The Macs are version 10.7 and 10.8. Neither work. It comes up with a log in box and if you enter in the Network name and password it does work and lets you in. I am wondering if there is a way to make that happen automatically. The web site was built using Word Press. Any help is greatly appreciated. Sorry if I have left out important information.
- authentication
2 Answers 2
They are using AD to sign people in so I am thinking there is a way to make this work.
Do you mean by this that users log into OS X using their AD username and password? If so, they may already have Kerberos credentials once they’re logged in. To check this, use the klist command from a terminal prompt; you should see something like:
If not, use kinit user@REALM from a command prompt to authenticate. The REALM will be the AD domain name. When it was based on MIT Kerberos, Apple’s Kerberos implementation would automatically bring up a GUI panel when a program needed Kerberos and the user was not authenticated; unfortunately when they switched to Heimdal they dropped this nice feature, and now you have to do it manually.
You may need other configuration as well to get this working depending on the environment, but this is required in any case, and this and the rest may just work if everything is set up conveniently (e.g. the KDCs are discoverable via the DNS, the web server principal name is determined properly from its DNS name with the default rules, etc.). If not, I can help you figure out what else needs to be done.
It is possible. I'm able to login to intranet sites secured with Negotiate WIS using Safari on a Mac without a login prompt.
I had to join my computer to the domain by adding a "Network Account Server" in System Preferences > Users & Groups > Login Options.
When I login using my Active Directory account I'm able to open secured sites in Safari w/o a prompt.
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged mac authentication ntlm ..
- The Overflow Blog
- Is GenAI the next dot-com bubble?
- Featured on Meta
- New Focus Styles & Updated Styling for Button Groups
- Upcoming initiatives on Stack Overflow and across the Stack Exchange network
- Google Cloud will be Sponsoring Super User SE
Hot Network Questions
- What does it mean that a language has a "effect system"?
- How do objects reach terminal velocity?
- Spacecraft rescued when they transmitted Morse code
- Why does no historian speak of the torn veil and how do we reconcile it with scripture?
- Finding food on the run
- Characterizing principal polarizations of abelian surfaces
- Latin minimal pairs, distinguished only by the length of the vowel in an unstressed non-last syllable
- What copyleft license could I use for a program that depends on non-free libraries?
- A Dangerous Asian Ruler
- Is it a cartesian product?
- Can a non-trivial continuous function "undo" the discontinuities of another function?
- How long would it take for nature to reclaim a completely abandoned city?
- 1 in 60 rule for VORs
- Evaluate the binomial integral
- How understandable is this statistical hypothesis?
- How can I blend 3 images in GIMP, where each image provides an equal HSV contribution?
- How can i fix my loose Towel Hanger that is sliding down makes the bar to fall
- Weave two lists, cycling if necessary
- Where can I get an earth-centric map of space?
- Is there a standard which requires a high voltage warning label on a PCB?
- Could a historic (1500- 1700 AD) bicycle stand rough terrain? If yes how?
- `\IfSubStr` in a tikz style
- How Do I Explain "Be Born"?
- Short story about a late night feline meeting

Configure Mac browsers for SSO
Although IWA SSO may work if you choose not to configure your browser, Okta recommends that you review the relevant information for your browser type and then configure your browser.
macOS Safari
IWA is enabled automatically in Safari on macOS. Make sure that the macOS host is a Windows domain member. For more information on how to add your macOS host to a Windows domain, refer to Apple Support documentation and search for articles on how to join your Mac to a network account server.
Mozilla Firefox
The following configuration permits Firefox to properly pass the Kerberos ticket with IWA, but Firefox still warns the user about the transition from an HTTPS page to an HTTP page. To resolve this issue, deploy IWA in HTTPS mode.
Firefox3.x and later displays a warning message requesting that you proceed with caution.
network.negotiate-auth.trusted-uris
The order does not matter if you enter more than one host name.
Okta recommends that you enter the fully qualified domain name (FQDN) of your IWA host servers. If you do not, you will also need to toggle the following values to TRUE:
- Right click the Value column for each of the above and toggle the value to True .
Google Chrome
IWA capability is enabled automatically in Chrome on OS/X, and just like on Windows, the capability is governed by an allowlist. If a site asks your browser to provide the Kerberos ticket, the browser only provides the ticket if the site is on the allowlist.
- Launch the Terminal application.
Replace [email protected] with your username and domain and then enter your password when prompted.
$ defaults write com.google.Chrome AuthServerAllowlist "*.example.com"
$ defaults write com.google.Chrome AuthNegotiateDelegateAllowlist "*.example.com"
Replace example.com with your domain.
For information on how to manage Chrome policies on macOS, refer to Google Support documentation and search for articles on AuthNegotiateDelegateAllowlist and AuthServerAllowlist .
Activate the Okta IWA Web agent
© 2024 Okta, Inc . All Rights Reserved. Various trademarks held by their respective owners.
Looks like no one’s replied in a while. To start the conversation again, simply ask a new question.
Safari and Kerberos
MacBook, Mac OS X (10.4.10)
Posted on Oct 21, 2007 9:34 AM
Loading page content
Page content loaded
There are no replies.
Apple Platform Deployment
- Intro to Apple platform deployment
- Intro to declarative device management
- Use declarative device management to manage Apple devices
- Intro to MDM profiles
- Intro to MDM payloads
- About device supervision
- Choose a deployment model
- Intro to Apple device enrollment types
- User Enrollment and MDM
- Device Enrollment and MDM
- Automated Device Enrollment and MDM
- Deploy Apple TV
- Deploy Apple Watch
- Deploy Apple Vision Pro
- Shared iPad overview
- Prepare Shared iPad
- Choose an MDM solution
- Intro to planning your MDM migration
- Configure your new MDM solution
- Reenroll devices in MDM
- Back up and restore devices
- Use standards-based services
- Deploy devices using Apple School Manager, Apple Business Manager, or Apple Business Essentials
- Configure devices
- Install apps with Apple Configurator
- Add Apple devices to Apple School Manager, Apple Business Manager, or Apple Business Essentials
- Configure your network for MDM
- Configure devices to work with APNs
- Prepare to use eSIMs with Apple devices
- Use MDM to deploy devices with cellular connections
- Support for private 5G and LTE networks
- Optimize your Wi-Fi networks
- Review aggregate throughput for Wi-Fi networks
- Intro to content caching
- Set up content caching
- Use DNS TXT records
- Advanced content caching settings
- Content caching from the command line
- Content caching metrics
- Set up a shared internet connection
- Intro to Apple identity services
- Platform SSO for macOS
- Enrollment SSO for iPhone and iPad
- Managed Apple IDs
- Service access with Managed Apple IDs
- iMessage and FaceTime
- Intro to single sign-on
- Kerberos SSO extension
- Integrate with Microsoft Entra ID
- Integrate with Microsoft Exchange
- Identify an iPhone, iPad, or Apple Vision Pro using Microsoft Exchange
- Integrate Mac computers with Active Directory
- Manage Setup Assistant
- Configure Setup Assistant panes in Apple TV
- Set up local macOS accounts
- Plan your configuration profiles
- Review MDM payloads
- Review MDM restrictions
- Review declarative configurations
- About software updates
- Test and defer software updates
- Use MDM to deploy software updates
- Intro to content distribution
- Content distribution methods
- Distribute Managed Apps
- Distribute Custom Apps
- Distribute Unlisted Apps
- Distribute proprietary in-house apps
- Distribute custom packages for Mac
- Bundle IDs for native iPhone and iPad apps
- Bundle IDs for native Apple TV apps
- Manage login items and background tasks on Mac
- How Apple devices join Wi-Fi networks
- Connect to 802.1X networks
- Wi-Fi roaming support
- Cisco network enhancements
- Wi-Fi specifications for Apple devices
- VPN overview
- Cisco IPsec VPN setup
- Use a VPN proxy and certificate configuration
- Use network relays
- Filter content
- Use AirPlay
- Intro to device management security
- Rapid Security Responses
- Lock and locate devices
- Erase devices
- Activation Lock
- Manage accessory access
- Enforce password policies
- Use persistent tokens
- Use built-in network security features
- Managed Device Attestation
- Intro to certificate management
- Distribute certificates
- Intro to smart card integration
- Supported smart card functions on iPhone and iPad
- Use a smart card on iPhone and iPad
- Supported smart card functions on Mac
- Use a smart card on Mac
- Configure a Mac for smart card–only authentication
- FileVault and smart card usage
- Advanced smart card options
- Startup security
- System and kernel extensions in macOS
- Intro to FileVault
- Use secure and bootstrap tokens
- Manage FileVault with MDM
- Mac app security enhancements
- User Enrollment MDM information
- Device Enrollment MDM payload list
- Automated Device Enrollment MDM payload list
- Payload list for iPhone and iPad
- Payload list for Mac
- Payload list for Apple TV
- Payload list for Apple Watch
- Payload list for Apple Vision Pro
- Payload list for Shared iPad
- Restrictions for iPhone and iPad
- Restrictions for Mac
- Restrictions for Apple TV
- Restrictions for Apple Watch
- Restrictions for Apple Vision Pro
- Restrictions for supervised devices
- MDM command list
- MDM settings command options list
- Device information queries
- Device network information queries
- Operating system queries
- Installed app queries
- Security queries
- Declarative status reports
- Accessibility payload settings
- Active Directory Certificate payload settings
- AirPlay payload settings
- AirPlay Security payload settings
- AirPrint payload settings
- App Lock payload settings
- Associated Domains payload settings
- Automated Certificate Management Environment (ACME) payload settings
- Autonomous Single App Mode payload settings
- Calendar payload settings
- Cellular payload settings
- Cellular Private Network payload settings
- Certificate Preference payload settings
- Certificate Revocation payload settings
- Certificate Transparency payload settings
- Certificates payload settings
- Conference Room Display payload settings
- Contacts payload settings
- Content Caching payload settings
- Directory Service payload settings
- DNS Proxy payload settings
- DNS Settings payload settings
- Dock payload settings
- Domains payload settings
- Energy Saver payload settings
- Exchange ActiveSync (EAS) payload settings
- Exchange Web Services (EWS) payload settings
- Extensible Single Sign-on payload settings
- Extensible Single Sign-on Kerberos payload settings
- Extensions payload settings
- FileVault payload settings
- Finder payload settings
- Firewall payload settings
- Fonts payload settings
- Global HTTP Proxy payload settings
- Google Accounts payload settings
- Home Screen Layout payload settings
- Identification payload settings
- Identity Preference payload settings
- Kernel Extension Policy payload settings
- LDAP payload settings
- Lights Out Management payload settings
- Lock Screen Message payload settings
- Login Window payload settings
- Managed Login Items payload settings
- Mail payload settings
- Wi-Fi settings
- Ethernet settings
- WEP, WPA, WPA2, WPA2/WPA3 settings
- Dynamic WEP, WPA Enterprise, and WPA2 Enterprise settings
- EAP settings
- HotSpot 2.0 settings
- Legacy Hotspot settings
- Cisco Fastlane settings
- Network Proxy Configuration settings
- Network Usage Rules payload settings
- Notifications payload settings
- Parental Controls payload settings
- Passcode payload settings
- Printing payload settings
- Privacy Preferences Policy Control payload settings
- Relay payload settings
- SCEP payload settings
- Security payload settings
- Setup Assistant payload settings
- Single Sign-on payload settings
- Smart Card payload settings
- Subscribed Calendars payload settings
- System Extensions payload settings
- System Migration payload settings
- Time Machine payload settings
- TV Remote payload settings
- VPN settings overview
- AppLayerVPN payload settings
- IKEv2 settings
- IPsec settings
- L2TP settings
- VPN Proxy settings
- Web Clips payload settings
- Web Content Filter payload settings
- Xsan payload settings
- Declarative app configuration settings
- Authentication credentials and identity asset settings
- Calendar declarative settings
- Certificates declarative configuration
- Contacts declarative configuration
- Exchange declarative configuration
- Google Accounts declarative configuration
- LDAP declarative configuration
- Legacy interactive profile declarative configuration
- Legacy profile declarative configuration
- Mail declarative configuration
- Passcode declarative configuration
- Passkey Attestation declarative configuration
- Screen Sharing declarative configuration
- Service configuration files declarative configuration
- Software Update declarative configuration
- Subscribed Calendars declarative configuration
- Join AppleSeed for IT
- AppleCare support
- Professional services
- Deployment and management training
- Apple Consultants Network
- Apple web resources
- Document revision history
Extensible Single Sign-on Kerberos MDM payload settings for Apple devices
Use the Extensible Single Sign-on Kerberos payload to configure a single sign-on extension on iPhone, iPad, and Mac devices enrolled in a mobile device management (MDM) solution.
