
An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
https://www.nist.gov/nvlap/publications-and-forms/site-assessment-checklists

National Voluntary Laboratory Accreditation Program (NVLAP)
On-site assessment checklists.
The NIST Handbook 150 series checklists, which correspond to the program-specific handbooks, may be downloaded from NVLAP Interactive Web System (NIWS) Lab portal or Assessor portal.
Programs that use the Test Method Review Summary in conjunction with the NIST Handbook 150 Checklists are flagged by an asterisk.
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( A locked padlock ) or https:// means you've safely connected to the .gov website. Share sensitive information only on official, secure websites.
- Create Account
Administrative Site Visit and Verification Program
USCIS started the Administrative Site Visit and Verification Program in July 2009 as an additional way to verify information in certain visa petitions. Under this program, immigration officers in the Fraud Detection and National Security Directorate (FDNS) make unannounced site visits to collect information as part of a compliance review.
What is a compliance review?
Immigration officers conduct compliance reviews to ensure that petitioners (employers) and beneficiaries (job applicant or other potential employee) follow the terms and conditions of their petitions. This process includes reviewing the petition and supporting documents, researching information in public records and government systems, and, where possible, interviewing the petitioner and beneficiary through unannounced site visits.
Participating in a site visit is voluntary, but strongly encouraged
Participation in the compliance review process is voluntary. FDNS immigration officers will end a site visit if a petitioner or beneficiary expresses an unwillingness to participate. When this happens, the FDNS immigration officer will complete the compliance review by using all available information and will document the circumstances of around ending the site visit.
Types of petitions subject to site visits
As of fiscal year 2019, FDNS conducts compliance-review site visits on petitions for:
- Special immigrant religious workers petitions (before and after adjudication);
- H-1B nonimmigrant temporary visas (after adjudication);
- L-1 nonimmigrant intracompany transferee executive or manager visas (after adjudication); and
- EB-5 immigrant investor program visas (before adjudication)
How USCIS chooses site visits
FDNS randomly selects petitioners for site visits after USCIS adjudicates their petitions.
Immigration officer tasks
Officers record their observations on a Compliance Review Report. Officers occasionally conduct multiple site visits if they need more information to complete a compliance review. At the site visit, the officer will:
- Verify the information, including supporting documents, submitted with the petition;
- Verify that the petitioning organization exists;
- Review public records and information on the petitioning organization;
- Conduct unannounced site visits to where the beneficiary works;
- Take photographs;
- Review documents;
- Interview personnel to confirm the beneficiary’s work location, physical workspace, hours, salary and duties; and
- Speak with the beneficiary.
How employers should prepare for a potential site visit
Before a site visit : Employers should be prepared to present any information originally submitted with the petition. The immigration officer may also may ask for more information relevant to the petition.
During the site visit : Employers should immediately provide all readily available documents and information that the immigration officer requests.
After the site visit : Employers should provide all additional information that USCIS requests in any follow-up communication.
Why some employers receive repeated site visits
Employers might receive more than one site visit if they petition for more than one beneficiary. Each compliance review focuses on one petition and beneficiary. FDNS will randomly select such employers for multiple site visits.
What happens after a site visit?
Because FDNS immigration officers are not adjudicators, they do not make decisions on petitions or applications for immigration benefits. USCIS will review an officer’s Compliance Review Report for any indicators of fraud or noncompliance, and, FDNS may refer the case to U.S. Immigration and Customs Enforcement for criminal investigation.
Free ISO 27001 Checklists and Templates
By Andy Marker | May 7, 2020
- Share on Facebook
- Share on LinkedIn
Link copied
We’ve compiled the most useful free ISO 27001 information security standard checklists and templates, including templates for IT, HR, data centers, and surveillance, as well as details for how to fill in these templates.
Included on this page, you'll find an ISO 27001 checklist and an ISO 27001 risk assessment template , as well as an up-to-date ISO 27001 checklist for ISO 27001 compliance.
ISO 27001 Checklist

Use this simple ISO 27001 checklist to ensure that you implement your information security management systems (ISMS) smoothly, from initial planning to the certification audit. This 14-step checklist provides you with a list of all stages of ISO 27001 execution, so you can account for every component you need to attain ISO 27001 certification. This reusable checklist is available in Word as an individual ISO 270010-compliance template and as a Google Docs template that you can easily save to your Google Drive account and share with others.
Download ISO 27001 Checklist
Excel | Word | PDF
See how Smartsheet can help you be more effective
Watch the demo to see how you can more effectively manage your team, projects, and processes with real-time work management in Smartsheet.