This extension is for use by organizations to deliver a seamless experience as users sign in to apps and websites. When this payload is properly configured using MDM, the user authenticates once, then gains access to subsequent native apps and websites automatically. Some of the features that can be used with the Extensible Single Sign-on Kerberos payload are:
Authentication with user name and password or for example, smart cards
Per App VPN
Password expiration notifications
Password changes
Because this payload can be used on the user channel, MDM vendors can bundle per-user settings for SSO—for example, the user-level certificate identities for use with certificate-based Kerberos or PKINIT.
Supported approval method: Requires user approval .
Supported installation method: Requires an MDM solution to install.
Supported payload identifier: com.apple.extensiblesso(kerberos)
Supported operating systems and channels: iOS, iPadOS, Shared iPad user, macOS device, macOS user, visionOS 1.1 .
Supported enrollment types: User Enrollment, Device Enrollment, Automated Device Enrollment.
Duplicates allowed: True—more than one Extensible Single Sign-on Kerberos payload can be delivered to a user or device.
You can use the settings in the table below with the Extensible Single Sign-on Kerberos payload.
Note: Each MDM vendor implements these settings differently. To learn how various Extensible Single Sign-on Kerberos settings are applied to your devices and users, consult your MDM vendor’s documentation.
Kerberos authentication on a Mac OS X workstation with Chrome
Kerberos authentication allows your computer to log into certain services automatically without you having to enter (and re-enter) your password (it's a SSO—single sign-on—service). Kerberos v5 is baked into Windows and Internet Explorer and works great with many LDAP-enabled services (for example, Drupal's LDAP module allows includes a submodule for SSO support).
Kerberos is built into Mac OS X as well, but isn't as simple to use and configure with Chrome and FireFox as it is with Explorer on a Windows workstation. You need to do two things before you can use Kerberos for authentication in Chrome/FireFox:
- Create a Kerberos ticket with the Ticket Viewer application (/System/Library/CoreServices/Ticket Viewer) or via the command line ( kinit [email protected] , then enter your password). See this article for more detailed instructions.
- Configure Chrome's whitelist to allow authentication against any domains you will be using (along with the domain you used with kinit above). In the Terminal, run the following commands: $ defaults write com.google.Chrome AuthServerWhitelist "*.example.com" $ defaults write com.google.Chrome AuthNegotiateDelegateWhitelist "*.example.com"
> **2019 Update**: For newer versions of Chrome (~68+), you might need to use the same commands above, but without the double quotes.
In all the above examples, replace 'example.com' with your domain. Also, for the Chrome defaults, you can add multiple domains with commas separating each. The asterisk is a wildcard, so any subdomain would work.
Safari works out of the box if you've created a Kerberos ticket as outlined in step 1; FireFox just needs a couple settings configured on the about:config page.
Further reading
- Apache Kerberos Authentication and basic authentication fallback
- Why I'm Switching Back from Chrome to Safari 5.0
- Switched back to Safari from Chrome... Again
- Add new comment
My reading tells me that Safari doesn't support kerberos ticket forwarding. Any thoughts?
https://discussions.apple.com/message/21104706#24471966
Thank you! I've been struggling for a month now to make Chrome work with our Sophos firewall. No extensions worked. Your method however worked on the first try.
What about Firefox? What are the couple of settings?
Go to about:config and add your [email protected] to network.negotiate-auth.trusted-uris. Field is comma delimited. The user.js file can auto-set these preferences which is under the users' Mozilla profile.
Thanks. This was very helpful and got my Chrome auth via Kerberos working.
Can you provide an example of the syntax for multiple domains? I can't seem to get it quite right.
The syntax is "*.example.com,*.another.net", so just comma separated. This at least works for me. Most important part, though, is that you will have to restart Google Chrome after making this change.
Great information! At my company we just adjusted to "does not work with Chrome". But now! Thanks to you! Everything works!
If you are using Chromium you need to use "org.chromium.Chromium" as a key to write to. Not really easy to find.
It seems this may not work anymore on newer version of Chrome? Can anyone else confirm?
Yeah I am struggling with this solution. Maybe has changed since
I figured it out for newer versions.
Its same commands but without the "quotes"
defaults write com.google.Chrome AuthServerWhitelist *.domain.com defaults write com.google.Chrome AuthNegotiateDelegateWhitelist *.domain.com
Thanks, I've added a note in the post about this!
Hi, since Chrome version 101 the two config names have been replaced: AuthServerWhitelist -> AuthServerAllowlist AuthNegotiateDelegateWhitelist -> AuthNegotiateDelegateAllowlist
I just tested this and it fixed an issue that I've been struggling with for 2 weeks! Old parameters don't work but new ones work like a charm! Thank you!
so i ran the defaults ( both ) and kinit... when i navigate to a page that needs authentication in safari no problem, but when i try the same path in chrome i get: java.lang.NullPointerException net.sourceforge.spnego.SpnegoAuthenticator.doSpnegoAuth(SpnegoAuthenticator.java:463) net.sourceforge.spnego.SpnegoAuthenticator.authenticate(SpnegoAuthenticator.java:283) net.sourceforge.spnego.SpnegoHttpFilter.doFilter(SpnegoHttpFilter.java:229)
I am trying to delete the allow list but I'm getting Syntax errors.... works for chrome, not for edge. # defaults delete com.microsoft.Edge AuthServerAllowlist "*domain" Command line interface to a user's defaults. Syntax:
'defaults' [-currentHost | -host ] followed by one of the following:
read shows all defaults read shows defaults for given domain read shows defaults for given domain, key
read-type shows the type for the given domain, key
write writes domain (overwrites existing) write writes key for domain
rename renames old_key to new_key
delete deletes domain delete deletes key in domain
import writes the plist at path to domain import - writes a plist from stdin to domain export saves domain as a binary plist to path export - writes domain as an xml plist to stdout domains lists all domains find lists all entries containing word help print this help
is ( | -app | -globalDomain ) or a path to a file omitting the '.plist' extension
-string -data -int[eger] -float -bool[ean] (true | false | yes | no) -date -array ... -array-add ... -dict ... -dict-add ...
- Jamf Nation Community
SSOs Kerberos Apple/Microsoft
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Report Inappropriate Content
Posted on 07-22-2021 06:54 AM
Solved! Go to Solution.
07-22-2021 07:20 AM - edited 07-22-2021 07:26 AM
View solution in original post
Posted on 07-22-2021 10:50 AM
Posted on 07-27-2021 09:45 AM
- All forum topics
- Previous Topic
Posted on 07-22-2021 07:34 AM
Posted on 07-22-2021 02:38 PM
never-displayed

Turn Your Curiosity Into Discovery
Latest facts.
11 Facts About National Love Your Produce Manager Day April 2nd
10 Facts About National Clean Out Your Medicine Cabinet Day April 19th
40 facts about elektrostal.
Written by Lanette Mayes
Modified & Updated: 02 Mar 2024
Reviewed by Jessica Corbett

Elektrostal is a vibrant city located in the Moscow Oblast region of Russia. With a rich history, stunning architecture, and a thriving community, Elektrostal is a city that has much to offer. Whether you are a history buff, nature enthusiast, or simply curious about different cultures, Elektrostal is sure to captivate you.
This article will provide you with 40 fascinating facts about Elektrostal, giving you a better understanding of why this city is worth exploring. From its origins as an industrial hub to its modern-day charm, we will delve into the various aspects that make Elektrostal a unique and must-visit destination.
So, join us as we uncover the hidden treasures of Elektrostal and discover what makes this city a true gem in the heart of Russia.
Key Takeaways:
- Elektrostal, known as the “Motor City of Russia,” is a vibrant and growing city with a rich industrial history, offering diverse cultural experiences and a strong commitment to environmental sustainability.
- With its convenient location near Moscow, Elektrostal provides a picturesque landscape, vibrant nightlife, and a range of recreational activities, making it an ideal destination for residents and visitors alike.
Known as the “Motor City of Russia.”
Elektrostal, a city located in the Moscow Oblast region of Russia, earned the nickname “Motor City” due to its significant involvement in the automotive industry.
Home to the Elektrostal Metallurgical Plant.
Elektrostal is renowned for its metallurgical plant, which has been producing high-quality steel and alloys since its establishment in 1916.

Boasts a rich industrial heritage.
Elektrostal has a long history of industrial development, contributing to the growth and progress of the region.
Founded in 1916.
The city of Elektrostal was founded in 1916 as a result of the construction of the Elektrostal Metallurgical Plant.
Located approximately 50 kilometers east of Moscow.
Elektrostal is situated in close proximity to the Russian capital, making it easily accessible for both residents and visitors.
Known for its vibrant cultural scene.
Elektrostal is home to several cultural institutions, including museums, theaters, and art galleries that showcase the city’s rich artistic heritage.
A popular destination for nature lovers.
Surrounded by picturesque landscapes and forests, Elektrostal offers ample opportunities for outdoor activities such as hiking, camping, and birdwatching.
Hosts the annual Elektrostal City Day celebrations.
Every year, Elektrostal organizes festive events and activities to celebrate its founding, bringing together residents and visitors in a spirit of unity and joy.
Has a population of approximately 160,000 people.
Elektrostal is home to a diverse and vibrant community of around 160,000 residents, contributing to its dynamic atmosphere.
Boasts excellent education facilities.
The city is known for its well-established educational institutions, providing quality education to students of all ages.
A center for scientific research and innovation.
Elektrostal serves as an important hub for scientific research, particularly in the fields of metallurgy, materials science, and engineering.
Surrounded by picturesque lakes.
The city is blessed with numerous beautiful lakes, offering scenic views and recreational opportunities for locals and visitors alike.
Well-connected transportation system.
Elektrostal benefits from an efficient transportation network, including highways, railways, and public transportation options, ensuring convenient travel within and beyond the city.
Famous for its traditional Russian cuisine.
Food enthusiasts can indulge in authentic Russian dishes at numerous restaurants and cafes scattered throughout Elektrostal.
Home to notable architectural landmarks.
Elektrostal boasts impressive architecture, including the Church of the Transfiguration of the Lord and the Elektrostal Palace of Culture.
Offers a wide range of recreational facilities.
Residents and visitors can enjoy various recreational activities, such as sports complexes, swimming pools, and fitness centers, enhancing the overall quality of life.
Provides a high standard of healthcare.
Elektrostal is equipped with modern medical facilities, ensuring residents have access to quality healthcare services.
Home to the Elektrostal History Museum.
The Elektrostal History Museum showcases the city’s fascinating past through exhibitions and displays.
A hub for sports enthusiasts.
Elektrostal is passionate about sports, with numerous stadiums, arenas, and sports clubs offering opportunities for athletes and spectators.
Celebrates diverse cultural festivals.
Throughout the year, Elektrostal hosts a variety of cultural festivals, celebrating different ethnicities, traditions, and art forms.
Electric power played a significant role in its early development.
Elektrostal owes its name and initial growth to the establishment of electric power stations and the utilization of electricity in the industrial sector.
Boasts a thriving economy.
The city’s strong industrial base, coupled with its strategic location near Moscow, has contributed to Elektrostal’s prosperous economic status.
Houses the Elektrostal Drama Theater.
The Elektrostal Drama Theater is a cultural centerpiece, attracting theater enthusiasts from far and wide.
Popular destination for winter sports.
Elektrostal’s proximity to ski resorts and winter sport facilities makes it a favorite destination for skiing, snowboarding, and other winter activities.
Promotes environmental sustainability.
Elektrostal prioritizes environmental protection and sustainability, implementing initiatives to reduce pollution and preserve natural resources.
Home to renowned educational institutions.
Elektrostal is known for its prestigious schools and universities, offering a wide range of academic programs to students.
Committed to cultural preservation.
The city values its cultural heritage and takes active steps to preserve and promote traditional customs, crafts, and arts.
Hosts an annual International Film Festival.
The Elektrostal International Film Festival attracts filmmakers and cinema enthusiasts from around the world, showcasing a diverse range of films.
Encourages entrepreneurship and innovation.
Elektrostal supports aspiring entrepreneurs and fosters a culture of innovation, providing opportunities for startups and business development.
Offers a range of housing options.
Elektrostal provides diverse housing options, including apartments, houses, and residential complexes, catering to different lifestyles and budgets.
Home to notable sports teams.
Elektrostal is proud of its sports legacy, with several successful sports teams competing at regional and national levels.
Boasts a vibrant nightlife scene.
Residents and visitors can enjoy a lively nightlife in Elektrostal, with numerous bars, clubs, and entertainment venues.
Promotes cultural exchange and international relations.
Elektrostal actively engages in international partnerships, cultural exchanges, and diplomatic collaborations to foster global connections.
Surrounded by beautiful nature reserves.
Nearby nature reserves, such as the Barybino Forest and Luchinskoye Lake, offer opportunities for nature enthusiasts to explore and appreciate the region’s biodiversity.
Commemorates historical events.
The city pays tribute to significant historical events through memorials, monuments, and exhibitions, ensuring the preservation of collective memory.
Promotes sports and youth development.
Elektrostal invests in sports infrastructure and programs to encourage youth participation, health, and physical fitness.
Hosts annual cultural and artistic festivals.
Throughout the year, Elektrostal celebrates its cultural diversity through festivals dedicated to music, dance, art, and theater.
Provides a picturesque landscape for photography enthusiasts.
The city’s scenic beauty, architectural landmarks, and natural surroundings make it a paradise for photographers.
Connects to Moscow via a direct train line.
The convenient train connection between Elektrostal and Moscow makes commuting between the two cities effortless.
A city with a bright future.
Elektrostal continues to grow and develop, aiming to become a model city in terms of infrastructure, sustainability, and quality of life for its residents.
In conclusion, Elektrostal is a fascinating city with a rich history and a vibrant present. From its origins as a center of steel production to its modern-day status as a hub for education and industry, Elektrostal has plenty to offer both residents and visitors. With its beautiful parks, cultural attractions, and proximity to Moscow, there is no shortage of things to see and do in this dynamic city. Whether you’re interested in exploring its historical landmarks, enjoying outdoor activities, or immersing yourself in the local culture, Elektrostal has something for everyone. So, next time you find yourself in the Moscow region, don’t miss the opportunity to discover the hidden gems of Elektrostal.
Q: What is the population of Elektrostal?
A: As of the latest data, the population of Elektrostal is approximately XXXX.
Q: How far is Elektrostal from Moscow?
A: Elektrostal is located approximately XX kilometers away from Moscow.
Q: Are there any famous landmarks in Elektrostal?
A: Yes, Elektrostal is home to several notable landmarks, including XXXX and XXXX.
Q: What industries are prominent in Elektrostal?
A: Elektrostal is known for its steel production industry and is also a center for engineering and manufacturing.
Q: Are there any universities or educational institutions in Elektrostal?
A: Yes, Elektrostal is home to XXXX University and several other educational institutions.
Q: What are some popular outdoor activities in Elektrostal?
A: Elektrostal offers several outdoor activities, such as hiking, cycling, and picnicking in its beautiful parks.
Q: Is Elektrostal well-connected in terms of transportation?
A: Yes, Elektrostal has good transportation links, including trains and buses, making it easily accessible from nearby cities.
Q: Are there any annual events or festivals in Elektrostal?
A: Yes, Elektrostal hosts various events and festivals throughout the year, including XXXX and XXXX.
Was this page helpful?
Our commitment to delivering trustworthy and engaging content is at the heart of what we do. Each fact on our site is contributed by real users like you, bringing a wealth of diverse insights and information. To ensure the highest standards of accuracy and reliability, our dedicated editors meticulously review each submission. This process guarantees that the facts we share are not only fascinating but also credible. Trust in our commitment to quality and authenticity as you explore and learn with us.
Share this Fact:
增强的虚拟应用程序和桌面启动体验
使用 Citrix Gateway 作为 IdP 域直通到 Citrix Workspace
使用 Azure Active Directory 作为 IdP 域直通到 Citrix Workspace
使用 Okta 作为 IdP 域直通到 Citrix Workspace
优化的 Microsoft Teams
Citrix Workspace 应用程序 Desktop Lock
Storebrowse
适用于 Workspace 的 Storebrowse
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。 免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica. (Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています. 免責事項
이 기사는 기계 번역되었습니다. 책임 부인
Este artigo foi traduzido automaticamente. (Aviso legal)
这篇文章已经过机器翻译. 放弃
Questo articolo è stato tradotto automaticamente. (Esclusione di responsabilità))
Translation failed!