Watch a free demo
ISO 27001 Risk Assessment Template
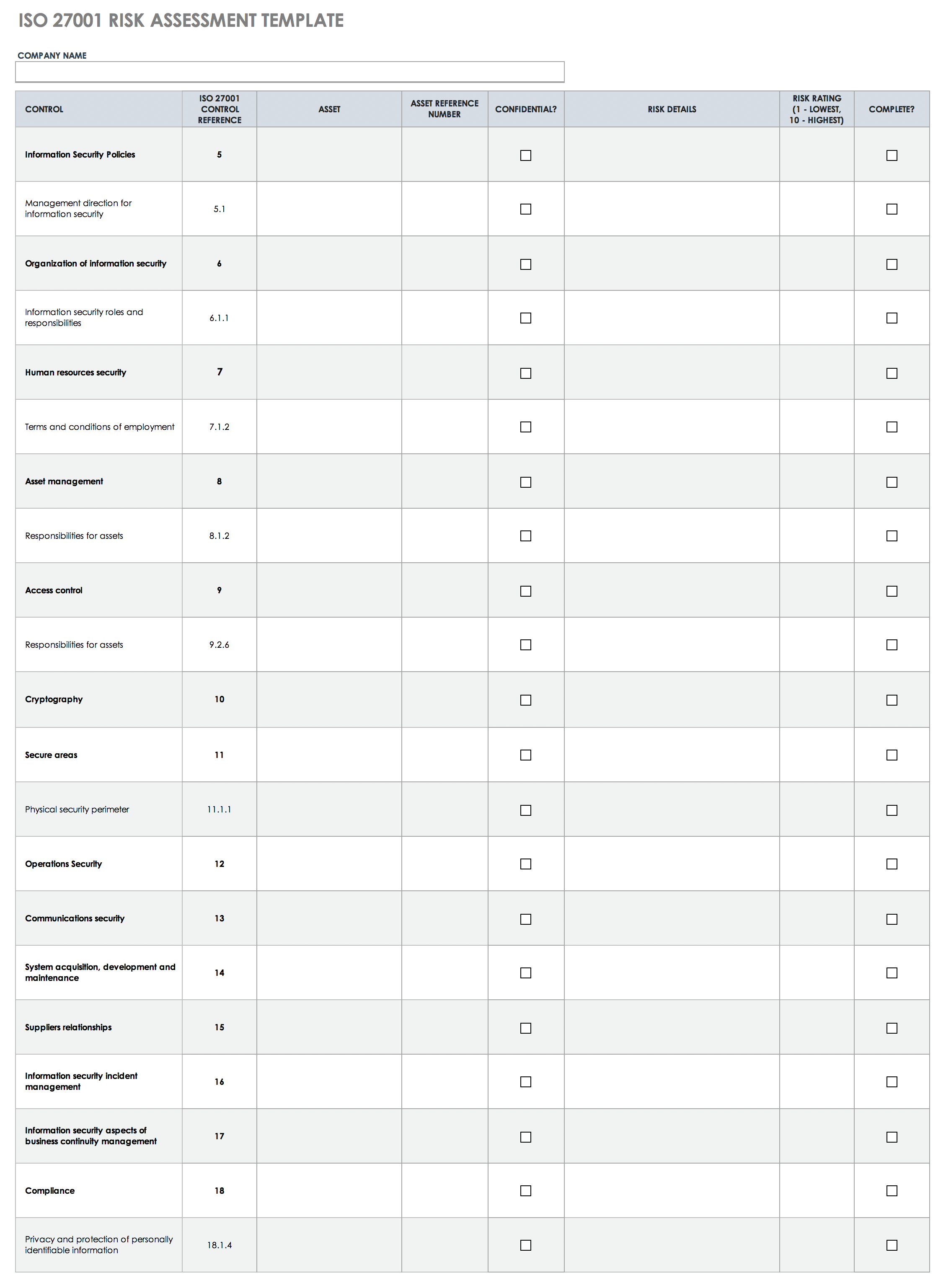
This ISO 27001 risk assessment template provides everything you need to determine any vulnerabilities in your information security system (ISS), so you are fully prepared to implement ISO 27001. The details of this spreadsheet template allow you to track and view — at a glance — threats to the integrity of your information assets and to address them before they become liabilities.
This simple template provides columns to detail asset name and number, confidentiality impact, risk details and rating, control details, and status. Use it as you seek ISO 27001 compliance certification.
Download ISO 27001 Risk Assessment Template - Excel
For more on ISMS, see “ Everything You Need to Know about Information Security Management Systems .”
ISO 27001 Controls Checklist
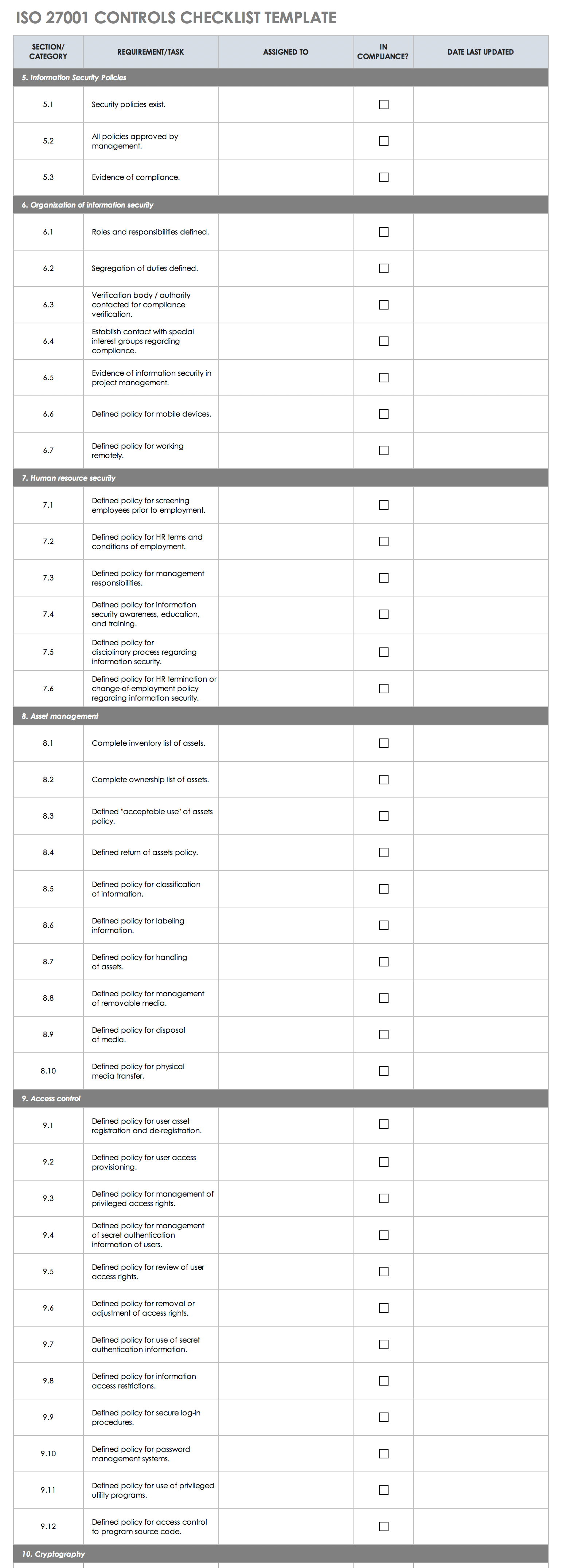
Track the overall implementation and progress of your ISO 27001 ISMS controls with this easily fillable ISO 27001 controls checklist template. The template includes an ISO 27001 clause column and allows you to track every component of successful ISO 27001 implementation.
Additionally, enter details pertaining to mandatory requirements for your ISMS, their implementation status, notes on each requirement’s status, and details on next steps. Use the status dropdown lists to track the implementation status of each requirement as you move toward full ISO 27001 compliance.