Citrix Workspace 应用程序,包括域直通身份验证(单点登录或 SSON)、 智能卡以及 Kerberos 直通身份验证,可以配置各种不同类型的身份验证。
- 域直通(单点登录)身份验证
域直通(单点登录或 SSON)允许您向域进行身份验证,并且无需重新进行身份验证即可使用 Citrix Virtual Apps and Desktops 和 Citrix DaaS(以前称为 Citrix Virtual Apps and Desktops 服务)。
注意: 如果您在组策略对象模板中禁用了 Enable MPR notifications for the System (为系统启用 MPR 通知)策略,则 Windows 11 不支持域直通(单点登录)身份验证功能。 此功能在适用于 Windows 的 Citrix Workspace 应用程序版本 2012 及更高版本中提供。
启用后,域直通(单点登录)会缓存您的凭据,这样您就可以连接到其他 Citrix 应用程序,而不必每次都登录。请确保您的设备上仅运行符合公司政策的软件,以降低凭据泄露的风险。
当您登录 Citrix Workspace 应用程序时,您的凭据将随应用程序和桌面以及“开始”菜单设置一起传递到 StoreFront。配置单点登录后,您可以登录 Citrix Workspace 应用程序并启动虚拟应用程序和桌面会话,而不需要重新键入您的凭据。
所有 Web 浏览器都要求您使用组策略对象 (GPO) 管理模板来配置单点登录。有关使用组策略对象 (GPO) 管理模板配置单点登录的详细信息,请参阅 使用 Citrix Gateway 配置单点登录 。
您可以使用以下任意选项在进行全新安装或升级安装时配置单点登录:
注意: 在本文档中,术语域直通、单点登录和 SSON 可以互换使用。
在全新安装过程中配置单点登录
要在全新安装过程中配置单点登录,请执行以下步骤:
- StoreFront 上的配置。
- 在 Delivery Controller 上配置 XML 信任服务。
- 修改 Internet Explorer 设置。
- 安装具有单点登录功能的 Citrix Workspace 应用程序。
在 StoreFront 上配置单点登录
单点登录允许您对域进行身份验证,并使用来自相同域的 Citrix Virtual Apps and Desktops 和 Citrix DaaS,而不需要重新对每个应用程序或桌面进行身份验证。
使用 Storebrowse 实用程序添加应用商店时,您的凭据将随为您枚举的应用程序和桌面一起传递到 Citrix Gateway 服务器,包括“开始”菜单设置。配置单点登录后,可以添加应用商店、枚举应用程序和桌面以及启动所需的资源,而无需多次键入您的凭据。
根据 Citrix Virtual Apps and Desktops 部署,可以使用管理控制台在 StoreFront 上配置单点登录身份验证。
通过下表了解不同的用例及其各自的配置:
通过 Citrix Gateway 配置单点登录
使用组策略对象管理模板对 Citrix Gateway 启用单点登录。但是,您必须确保已在 Citrix Gateway 上启用基本身份验证和单因素(包含 1 个因素的 nFactor)身份验证。
- 通过运行 gpedit.msc 打开 Citrix Workspace 应用程序 GPO 管理模板。
- 在 计算机配置节点 下,转至 管理模板 > Citrix 组件 > Citrix Workspace > 用户身份验证 ,然后选择 通过 Citrix Gateway 实现 Single Sign-On 策略。
- 单击 应用 和 确定 。
重新启动 Citrix Workspace 应用程序以使所做的更改生效。
在 Delivery Controller 上配置 XML 信任服务
在 Citrix Virtual Apps and Desktops 和 Citrix DaaS 上,以管理员身份在 Delivery Controller 上运行以下 PowerShell 命令:
asnp Citrix* ; Set-BrokerSite -TrustRequestsSentToTheXmlServicePort $True
修改 Internet Explorer 设置
- 从控制面板启动 Internet 选项 。
单击 安全 > 本地 Internet ,然后单击 站点 。
此时将显示 本地 Intranet 窗口。
- 添加使用恰当的 HTTP 或 HTTPS 协议的 StoreFront FQDN 的 URL。
- 单击 安全 选项卡 > 本地 Intranet 。
- 单击 自定义级别 。此时将显示 安全设置 — 本地 Intranet 区域 窗口。
在 用户身份验证 窗格中,选择 使用当前用户名和密码自动登录 。
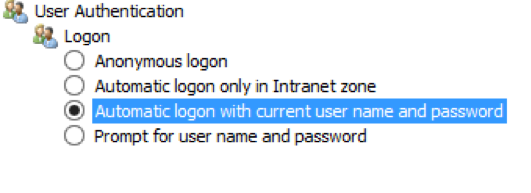
使用命令行接口配置单点登录
使用 /includeSSON 开关安装 Citrix Workspace 应用程序并重新启动 Citrix Workspace 应用程序以使所做的更改生效。
使用 GUI 配置单点登录
- 找到 Citrix Workspace 应用程序安装文件 ( CitrixWorkspaceApp.exe )。
- 双击 CitrixWorkspaceApp.exe 以启动安装程序。
- 在 启用单点登录安装 向导中,选择 启用单点登录 选项。
- 单击 下一步 ,然后按照提示完成安装。
您现在不需要输入用户凭据即可使用 Citrix Workspace 应用程序登录到现有应用商店(或配置一个新应用商店)。
在适用于 Web 的 Workspace 中配置单点登录
可以使用组策略对象管理模板在适用于 Web 的 Workspace 上配置单点登录。
- 通过运行 gpedit.msc 打开适用于 Web 的 Workspace GPO 管理模板。
- 在 计算机配置 节点下,转至 管理模板 > Citrix 组件 > Citrix Workspace > 用户身份验证 。
选择 本地用户名和密码 策略并将其设置为 已启用 。
- 单击 启用直通身份验证 。此选项允许适用于 Web 的 Workspace 使用您的登录凭据在远程服务器上进行身份验证。
- 单击 允许对所有 ICA 连接执行直通身份验证 。此选项将跳过任何身份验证限制,并允许在所有连接上传递凭据。
- 重新启动适用于 Web 的 Workspace 以使所做的更改生效。
通过启动 任务管理器 来验证是否已启用单点登录,并检查 ssonsvr.exe 进程是否正在运行。
使用 Active Directory 配置单点登录
请完成以下步骤以使用 Active Directory 组策略为 Citrix Workspace 应用程序配置直通身份验证。在这种情况下,可以实现单点登录身份验证,而无需使用企业软件部署工具,例如 Microsoft System Center Configuration Manager。
下载 Citrix Workspace 应用程序安装文件 ( CitrixWorkspaceApp.exe ) 并将其放在合适的网络共享上。在其上安装了 Citrix Workspace 应用程序的目标计算机必须能够访问该安装文件。
从 适用于 Windows 的 Citrix Workspace 应用程序下载 页面获取 CheckAndDeployWorkspacePerMachineStartupScript.bat 模板。
编辑内容以反映 CitrixWorkspaceApp.exe 的位置和版本。
在 Active Directory 组策略管理 控制台中,键入 CheckAndDeployWorkspacePerMachineStartupScript.bat 作为启动脚本。有关部署启动脚本的详细信息,请参阅 Active Directory 部分。
在 计算机配置 节点中,转至 管理模板 > 添加/删除模板 以添加 receiver.adml 文件。
添加 receiver.adml 模板后,转至 计算机配置 > 管理模板 > Citrix 组件 > Citrix Workspace > 用户身份验证 。有关添加模板文件的详细信息,请参阅 组策略对象管理模板 。
选择 启用直通身份验证 ,然后单击 应用 。
重新启动计算机以使更改生效。
StoreFront 配置
- 在 StoreFront 服务器上启动 Citrix Studio ,然后选择 应用商店 > 管理身份验证方法 - 应用商店 。
身份验证令牌会加密并存储在本地磁盘上,这样您就不需要在系统或会话重新启动时重新输入凭据。Citrix Workspace 应用程序提供了用于禁止在本地磁盘上存储身份验证令牌的选项。
为了增强安全性,我们现在提供了组策略对象 (GPO) 策略来配置身份验证令牌存储。
注意: 此配置仅在云部署中适用。
要使用组策略对象 (GPO) 策略禁用存储身份验证令牌,请执行以下操作:
- 通过运行 gpedit.msc 打开 Citrix Workspace 应用程序组策略对象管理模板。
- 在 计算机配置 节点下,转至 管理模板 > Citrix 组件 > 自助服务 。
在 存储身份验证令牌 策略中,选择以下选项之一:
- 已启用:指示身份验证令牌存储在磁盘上。默认情况下,设置为“已启用”。
- 已禁用:指示身份验证令牌未存储在磁盘上。系统或会话重新启动时,请重新输入您的凭据。
自版本 2106 起,Citrix Workspace 应用程序提供用于禁止在本地磁盘上存储身份验证令牌的其他选项。除了现有 GPO 配置外,还可以使用 Global App Configuration Service 禁止在本地磁盘上存储身份验证令牌。
在 Global App Configuration Service 中,将 Store Authentication Tokens 属性设置为 False 。
可以使用 Global App Configuration Service 通过以下方法之一配置此设置:
- Global App Configuration Service 用户界面 (UI):要使用用户界面进行配置,请参阅 配置 Citrix Workspace 应用程序
- API:要使用 API 配置设置,请参阅 Citrix Developer 文档。
可以使用配置检查器运行测试,检查单点登录是否正确配置。该测试在单点登录的不同检查点运行,并显示配置结果。
- 右键单击通知区域中的 Citrix Workspace 应用程序图标,然后单击 高级首选项 。 此时将显示 高级首选项 对话框。
单击 配置检查器 。 此时将显示 Citrix 配置检查器 窗口。
- 从 选择 窗格中选择 SSONChecker 。
- 单击 运行 。将显示一个进度条,显示测试的状态。
配置检查器 窗口包含以下列:
状态: 显示特定检查点的测试结果。
- 绿色复选标记表明该特定检查点配置正确。
- 蓝色的“I”指示有关检查点的信息。
- 红色的“X”指示该特定检查点配置不正确。
- 提供程序: 显示在其上运行测试的模块的名称。在本案例中,为单点登录。
- 套件: 指示测试的类别。例如,安装。
- 测试: 指示运行的具体测试的名称。
- 详细信息: 提供有关测试的其他信息,包括通过和未通过。
用户获得有关每个检查点和相应结果的详细信息。
- 网络提供程序注册:只有将“Citrix Single Sign-On”设置为网络提供程序列表中的第一个时,针对网络提供程序注册的测试结果才会显示一个绿色复选标记。如果 Citrix Single Sign-On 显示在列表中的任何其他位置,则针对网络提供程序注册的测试结果会显示一个蓝色的“I”,并包含其他信息。
- 单点登录进程正在运行。
- 组策略:默认情况下,此策略配置在客户端上。
- Internet 的安全区域设置:请务必将 Store/XenApp Service URL 添加到“Internet 选项”中的安全区域列表中。 如果通过组策略配置安全区域,策略中出现任何更改时,都需要重新打开 高级首选项 窗口才能使所做的更改生效,以及显示测试的正确状态。
- StoreFront 的身份验证方法。
注意: 如果要访问适用于 Web 的 Workspace,则测试结果不适用。 如果 Citrix Workspace 应用程序配置有多个应用商店,则会在所有已配置的应用商店上运行身份验证方法测试。 可以将测试结果保存为报告。默认报告格式为 .txt。
隐藏“高级首选项”窗口中的“配置检查器”选项
- 转至 Citrix 组件 > Citrix Workspace > 自助服务 > DisableConfigChecker 。
- 单击 已启用 将隐藏 高级首选项 窗口中的 配置检查器 选项。
- 运行 gpupdate /force 命令。
配置检查器不包括 Citrix Virtual Apps and Desktops 服务器上“信任发送到 XML Service 的请求”配置的检查点。
Citrix Workspace 应用程序允许您使用信标检查器(作为 配置检查器 实用程序的一部分提供)执行信标测试。信标测试可帮助确认信标 (ping.citrix.com) 是否可访问。此诊断测试可帮助消除资源枚举较慢(即信标不可用)的多个可能原因之一。要运行测试,请右键单击通知区域中的 Citrix Workspace 应用程序并选择 高级首选项 > 配置检查器 。从测试列表中选择 Beacon checke (信标检查器)选项并单击 运行 。
测试结果可能为以下任一情况:
- 可访问 - Citrix Workspace 应用程序能够成功联系信标。
- 不可访问 - Citrix Workspace 应用程序无法联系信标。
- 部分可访问 - Citrix Workspace 应用程序可以间歇性地联系信标。
注意: 在适用于 Web 的 Workspace 中,这些测试结果不适用。 测试结果可以保存为报告。报告的默认格式为 .txt。
- 通过 Kerberos 进行域直通(单点登录)身份验证
本主题仅适用于在适用于 Windows 的 Citrix Workspace 应用程序与 StoreFront、Citrix Virtual Apps and Desktops 和 Citrix DaaS 之间建立的连接。
Citrix Workspace 应用程序支持为使用智能卡的部署采用 Kerberos 进行域直通(单点登录或 SSON)身份验证。Kerberos 是 集成 Windows 身份验证 (IWA) 中包含的一种身份验证方法。
启用后,无需 Citrix Workspace 应用程序的密码即可进行 Kerberos 身份验证。因此,请防止在用户设备上发生尝试获取密码访问权限的特洛伊木马攻击。用户可以使用任何身份验证方法登录并访问已发布的资源,例如指纹读取器等生物特征身份验证器。
使用智能卡登录到配置了智能卡身份验证的 Citrix Workspace 应用程序、StoreFront、Citrix Virtual Apps and Desktops 和 Citrix DaaS 时,Citrix Workspace 应用程序将:
- 在单点登录期间捕获智能卡 PIN。
使用 IWA (Kerberos) 向 StoreFront 验证用户身份。然后,StoreFront 向您的 Citrix Workspace 应用程序提供有关可用 Citrix Virtual Apps and Desktops 和 Citrix DaaS 的信息。
注意: 应启用 Kerberos 以避免额外的 PIN 提示。如果未使用 Kerberos 身份验证,Citrix Workspace 应用程序将使用智能卡凭据向 StoreFront 进行身份验证。
- HDX Engine(之前称为 ICA 客户端)将智能卡 PIN 传递给 VDA,从而使用户登录到 Citrix Workspace 应用程序会话。Citrix Virtual Apps and Desktops 和 Citrix DaaS 随后提供请求的资源。
要将 Kerberos 身份验证用于 Citrix Workspace 应用程序,请检查您的 Kerberos 配置是否符合以下条件。
- Kerberos 只在 Citrix Workspace 应用程序与属于相同或可信 Windows Server 域的服务器之间起作用。请信任服务器进行委派,您可以通过“Active Directory 用户和计算机管理”工具配置该选项。
- 必须在域和 Citrix Virtual Apps and Desktops 和 Citrix DaaS 上启用 Kerberos。为了增强安全性并确保使用 Kerberos,请在域上禁用任何非 Kerberos IWA 选项。
- Kerberos 登录不适用于配置为使用基本身份验证、始终使用指定的登录信息或始终提示输入密码的远程桌面服务连接。
警告: 注册表编辑器使用不当可能导致严重问题,可能需要重新安装操作系统。Citrix 无法保证因注册表编辑器使用不当导致出现的问题能够得以解决。使用注册表编辑器需自担风险。请确保在编辑注册表之前进行备份。
通过 Kerberos 实现的域直通(单点登录)身份验证与智能卡结合使用
在继续操作之前,请参阅 Citrix Virtual Apps and Desktops 文档中的 保护部署 部分。
安装适用于 Windows 的 Citrix Workspace 应用程序时,请包含以下命令行选项:
/includeSSON
此选项在加入域的计算机上安装 Single Sign-On 组件,从而使您的工作区能够使用 IWA (Kerberos) 向 StoreFront 进行身份验证。单点登录组件存储智能卡 PIN 码,HDX Engine 在将智能卡硬件和凭据远程传递到 Citrix Virtual Apps and Desktops 和 Citrix DaaS 时会使用此 PIN 码。Citrix Virtual Apps and Desktops 和 Citrix DaaS 自动从智能卡选择一个证书并从 HDX Engine 获取此 PIN 码。
默认情况下启用一个相关选项 ENABLE_SSON 。
如果安全策略阻止在设备上启用 Single Sign-On,请使用组策略对象管理模板配置 Citrix Workspace 应用程序。
- 选择 管理模板 > Citrix 组件 > Citrix Workspace > 用户身份验证 > 本地用户名和密码
- 选择 启用直通身份验证 。
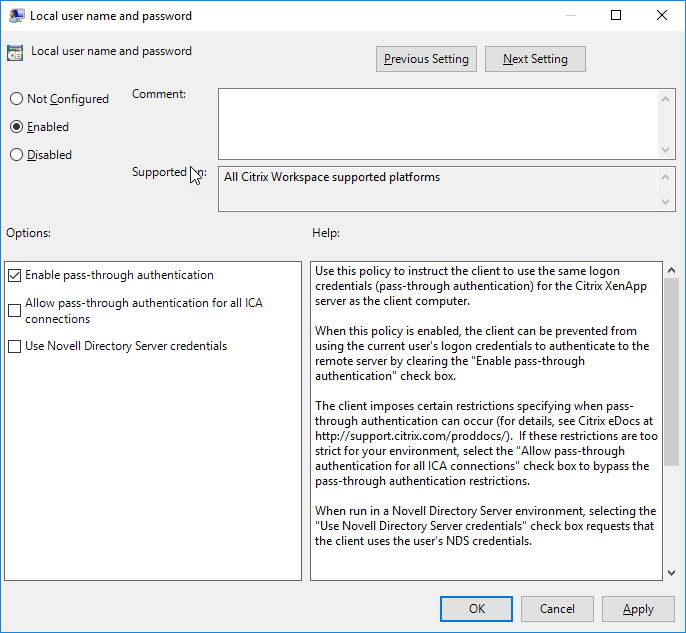
配置 StoreFront:
在 StoreFront 服务器上配置身份验证服务时,选择 域直通 选项。该设置将启用集成 Windows 身份验证。无需选择智能卡选项,除非您还具有未加入域的客户端使用智能卡连接到 StoreFront。
有关将智能卡用于 StoreFront 的详细信息,请参阅 StoreFront 文档中的 配置身份验证服务 。
- 支持 Azure Active Directory 中的条件访问
条件访问是 Azure Active Directory 强制执行组织策略所用的工具。Workspace 管理员可以为向 Citrix Workspace 应用程序进行身份验证的用户配置并强制执行 Azure Active Directory 条件访问策略。运行 Citrix Workspace 应用程序的 Windows 计算机必须已安装 Microsoft Edge WebView2 Runtime 99 或更高版本。
有关使用 Azure Active Directory 配置条件访问策略的完整详细信息和说明,请参阅 Azure AD 条件访问文档 ,地址为 Docs.microsoft.com/zh-cn/azure/active-directory/conditional-access/ 。
注意: 此功能仅在 Workspace (Cloud) 部署中受支持。
- 支持 StoreFront 应用商店的新式验证方法
可以使用组策略对象 (GPO) 模板为 StoreFront 应用商店启用对新式验证方法的支持。可以使用 Global App Configuration Service 启用此功能。
可以使用下面的任何一种方式向 Citrix StoreFront 应用商店进行身份验证:
- 使用 Windows Hello 和 FIDO2 安全密钥。有关详细信息,请参阅 其他身份验证方式 。