Download ISO 27001 Controls Checklist
Excel | Word | Smartsheet
ISO 27001-2013 Auditor Checklist
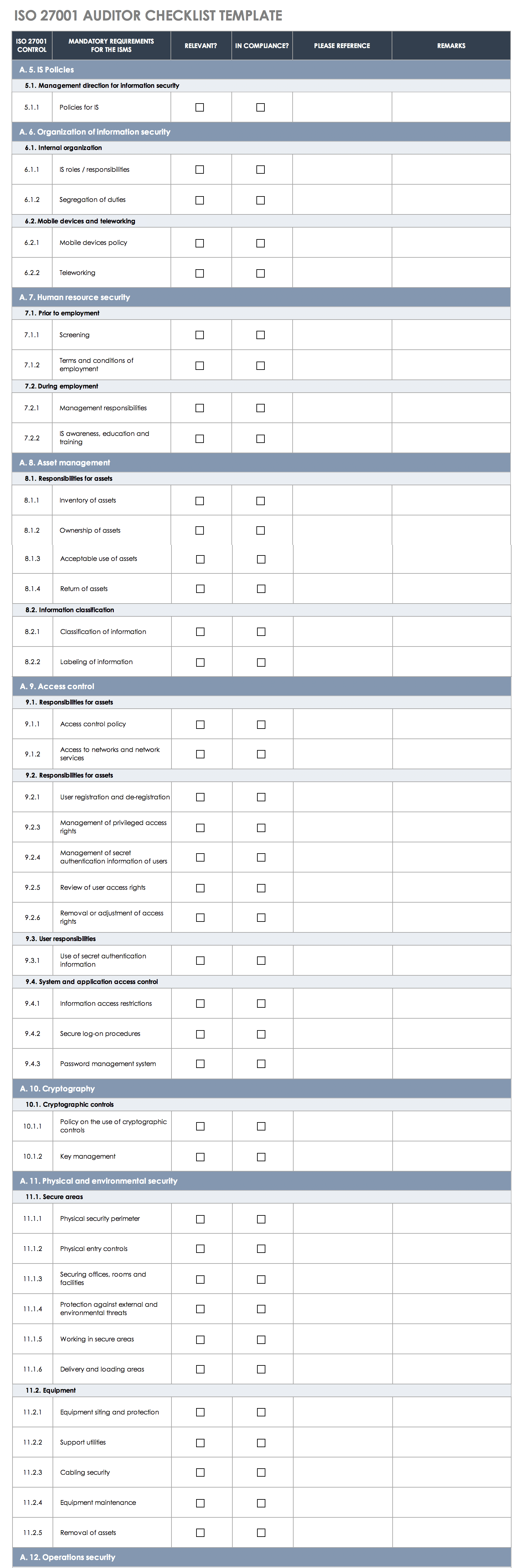
This ISO 27001-2013 auditor checklist provides an easily scannable view of your organization’s compliance with ISO 27001-2013. Columns include control-item numbers (based on ISO 27001 clause numbering), a description of the control item, your compliance status, references related to the control item, and issues related to reaching full ISO 27001 compliance and certification.
Whether you need to perform a preliminary internal audit or prepare for an external audit and ISO 27001 certification, this easy-to-fill checklist helps ensure that you identify potential issues that must be addressed in order to achieve ISO 27001 compliance.
Download ISO 27001-2013 Auditor Checklist
Excel | Word
ISO 27001 Compliance Checklist
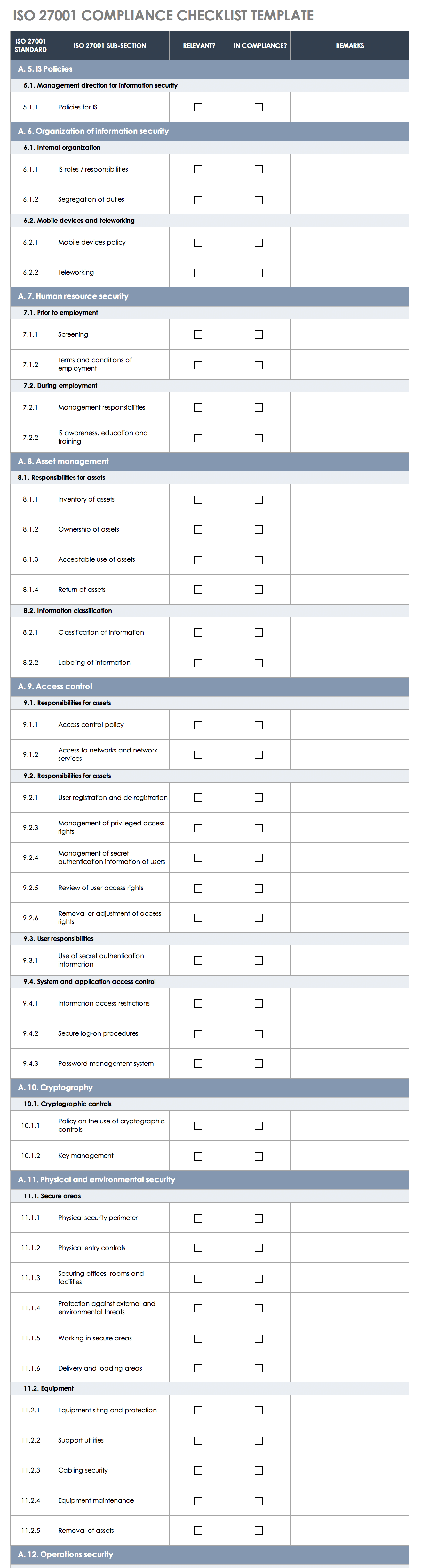
This single-source ISO 27001 compliance checklist is the perfect tool for you to address the 14 required compliance sections of the ISO 27001 information security standard.
Keep all collaborators on your compliance project team in the loop with this easily shareable and editable checklist template, and track every single aspect of your ISMS controls. This pre-filled template provides standards and compliance-detail columns to list the particular ISO 27001 standard (e.g., A.5.1 - Management Direction for Information, A.5.1.1 - Policies for Information Security, etc.), as well as assessment and results columns to track progress on your way to ISO 27001 certification.