- 从 Azure Active Directory (AAD) 作为身份提供程序的已加入 AAD 的计算机单点登录到 Citrix StoreFront 应用商店。有关详细信息,请参阅 其他身份验证方式 。
- Workspace 管理员可以为对 Citrix StoreFront 应用商店进行身份验证的用户配置和强制执行 Azure Active Directory 条件访问策略。有关详细信息,请参阅 支持 Azure AD 中的条件访问 。
必须使用 Microsoft Edge WebView2 作为底层浏览器进行直接 StoreFront 和网关身份验证,才能启用此功能。
注意: 请确保 Microsoft Edge WebView2 Runtime 版本为 102 或更高版本。
可以使用 Global App Config Service 和组策略对象 (GPO) 模板为 StoreFront 应用商店启用新式验证方法。
使用 Global App Config Service
- 在 Citrix Cloud 菜单中,选择 Workspace Configuration (Workspace 配置),然后选择 App Configuration (应用程序配置)。
- 单击 Security & Authentication (安全性和身份验证)。
- 确保选中 Windows 复选框。
从 用于 StoreFront 身份验证的 Microsoft Edge WebView 下拉列表中选择 Windows 旁边的 已启用 。
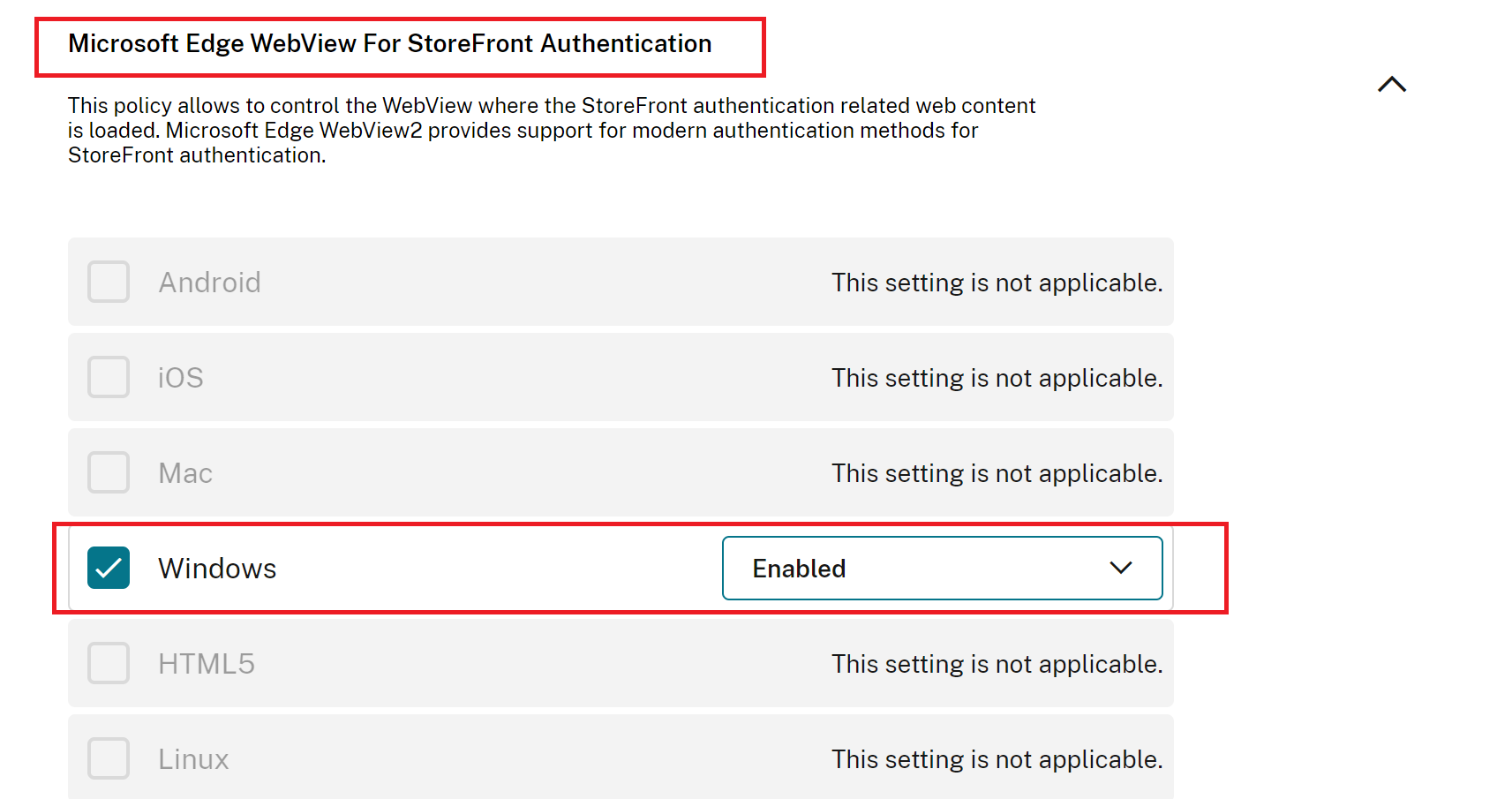
注意: 如果您从 用于 StoreFront 身份验证的 Microsoft Edge WebView 下拉列表中选择 Windows 旁边的 已禁用 ,则将在 Citrix Workspace 应用程序中使用 Internet Explorer WebView。因此,不支持对 Citrix Storefront 应用商店使用新式验证方法。
- 在 计算机配置 节点下,转至 管理模板 > Citrix Workspace > 用户身份验证 。
单击 Microsoft Edge WebView for StoreFront authentication (适用于 StoreFront 的 Microsoft Edge WebView 身份验证)策略并将其设置为 Enabled (已启用)。
- 单击 应用 ,然后单击 确定 。
禁用此策略后,Citrix Workspace 应用程序使用 Internet Explorer WebView。因此,不支持 Citrix StoreFront 应用商店的新式验证方法。
您可以使用 Citrix Workspace 应用程序配置以下身份验证机制。为使以下身份验证机制正常发挥作用,运行 Citrix Workspace 应用程序的 Windows 计算机必须安装了 Microsoft Edge WebView2 Runtime 99 或更高版本。
基于 Windows Hello 的身份验证 – 有关配置基于 Windows Hello 的身份验证的说明,请参阅 配置 Windows Hello 企业版策略设置 - 证书信任 ,地址为 Docs.microsoft.com/zh-cn/windows/security/identity-protection/hello-for-business/hello-cert-trust-policy-settings。
注意: 不支持使用域直通(单点登录或 SSON)的基于 Windows Hello 的身份验证。
- 基于 FIDO2 安全密钥的身份验证 – FIDO2 安全密钥为企业员工提供了一种无需输入用户名或密码即可无缝进行身份验证的方式。您可以配置向 Citrix Workspace 进行基于 FIDO2 安全密钥的身份验证。如果希望用户使用 FIDO2 安全密钥通过其 Azure AD 帐户向 Citrix Workspace 进行身份验证,请参阅 启用无密码安全密钥登录 ,地址为 Docs.microsoft.com/zh-cn/azure/active-directory/authentication/howto-authentication-passwordless-security-key 。
- 此外,您还可以从加入了 Microsoft Azure Active Directory (AAD) 且 AAD 为身份提供程序的计算机单点登录 (SSO) 到 Citrix Workspace 应用程序。有关配置 Azure Active Directory 域服务的更多详细信息,请参阅 配置 Azure Active Directory 域服务 ,网址为 Docs.microsoft.com/en-us/azure/active-directory-domain-services/overview 。有关如何将 Azure Active Directory 连接到 Citrix Cloud 的信息,请参阅 将 Azure Active Directory 连接到 Citrix Cloud 。
适用于 Windows 的 Citrix Workspace 应用程序支持以下智能卡身份验证:
直通身份验证(单点登录) - 当用户登录 Citrix Workspace 应用程序时,直通身份验证可捕获智能卡凭据。Citrix Workspace 应用程序按以下方式使用捕获的凭据:
- 使用智能卡登录 Citrix Workspace 应用程序的已加入域的设备用户无需重新进行身份验证即可启动虚拟桌面和应用程序。
- 在使用智能卡凭据的情况下,对于在未加入域的设备上运行的 Citrix Workspace 应用程序,用户必须再次键入凭据才可启动虚拟桌面或应用程序。
直通身份验证需要使用 StoreFront 和 Citrix Workspace 应用程序上的配置。
双模式身份验证 - 双模式身份验证允许用户在使用智能卡与键入用户名和密码之间进行选择。无法使用智能卡时,可使用此功能。例如,登录证书已过期。必须为每个站点设置专用应用商店才允许使用双模式身份验证,并将 DisableCtrlAltDel 方法设置为 False 以允许使用智能卡。双模式身份验证需要 StoreFront 配置。
通过使用双模式身份验证,StoreFront 管理员可以允许针对同一个应用商店使用用户名和密码身份验证以及智能卡身份验证,方法是在 StoreFront 控制台中进行选择。请参阅 StoreFront 文档。
多个证书 – 如果正在使用多个证书,则其可用于单个智能卡。如果您将智能卡插入读卡器,则这些证书适用于在用户设备上运行的所有应用程序,包括 Citrix Workspace 应用程序。
客户端证书身份验证 – 客户端证书身份验证需要使用 Citrix Gateway 和 StoreFront 配置。
- 要通过 Citrix Gateway 访问 StoreFront,在移除智能卡后您必须重新进行身份验证。
- 当 Citrix Gateway SSL 配置设置为 强制客户端证书身份验证 时,操作更加安全。但是,强制客户端证书身份验证与双模式身份验证不兼容。
双跳会话 - 如果需要双跳,则需要在 Citrix Workspace 应用程序和用户的虚拟桌面之间建立连接。
支持智能卡的应用程序 - 支持智能卡的应用程序(如 Microsoft Outlook 和 Microsoft Office)允许用户对虚拟应用程序和桌面会话中的文档进行数字签名或加密。
- 证书必须存储在智能卡上,而非存储在用户设备上。
- Citrix Workspace 应用程序不保存用户证书选择信息,但在配置时存储 PIN。PIN 仅在用户会话期间缓存在非分页内存中,不会存储在磁盘中。
- 插入智能卡后,Citrix Workspace 应用程序不会重新连接会话。
- 针对智能卡身份验证进行配置后,Citrix Workspace 应用程序不支持虚拟专用网络 (VPN) 单点登录或会话预启动。要将 VPN 与智能卡身份验证结合使用,请安装 Citrix Gateway 插件。使用智能卡和 PIN 登录 Web 页面,在每一步操作中进行身份验证。使用 Citrix Gateway 插件通过直通身份验证访问 StoreFront 不适用于智能卡用户。
- Citrix Workspace 应用程序更新程序与 citrix.com 通信,且 Merchandising Server 与 Citrix Gateway 上的智能卡身份验证不兼容。
警告 某些配置需要编辑注册表。注册表编辑器使用不当可能导致问题,可能需要重新安装操作系统。Citrix 无法保证因注册表编辑器使用不当导致出现的问题能够得以解决。请确保在编辑注册表之前进行备份。
要为智能卡身份验证启用单点登录,请执行以下操作:
要配置适用于 Windows 的 Citrix Workspace 应用程序,请在安装期间包含以下命令行选项:
ENABLE_SSON=Yes
单点登录是另一个用于直通身份验证的术语。启用此设置可阻止 Citrix Workspace 应用程序第二次显示 PIN 提示。
在注册表编辑器中,导航到以下路径并将 SSONCheckEnabled 字符串设置为 False (如果您尚未安装单点登录组件)。
HKEY_CURRENT_USER\Software{Wow6432}\Citrix\AuthManager\protocols\integratedwindows\
HKEY_LOCAL_MACHINE\Software{Wow6432}\Citrix\AuthManager\protocols\integratedwindows\
此注册表项可阻止 Citrix Workspace 应用程序身份验证管理器查找 Single Sign-On 组件,并允许 Citrix Workspace 应用程序向 StoreFront 进行身份验证。
要为 StoreFront 启用智能卡身份验证而非 Kerberos,请使用下面的命令行选项安装适用于 Windows 的 Citrix Workspace 应用程序:
/includeSSON 安装单点登录(直通)身份验证。启用凭据缓存以及使用基于域的直通身份验证。
如果用户使用其他身份验证方法(例如用户名和密码)登录端点,则命令行为:
/includeSSON LOGON_CREDENTIAL_CAPTURE_ENABLE=No
此类型的身份验证可防止在登录时捕获凭据,并允许 Citrix Workspace 应用程序在 Citrix Workspace 应用程序登录期间存储 PIN。
- 转至 管理模板 > Citrix 组件 > Citrix Workspace > 用户身份验证 > 本地用户名和密码 。
- 选择 启用直通身份验证 。根据配置和安全设置,选择 允许对所有 ICA 执行直通身份验证 选项以便能够使用直通身份验证。
- 配置身份验证服务时,请选中 智能卡 复选框。
要使用户设备支持使用智能卡,请执行以下操作:
- 将证书颁发机构根证书导入设备的密钥库。
- 安装供应商的加密中间件。
- 安装和配置 Citrix Workspace 应用程序。
要更改证书的选择方式,请执行以下操作:
默认情况下,如果多个证书有效,则 Citrix Workspace 应用程序将提示用户从列表中选择证书。可以改为将 Citrix Workspace 应用程序配置为使用默认证书(根据智能卡提供商)或近期即将过期的证书。如果没有有效的登录证书,则会向用户发出通知,并提供使用其他可用登录方法的选项。
有效证书必须具备以下所有特点:
- 本地计算机上时钟的当前时间在证书有效期内。
- 使用者公钥 必须使用 RSA 算法且密钥长度为 1024 位、2048 位或 4096 位。
- 密钥用法必须包括数字签名。
- 使用者备用名称必须包括用户主体名称 (UPN)。
- 增强型密钥用法必须包括智能卡登录和客户端身份验证或所有密钥用法。
- 证书颁发者链条中的证书颁发机构之一必须匹配服务器在 TLS 握手时发送的允许使用的可分辨名称 (DN) 之一。
使用以下方法之一可更改证书的选择方式:
在 Citrix Workspace 应用程序命令行中,指定选项 AM_CERTIFICATESELECTIONMODE={ Prompt | SmartCardDefault | LatestExpiry } 。
默认有提示。对于 SmartCardDefault 或 LatestExpiry ,如果有多个证书符合条件,则 Citrix Workspace 应用程序将提示用户从中选择一个证书。
在 HKEY_CURRENT_USER 中定义的值优先级高于 HKEY_LOCAL_MACHINE 中的值,可更好地帮助用户选择证书。
要使用 CSP PIN 提示,请执行以下操作:
默认情况下,向用户显示的 PIN 提示由适用于 Windows 的 Citrix Workspace 应用程序而不是智能卡加密服务提供程序 (CSP) 提供。Citrix Workspace 应用程序在需要时提示用户输入 PIN,然后将 PIN 传递给智能卡 CSP。如果您的站点或智能卡有更严格的安全要求(如不允许在每进程或每会话缓存 PIN),则可将 Citrix Workspace 应用程序配置为使用 CSP 组件以管理 PIN 条目,包括输入 PIN 的提示。
使用以下方法之一更改 PIN 条目的处理方式:
- 在 Citrix Workspace 应用程序命令行中,指定选项 AM_SMARTCARDPINENTRY=CSP 。
- 将以下项值添加到注册表项 HKEY_LOCAL_MACHINE\Software\[Wow6432Node\Citrix\AuthManager :SmartCardPINEntry=CSP。
删除智能卡时,Citrix Virtual Apps 会话将注销。如果在 Citrix Workspace 应用程序中已将智能卡配置为身份验证方法,请在适用于 Windows 的 Citrix Workspace 应用程序上配置相应的策略以强制注销 Citrix Virtual Apps 会话。而用户在 Citrix Workspace 应用程序会话中仍然保持登录状态。
使用智能卡身份验证登录 Citrix Workspace 应用程序站点时,用户名显示为 已登录 。
快速智能卡是对现有基于 HDX PC/SC 的智能卡重定向的改进。在高延迟 WAN 环境中使用智能卡时,可以提高性能。
仅在 Windows VDA 上支持快速智能卡。
要在 Citrix Workspace 应用程序中启用快速智能卡登录,请执行以下操作:
默认情况下,快速智能卡登录在 VDA 上处于启用状态,在 Citrix Workspace 应用程序中处于禁用状态。要启用快速智能卡登录,请在关联的 StoreFront 站点的 default.ica 文件中包含以下参数:
要在 Citrix Workspace 应用程序中禁用快速智能卡登录,请执行以下操作:
要在 Citrix Workspace 应用程序中禁用快速智能卡登录,请从关联的 StoreFront 站点的 default.ica 文件中删除 SmartCardCryptographicRedirection 参数。
有关详细信息,请参阅 智能卡 。
- 面向 Citrix Workspace 的无提示身份验证
Citrix Workspace 应用程序引入了组策略对象 (GPO) 策略以启用面向 Citrix Workspace 的无提示身份验证。此策略使 Citrix Workspace 应用程序能够在系统启动时自动登录 Citrix Workspace。仅当为加入了域的设备上的 Citrix Workspace 配置了域直通(单点登录或 SSON)时,才使用此策略。此功能在适用于 Windows 的 Citrix Workspace 应用程序版本 2012 及更高版本中提供。
要使此策略起作用,必须满足以下条件:
- 必须在注册表编辑器中将 SelfServiceMode 密钥设置为 Off 。
- 在 计算机配置 节点下,转至 管理模板 > Citrix Workspace > 自助服务 。
- 单击 面向 Citrix Workspace的无提示身份验证 策略并将其设置为 已启用 。
- 阻止适用于 Windows 的 Citrix Workspace 应用程序缓存密码和用户名
默认情况下,适用于 Windows 的 Citrix Workspace 应用程序会自动填充上次输入的用户名。要清除用户名字段的自动填充,请编辑用户设备上的注册表:
- 创建 REG_SZ 值 HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\AuthManager\RememberUsername。
- 将其值设置为“false”。
要禁用 Remember my password (记住我的密码)复选框并阻止自动登录,请在安装了适用于 Windows 的 Citrix Workspace 应用程序的客户端计算机上创建以下注册表项:
- 路径:HKEY_LOCAL_MACHINE\Software\wow6432node\Citrix\AuthManager
- 名称:SavePasswordMode
注意: 注册表编辑器使用不当可能导致严重问题,可能需要重新安装操作系统。Citrix 无法保证因注册表编辑器使用不当导致出现的问题能够得以解决。使用注册表编辑器需自担风险。请确保在编辑注册表之前进行备份。
要防止缓存 StoreFront 应用商店的凭据,请参阅 StoreFront 文档中的 阻止适用于 Windows 的 Citrix Workspace 应用程序缓存密码和用户名 。
- 在 Azure AD 中支持 200 多个组
在本版本中,属于 200 多个组的 Azure AD 用户可以查看分配给该用户的应用程序和桌面。以前,同一用户无法查看这些应用程序和桌面。
注意: 用户必须从 Citrix Workspace 应用程序注销并重新登录才能启用此功能。
以前,在配置了代理身份验证的客户端计算机上,如果 Windows 凭据管理器 中不存在代理凭据,则不允许您向 Citrix Workspace 应用程序进行身份验证。
自适用于 Windows 的 Citrix Workspace 应用程序版本 2102 及更高版本起,在配置为进行代理身份验证的客户端计算机上,如果代理凭据未存储在 Windows 凭据管理器 中,则会显示身份验证提示,要求您输入代理凭据。然后,Citrix Workspace 应用程序将代理服务器凭据保存在 Windows 凭据管理器 中。这样可以打造无缝登录体验,因为您无需在访问 Citrix Workspace 应用程序之前在 Windows 凭据管理器中手动保存凭据。
Citrix Workspace 应用程序在网络请求中发送用户代理,该请求可用于配置身份验证策略,包括将身份验证重定向到其他身份提供商 (IdP)。
注意: 例如下表中作为用户-代理的一部分提到的版本号,它会根据您使用的版本自动更新。
下表介绍了场景、描述以及每种场景的相应用户-代理:
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.
是否要使用您的浏览器的首选语言切换到该 Web 站点?
Edit Article

Current time by city
For example, New York
Current time by country
For example, Japan
Time difference
For example, London
For example, Dubai
Coordinates
For example, Hong Kong
For example, Delhi
For example, Sydney
Geographic coordinates of Elektrostal, Moscow Oblast, Russia
City coordinates
Coordinates of Elektrostal in decimal degrees
Coordinates of elektrostal in degrees and decimal minutes, utm coordinates of elektrostal, geographic coordinate systems.