Download ISO 27001 Compliance Checklist
For more on data security, see “ Data Security 101: Understanding the Crisis of Data Breaches, and Best Practices to Keep Your Organization's Data Secure .”
ISO 27001 Internal Audit Schedule Template
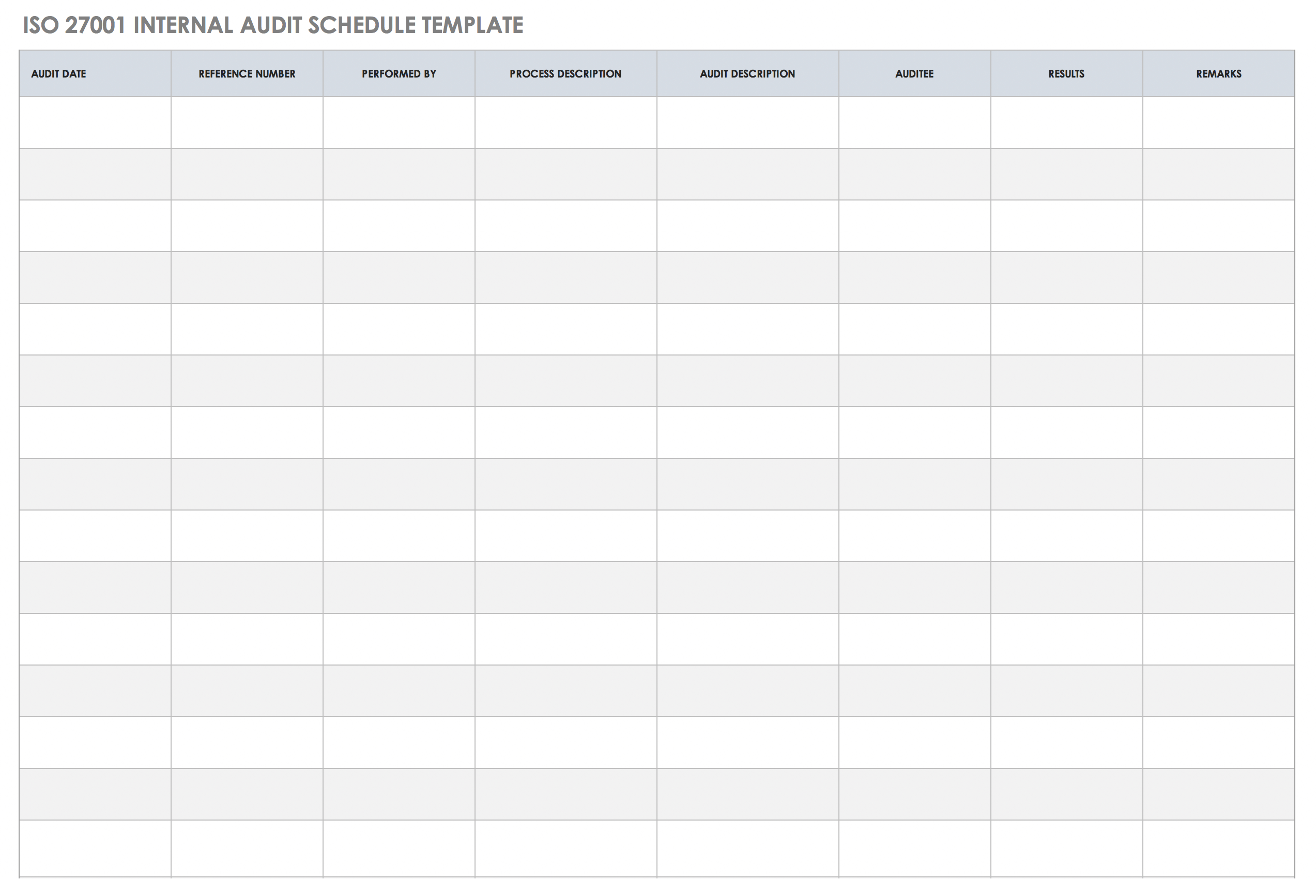
Use this internal audit schedule template to schedule and successfully manage the planning and implementation of your compliance with ISO 27001 audits, from information security policies through compliance stages. Whether your eventual external audit is for information technology (IT), human resources (HR), data centers, physical security, or surveillance, this internal audit template helps ensure accordance with ISO 27001 specifications.
This internal audit schedule provides columns where you can note the audit number, audit date, location, process, audit description, auditor and manager, so that you can divide all facets of your internal audits into smaller tasks. Easily assess at-risk ISO 27001 components, and address them proactively with this simple-to-use template.
Download ISO 27001 Internal Audit Schedule Template
Excel | Word
For more on internal audits, see “ Network Security 101: Problems & Best Practices .”