WGS 84 coordinate reference system is the latest revision of the World Geodetic System, which is used in mapping and navigation, including GPS satellite navigation system (the Global Positioning System).
Geographic coordinates (latitude and longitude) define a position on the Earth’s surface. Coordinates are angular units. The canonical form of latitude and longitude representation uses degrees (°), minutes (′), and seconds (″). GPS systems widely use coordinates in degrees and decimal minutes, or in decimal degrees.
Latitude varies from −90° to 90°. The latitude of the Equator is 0°; the latitude of the South Pole is −90°; the latitude of the North Pole is 90°. Positive latitude values correspond to the geographic locations north of the Equator (abbrev. N). Negative latitude values correspond to the geographic locations south of the Equator (abbrev. S).
Longitude is counted from the prime meridian ( IERS Reference Meridian for WGS 84) and varies from −180° to 180°. Positive longitude values correspond to the geographic locations east of the prime meridian (abbrev. E). Negative longitude values correspond to the geographic locations west of the prime meridian (abbrev. W).
UTM or Universal Transverse Mercator coordinate system divides the Earth’s surface into 60 longitudinal zones. The coordinates of a location within each zone are defined as a planar coordinate pair related to the intersection of the equator and the zone’s central meridian, and measured in meters.
Elevation above sea level is a measure of a geographic location’s height. We are using the global digital elevation model GTOPO30 .
Elektrostal , Moscow Oblast, Russia

Victor Mukhin
- Scientific Program

Title : Active carbons as nanoporous materials for solving of environmental problems
However, up to now, the main carriers of catalytic additives have been mineral sorbents: silica gels, alumogels. This is obviously due to the fact that they consist of pure homogeneous components SiO2 and Al2O3, respectively. It is generally known that impurities, especially the ash elements, are catalytic poisons that reduce the effectiveness of the catalyst. Therefore, carbon sorbents with 5-15% by weight of ash elements in their composition are not used in the above mentioned technologies. However, in such an important field as a gas-mask technique, carbon sorbents (active carbons) are carriers of catalytic additives, providing effective protection of a person against any types of potent poisonous substances (PPS). In ESPE “JSC "Neorganika" there has been developed the technology of unique ashless spherical carbon carrier-catalysts by the method of liquid forming of furfural copolymers with subsequent gas-vapor activation, brand PAC. Active carbons PAC have 100% qualitative characteristics of the three main properties of carbon sorbents: strength - 100%, the proportion of sorbing pores in the pore space – 100%, purity - 100% (ash content is close to zero). A particularly outstanding feature of active PAC carbons is their uniquely high mechanical compressive strength of 740 ± 40 MPa, which is 3-7 times larger than that of such materials as granite, quartzite, electric coal, and is comparable to the value for cast iron - 400-1000 MPa. This allows the PAC to operate under severe conditions in moving and fluidized beds. Obviously, it is time to actively develop catalysts based on PAC sorbents for oil refining, petrochemicals, gas processing and various technologies of organic synthesis.
Victor M. Mukhin was born in 1946 in the town of Orsk, Russia. In 1970 he graduated the Technological Institute in Leningrad. Victor M. Mukhin was directed to work to the scientific-industrial organization "Neorganika" (Elektrostal, Moscow region) where he is working during 47 years, at present as the head of the laboratory of carbon sorbents. Victor M. Mukhin defended a Ph. D. thesis and a doctoral thesis at the Mendeleev University of Chemical Technology of Russia (in 1979 and 1997 accordingly). Professor of Mendeleev University of Chemical Technology of Russia. Scientific interests: production, investigation and application of active carbons, technological and ecological carbon-adsorptive processes, environmental protection, production of ecologically clean food.
Quick Links
- Conference Brochure
- Tentative Program


IMAGES
VIDEO
COMMENTS
The Kerberos SSO extension features for iOS, iPadOS, and visionOS 1.1 include the following: Authentication methods: Adds support for multiple different authentication methods including passwords and certificate identities (PKINIT). The certificate identity can be on a CryptoTokenKit smart card, an MDM-supplied identity, or the local keychain.
Kerberos TGT upon network state changes to ensure that the user is ready to authenticate when needed. Active Directory account management ... • Use Safari to access a website that supports Kerberos authentication. • Launch an app that supports Kerberos authentication. 3. Enter your Kerberos or Active Directory user name and password.
Any Mac app that supports Kerberos authentication works with SSO. This includes many of the apps built in to macOS, such as Safari, Mail, and Calendar, as well as services like file sharing, screen sharing, and secure shell (SSH). Many third-party apps, such as Microsoft Outlook, support Kerberos as well.
This includes setting the user principal name (that is, the Active Directory user account) and Kerberos realm settings, as well as configuring which apps and Safari web URLs should be allowed to use SSO. To configure Kerberos in macOS, acquire tickets with Ticket Viewer, log in to a Windows Active Directory domain, or use the kinit command-line ...
The Kerberos single sign-on (SSO) extension on macOS Catalina10.15 will log users into native apps (for apps that support Kerberos authentication) and sync local user passwords with a directory service such as Microsoft Active Directory. With the Kerberos SSO extension, users do not have to provide their user name and password to access native ...
Kerberos is a network authentication protocol developed and maintained by MIT since the 80s. The image below is one of my favorite images. For our purposes, to keep it really simple since this isn't a class on Kerberos, we use kerberos with certificate-based authentication on iOS to authenticate seamlessly to applications. ... (iOS Safari ...
The Kerberos Single Sign-on extension is a credential extension designed to manage Kerberos/Active Directory credentials, synchronize local and Directory passwords, and support authentication via smart cards, MDM-provided certificate-based identity, and username/password. Included in iOS 13, iPadOS, and macOS Catalina, this extension is a ...
Microsoft Enterprise SSO plug-in vs. Kerberos SSO extension. When you use the SSO app extension, ... Recommended value: 1 When set to 1, users can sign in from Safari browser, and from apps that don't support MSAL. Enabling this setting allows users to bootstrap the extension from Safari or other apps.
The command to authenticate to the Kerberos system: /usr/bin/kinit <SUNetID>. This is also referred to as "acquiring a TGT or ticket-granting ticket." The command to display currently held TGTs: /usr/bin/klist. The command to delete current TGTs: /usr/bin/kdestroy. The command to change your Kerberos password, /usr/bin/kpasswd, is included in ...
If so, they may already have Kerberos credentials once they're logged in. To check this, use the klist command from a terminal prompt; you should see something like: $ klist. Credentials cache: API:17DFC650-1327-4721-92ED-A0099CA09885. Principal: [email protected].
macOS Safari. IWA is enabled automatically in Safari on macOS. Make sure that the macOS host is a Windows domain member. ... If a site asks your browser to provide the Kerberos ticket, the browser only provides the ticket if the site is on the allowlist. Launch the Terminal application. Create a Kerberos ticket for the account: kinit user.name ...
Our MI environment uses the eSentry Tunnel server (SSL VPN basically) to allow iOS devices to connect in to on-prem resources, and then authenticate against them with Seamless SSO using certificates pulled from SCEP. I want to do the same thing with Intune, which I'm told to use the SSO Extension Device Feature policy, and have followed a few ...
It looks as though this is something that Apple has some limited support on. We would like to link you to the information we were able to find, in hopes that it directs you to the information you need. You can check out these pages with information here: Intro to Kerberos Single sign-on with Apple devices. Using the Kerberos SSO extension with ...
Applications and Services / Safari Looks like no one's replied in a while. To start the conversation again, simply ask a new question. ... 10 points Safari and Kerberos. I log onto my university's logging system (Kerberos). I get authenticated, so I assume I have the cookie. I go to the library page to search electronic journals.
The full Kerberos realm where the user's account is located. Yes. Hosts. Approved domains that can be authenticated with the app extension. No. Preferred KDCs. The ordered list of preferred Key Distribution Centers (KDCs) to use for Kerberos traffic. If the servers are specified, they're used for both connectivity checks and attempted first ...
Kerberos authentication allows your computer to log into certain services automatically without you having to enter (and re-enter) your password (it's a SSO—single sign-on—service). Kerberos v5 is baked into Windows and Internet Explorer and works great with many LDAP-enabled services (for example, Drupal's LDAP module allows includes a submodule for SSO support).
Posted on 07-22-2021 02:38 PM. The Apple Kerberos extension is just for the logged in user to get a Kerberos ticket. It doesn't play a part in creating the user account. The local username/password is technically independent, but you can set the extension to keep the passwords in sync. 0 Kudos.
Elektrostal is a city in Moscow Oblast, Russia, located 58 kilometers east of Moscow. Elektrostal has about 158,000 residents. Mapcarta, the open map.
40 Facts About Elektrostal. Elektrostal is a vibrant city located in the Moscow Oblast region of Russia. With a rich history, stunning architecture, and a thriving community, Elektrostal is a city that has much to offer. Whether you are a history buff, nature enthusiast, or simply curious about different cultures, Elektrostal is sure to ...
To sign in to the Kerberos SSO extension with a smart card, follow these steps: Click the Options menu, then select "Use a smart card". When you see the Identity button, insert your smart card and click the button. Choose the identity that you want to authenticate with, click OK, then click Sign In.
Citrix Workspace 应用程序支持为使用智能卡的部署采用 Kerberos 进行域直通(单点登录或 SSON)身份验证。Kerberos 是集成 Windows 身份验证 (IWA) 中包含的一种身份验证方法。 启用后,无需 Citrix Workspace 应用程序的密码即可进行 Kerberos 身份验证。
Geographic coordinates of Elektrostal, Moscow Oblast, Russia in WGS 84 coordinate system which is a standard in cartography, geodesy, and navigation, including Global Positioning System (GPS). Latitude of Elektrostal, longitude of Elektrostal, elevation above sea level of Elektrostal.
Title : Active carbons as nanoporous materials for solving of environmental problems Abstract: However, up to now, the main carriers of catalytic additives have been mineral sorbents: silica gels, alumogels. This is obviously due to the fact that they consist of pure homogeneous components SiO2 and Al2O3, respectively.