ISO 27001 Sample Form Template
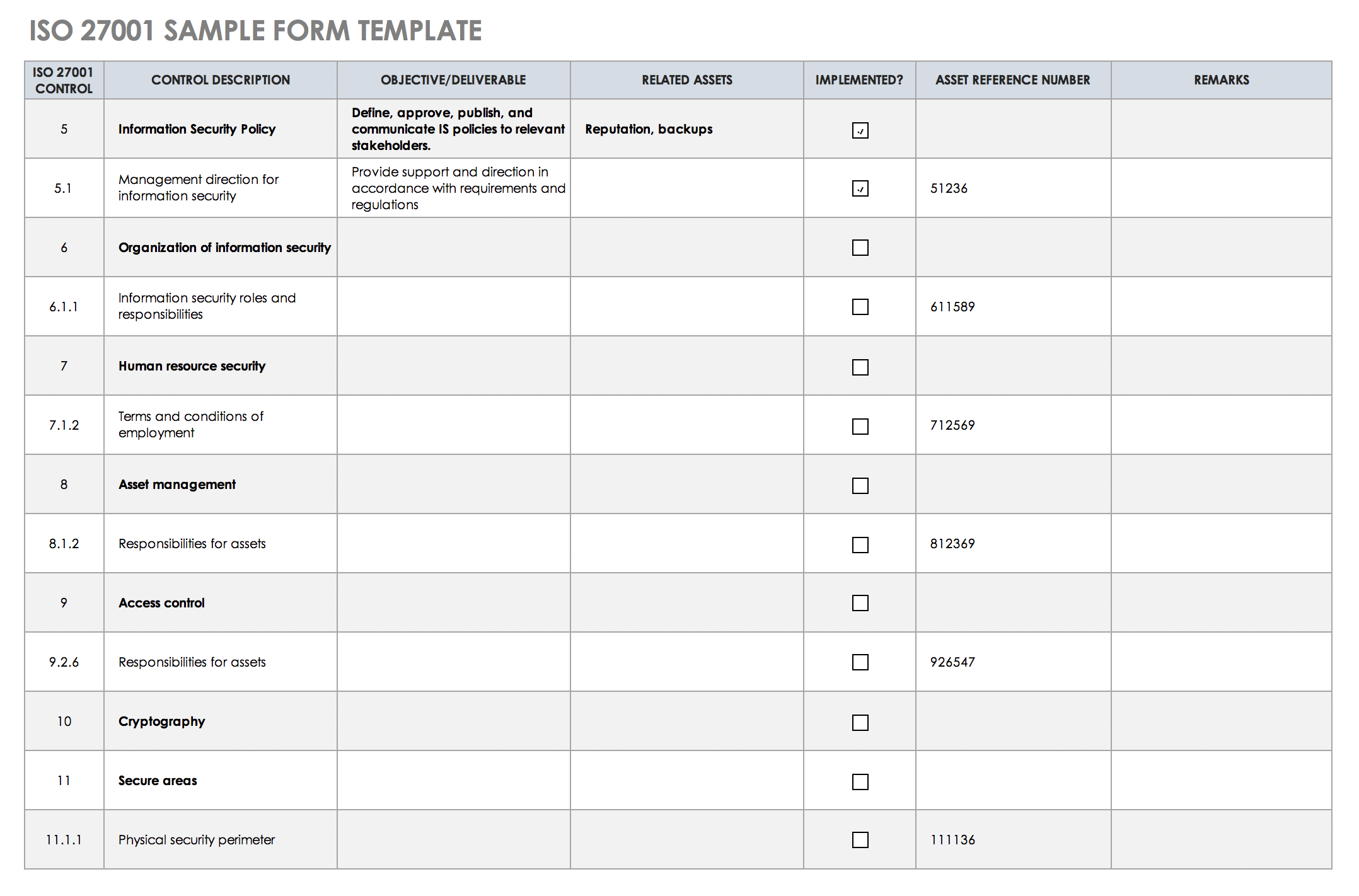
Keep tabs on progress toward ISO 27001 compliance with this easy-to-use ISO 27001 sample form template.
The template comes pre-filled with each ISO 27001 standard in a control-reference column, and you can overwrite sample data to specify control details and descriptions and track whether you’ve applied them. The “Reason(s) for Selection” column allows you to track the reason (e.g., “risk assessment”) for application of any particular ISO 27001 standard and to list associated assets.
You can save this ISO 27001 sample form template as an individual file — with customized entries — or as a template for application to other business units or departments that need ISO 27001 standardization.
Download ISO 27001 Sample Form Template - Excel
ISO 27001 Business Continuity Checklist
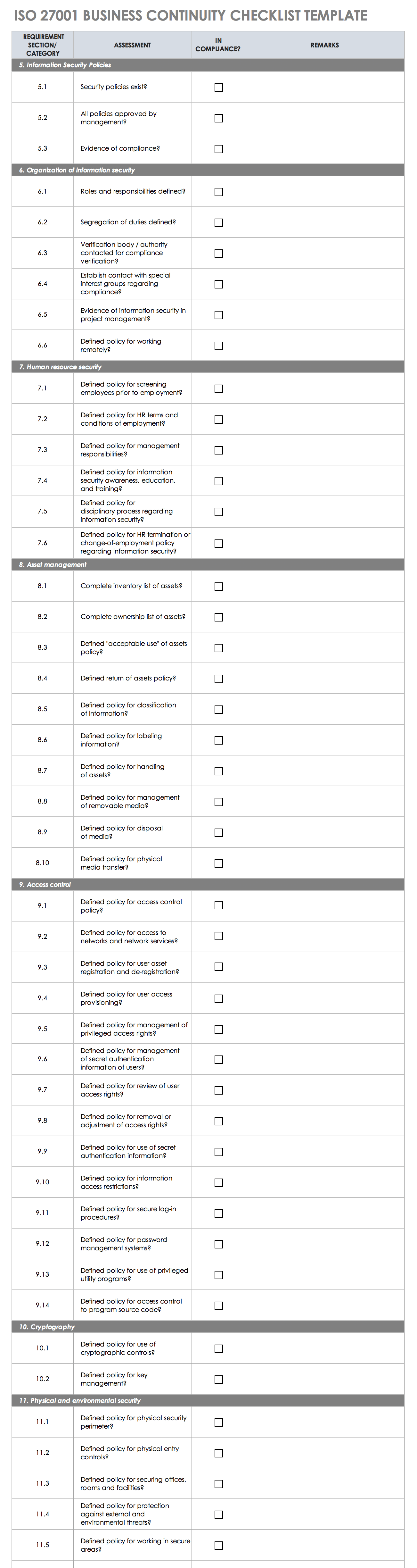
Designed with business continuity in mind, this comprehensive template allows you to list and track preventative measures and recovery plans to empower your organization to continue during an instance of disaster recovery.
This checklist is fully editable and includes a pre-filled requirement column with all 14 ISO 27001 standards, as well as checkboxes for their status (e.g., specified, in draft, and done) and a column for further notes. Use this simple checklist to track measures to protect your information assets in the event of any threats to your company’s operations.
Download ISO 27001 Business Continuity Checklist
Excel | Word | PowerPoint
ISO 27002 Information Security Guidelines Checklist
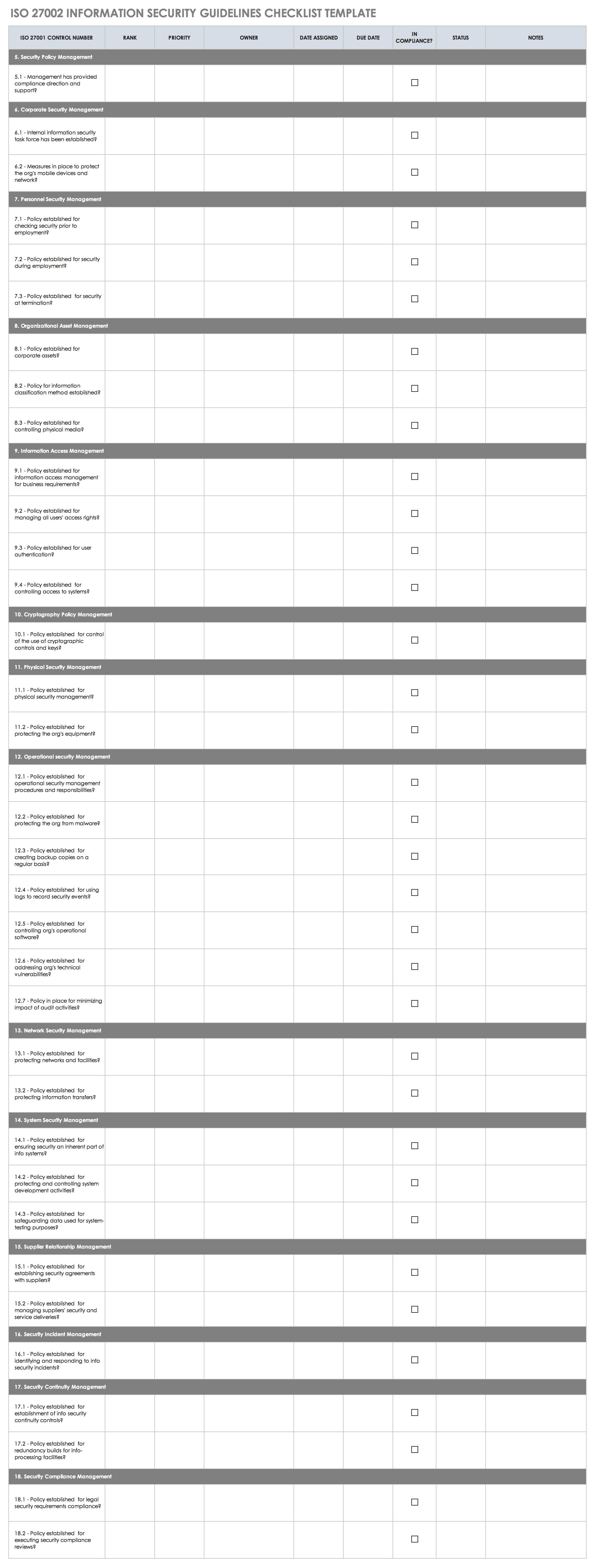
Use this ISO 27002 information security guidelines checklist to ensure that your ISMS security controls adhere to the ISO 27001 information security standard. ISO 27002 provides an overview list of best practices for implementing the ISO 27001 security standard.
This ISO 27002 information security guidelines checklist provides an overview of security controls that should be managed through your ISMS and helps ensure that your controls are organized and up-to-date.
Download ISO 27002 Information Security Guidelines Checklist
The Importance of the IS0 27001 Information Security Standard
The only way for an organization to demonstrate complete credibility — and reliability — in regard to information security best practices and processes is to gain certification against the criteria specified in the ISO/IEC 27001 information security standard. The International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) 27001 standards offer specific requirements to ensure that data management is secure and the organization has defined an information security management system (ISMS). Additionally, it requires that management controls have been implemented, in order to confirm the security of proprietary data.
By following the guidelines of the ISO 27001 information security standard, organizations can be certified by a Certified Information Systems Security Professional (CISSP), as an industry standard, to assure customers and clients of the organization’s dedication to comprehensive and effective data security standards.
In order to adhere to the ISO 27001 information security standards, you need the right tools to ensure that all 14 steps of the ISO 27001 implementation cycle run smoothly — from establishing information security policies (step 5) to full compliance (step 18).
Whether your organization is looking for an ISMS for information technology (IT), human resources (HR), data centers, physical security, or surveillance — and regardless of whether your organization is seeking ISO 27001 certification — adherence to the ISO 27001 standards provides you with the following five benefits:
- Industry-standard information security compliance
- An ISMS that defines your information security measures
- Client reassurance of data integrity and successive ROI
- A decrease in costs of potential data compromises
- A business continuity plan in light of disaster recovery
ISO 27001 and ISO 22301 work together to prevent and mitigate potential problems, especially when it comes to business continuity. To learn more, visit, " ISO 22301 Business Continuity Simplified: Fortify Your Business Against Disruption ."
Up-to-Date ISO 27001 Checklist
An ISO 27001 checklist is crucial to a successful ISMS implementation, as it allows you to define, plan, and track the progress of the implementation of management controls for sensitive data. In short, an ISO 27001 checklist allows you to leverage the information security standards defined by the ISO/IEC 27000 series’ best practice recommendations for information security.
An ISO 27001-specific checklist enables you to follow the ISO 27001 specification’s numbering system to address all information security controls required for business continuity and an audit. It ensures that the implementation of your ISMS goes smoothly — from initial planning to a potential certification audit.
An ISO 27001 checklist provides you with a list of all components of ISO 27001 implementation, so that every aspect of your ISMS is accounted for. An ISO 27001 checklist begins with control number 5 (the previous controls having to do with the scope of your ISMS) and includes the following 14 specific-numbered controls and their subsets:
Information Security Policies:
Management direction for information security
Organization of Information Security:
Internal organization
Mobile devices and teleworking
Human Resources Security:
Prior to employment
During employment
Termination and change of employment
Asset Management:
Responsibilities for assets
Information classification
Media handling
Access Control:
Responsibilities for assets, user responsibilities, and system application access control
Cryptography:
Cryptographic controls
Physical and environmental security:
Secure areas
Operations Security:
Operational procedures and responsibilities
Protection from malware
Logging and monitoring
Control of operational software
Technical vulnerability information systems audit considerations
Communications Security:
Network security management
Information transfer
System Acquisition, Development, and Maintenance:
Security requirements of information systems
Security in development and support processes
Supplier Relationships
Information Security Incident Management:
Information security management
Information Security Aspects of Business Continuity Management
Information security continuity
Redundancies
Business Continuity Management:
Compliance with legal and contractual requirements
Independent review of information security
Improve ISO 27001 Implementation with Smartsheet
Empower your people to go above and beyond with a flexible platform designed to match the needs of your team — and adapt as those needs change.
The Smartsheet platform makes it easy to plan, capture, manage, and report on work from anywhere, helping your team be more effective and get more done. Report on key metrics and get real-time visibility into work as it happens with roll-up reports, dashboards, and automated workflows built to keep your team connected and informed.
When teams have clarity into the work getting done, there’s no telling how much more they can accomplish in the same amount of time. Try Smartsheet for free, today.
Any articles, templates, or information provided by Smartsheet on the website are for reference only. While we strive to keep the information up to date and correct, we make no representations or warranties of any kind, express or implied, about the completeness, accuracy, reliability, suitability, or availability with respect to the website or the information, articles, templates, or related graphics contained on the website. Any reliance you place on such information is therefore strictly at your own risk.
These templates are provided as samples only. These templates are in no way meant as legal or compliance advice. Users of these templates must determine what information is necessary and needed to accomplish their objectives.
Discover why over 90% of Fortune 100 companies trust Smartsheet to get work done.
- Bureaus and Offices
- Contact HRSA
- Site Visit Protocols and Guides
Health Center Program Site Visit Protocol
Last updated: April 13, 2023
The Site Visit Protocol (SVP) is a guide to the operational site visits (OSVs) we conduct at health centers. It includes what we look for and how we assess compliance.
It aligns with the Health Center Program Compliance Manual .
Changes made to the SVP
In 2023, we improved the format of the SVP and made it easier to read. This did not change the way we conduct OSVs.
We stopped assessing the Federal Tort Claims Act (FTCA) portion of OSVs on October 27, 2023. We will continue to assess FTCA risk management and claims management requirements during FTCA-specific applications and site visits.
The FTCA Deeming Requirements section is no longer in use. We will remove it in a future update.
Search Book:
Print the entire Site Visit Protocol (PDF - 1 MB)

Free Site Analysis Checklist
Every design project begins with site analysis … start it with confidence for free!
Site Visit Analysis and Report: How to conduct and evaluate your first architecture site visit
- Updated: January 2, 2024

Here we will cover everything you need to know about of how to approach your first site visit analysis for a new project, what to do when physically there, and how to eventuate and summarize the information you collect.
However before visiting for the first time we highly recommend that you carry out desktop study beforehand, as this will provide an important initial understanding of the site and generate far better results and more refined questions once there.
The desktop study will also help to identify the important items of equipment that you will need to take with you to make your trip as successful as possible. …these are mentioned below but may include a:
- Site map (very important)
- Tape measure
- Laser distance meter
…more essential architects items here

Conducting an architecture site visit analysis
A site visit analysis is a comprehensive report that summarizes the findings of a physical inspection of a potential development site. It includes information on the site’s physical characteristics, location, surrounding area, demographic information, environmental impact, zoning regulations, traffic flow, and recommendations for development.
The report synthesizes all gathered information to provide a comprehensive understanding of the site and its potential.
What to look for?
Once there, there are a whole number of important areas and items that need to be studied and recorded, some of which would have already been identified during your desktop study, but as a starting point we’ve produced the below list of all the key areas:
We suggest that you take these with you and tick them off as they are found, so not to miss anything.
- Entrance and access points (both pedestrian and vehicle)
- Security (gates, surveillance)
- Travelling to the site (road types and suitability, safety, public transport)
- Boundary treatment (fencing, vegetation, land form, water)
- Extent of boundary (does it match the survey/OS map)
- Circulation (existing travel routes within the site)
- Noise levels (quiet and loud areas)
- Services (electric, gas, water, sewage)
- Existing buildings (condition? Relevant? Protected?)
- Existing landscape features (condition? Relevant? Protected?)
- Neighbouring buildings (local vernacular, protected?)
- Views in and out of the site (areas to screen off and areas to draw attention to)
- Tree’s and vegetation (protected and rare species)
- Ecology (any areas likely to be home to protected species)
- Orientation (sun and wind paths)
- Light levels (areas in direct sunlight, shaded areas, dappled light)
- Accessibility (disability access)
- Surrounding context (historical, heritage, conservation area, SSSI, AONB)
- Existing materials in and around the site
- Topography (site levels)
- Flood level (is it likely to flood)
- Soil and ground conditions (types and suitability)
- Existing legal agreements (where are the rights of way, covenants)
- Hazards (Electricity lines, Drainage, Telephone lines, Sub-stations)
We provide a site analysis checklist here covering all of the above that’s free to download.

Where to start
You want to begin documenting your visit as soon as you arrive, as the approach and entrance to your site are just as important as the site itself. If you’re desktop study didn’t highlight the possible routes and methods of transport to and from the site, then this needs to be recorded also.
Documenting your first impressions is vitally important, ask yourself; what do you see as you enter the site? what do you hear? what do you feel? (…what senses are the first to be triggered), you will only get one chance to do this properly and so you need to make it count!
…and don’t forget to include the location of the elements you record, when noting it down on your site map or survey. By the end of your visit, you should barley be able to read whats under all your notes …write down everything!
Moving on from first impressions, you should plan to walk around the site as least twice (as a minimum) to ensure that nothing is missed, so leave enough time to make a least two loops, noting down and photographing everything that you feel is relevant, no matter how small.
…there’s nothing worse than getting back to the studio and realizing you forgot to document something.
We like to use the check list supplied above and:
- Firstly walk around the site whilst annotating a site plan
- Secondly with a camera …photographing everything
- and thirdly with both …just in case something has been missed
This way we can focus on one task at a time, helping to ensure we gather everything we need.
In terms of a camera, and depending on your budget we suggest looking one these three options (but a phone is just as good):
- Sony DSCW800 Digital Compact Camera
- Sony DSCWX350 Digital Compact Camera
- Canon EOS 1300D DSLR Camera
It can be difficult to identify certain elements, and some may only be noticeable from a professional survey, such as underground services and precise spot levels. But approximations of such locations and heights are a good start and can serve as a reminder for further investigation.
If accessible you can of course take your own measurements and so this is where a tape measure and/or distance meter will come in handy.
Try one of these:
– Tape measure
– Laser distance meter
What to take with you
Firstly look at the weather, you wont have a good time if your not dressed appropriately, and this applies to protecting your notes and equipment as well as yourself.
…a simple quick check, can make or break a visit, arranging to go on sunny day will also give you the best site photographs, which could also be used in future CGI’s and presentation material.
If the site is derelict, or has potentially dangerous or hazardous elements, it is likely that you will require personal protection equipment (otherwise known as PPE) so make sure this is organised before setting off.
As a minimum you want to take with you a camera, a pen and an OS map. Google Maps can provide a temporary (though very basic) version, but a much preferred scaled version that can normally be obtained through your university or practice via such companies as:
- Digimap – digimap.edina.ac.uk
- Xero CAD – xerocad.co.uk
- CAD Mapper – cadm a pper.com (free account available)
As mentioned, you will want to make notes, and record everything you observe, experience and hear all over this map. So print out a couple of copies at a usable and convenient size.

A camera is essential in documenting the site, and the pictures taken during your visit are likely to be used on a daily basis throughout your project. So once again make sure you document and record everything.
Pictures should be taken from all distances, close zoomed-in sections of materials and textures along with shots of the site from a distance to include the area as a whole and within its context.
Note pads are important for obvious reasons, we prefer an A5 sized pad, as this is much easier to carry and hold than an A4 one.
Tape measures can be useful, but we never go on a site visit without a distance meter.
…and lastly if you’re visiting on your own, don’t forget to tell someone where you’ll be and take your phone with a charged battery.
Our site visit equipment check list looks something like this:
- Weather check
- Print out our “what to look for” checklist
- Site map (at least 2 copies)
- PPE equipment
- Scale ruler
If you are interested in trying our architecture site analysis symbols for your own site analysis recordings and presentation, then head over to our shop ( Here ).
FAQ’s about site visit analysis
What is included in a site analysis.
As discussed above, site analysis typically includes the following elements:
- Site location and context: Understanding the location of the site in relation to the surrounding area, including climate, topography, neighboring buildings, and accessibility.
- Physical characteristics: Examining the site’s physical features, such as its size, shape, soil type, vegetation, and water sources.
- Utilities and infrastructure: Assessing the availability of utilities such as electricity, water, gas, and sewer, as well as the infrastructure, such as roads and transportation.
- Environmental considerations: Analyzing the site’s potential environmental impact and assessing any potential hazards, such as flooding or soil stability.
- Zoning and land-use regulations: Reviewing the local zoning and land-use regulations to determine the types of uses and development allowed on the site.
- Cultural and historical context: Examining the cultural and historical significance of the site and its surrounding area.
- Demographic information: Analyzing the demographic information of the surrounding area, including population, income, and age.
- Traffic and pedestrian flow: Studying the flow of vehicular and pedestrian traffic in the area to understand the impact on the site.
This information is used to inform the design of a building or development project, taking into account the unique characteristics and constraints of the site.
What are the steps of site analysis?
including the above, the steps involved in conducting a site analysis report typically include:
- Data Collection: Gather data and information about the site, including maps, aerial photos, zoning regulations, environmental reports, and other relevant documents.
- Site Observations: Conduct a site visit to observe and document the site’s physical and environmental conditions, such as topography, vegetation, water sources, and neighboring buildings.
- Context Analysis: Analyze the site’s location and context, including its surrounding area, access to transportation, and cultural and historical significance.
- Demographic Analysis: Study the demographic information of the surrounding area, including population, income, and age, to understand the potential market for the development project.
- Traffic and Pedestrian Flow Analysis: Study the flow of vehicular and pedestrian traffic in the area to understand the impact on the site.
- Synthesis: Synthesize the information gathered in the previous steps to develop a comprehensive understanding of the site and its potential.
- Recommendations: Based on the analysis, make recommendations for the development of the site, taking into account the unique characteristics and constraints of the site.
These steps help architects and planners to gain a deeper understanding of the site and to make informed decisions about the design and development of a building or project.
Every design project begins with site analysis … start it with confidence for free!.
Leave a Reply Cancel reply
You must be logged in to post a comment.
As seen on:

Providing a general introduction and overview into the subject, and life as a student and professional.
Study aid for both students and young architects, offering tutorials, tips, guides and resources.
Information and resources addressing the professional architectural environment and industry.
- Concept Design Skills
- Portfolio Creation
- Meet The Team

Where can we send the Checklist?
By entering your email address, you agree to receive emails from archisoup. We’ll respect your privacy, and you can unsubscribe anytime.
Elite Integration
We are experts in creating consistent security ecosystems across locations, consolidating stand-alone solutions, and avoiding disparities.
Fanatical Customer Service
We take customer care seriously — in fact, we are fanatical about supporting you and supplying the solutions your business needs as soon as possible.
Technology Partners
Security 101 maintains long-standing strategic partnerships with the security industry's leading manufacturers.
Our portfolio of services is provided by a team of skilled and qualified experts, who have in-depth knowledge of security principles and processes, a comprehensive understanding of your vertical, experience in developing intricate projects, and adherence to Security 101’s core values of fanatical customer service and integrity.
Industry Solutions
Security solutions, situational awareness, all services.
We are customer-centric. You are at the center of everything we do.
Select a location near you

Jan 15, 2021 |
Physical Security Audit & Assessment Checklist | Security 101

What is a Physical Security Audit and Why You Need One
Should you get a physical security site assessment.
A good physical security solution isn’t one-size-fits-all. Every space and building is unique, and security needs change over time. In today’s buildings, security systems need to protect the perimeter, as well as safeguard the sensitive data and information that’s constantly in motion. So even if you’ve installed security systems in the past, they may not meet the current standards for protection.
Don’t wait until after a breach has occurred to evaluate your physical security. A site assessment with a trained security professional can help you improve the safety of your building by uncovering weak points in your current system, and identifying the right technology to safeguard your space. Contact your integrator and review this checklist together to determine your risk level, and discuss ways to mitigate potential threats to your building security.
1) Identify potential security threats
Knowing what you need to protect against will help you identify the best security technology for your building. The most common security threats to businesses include:
- Theft and vandalism
- Insider breach involving sensitive data
- Negligent data management
- Phishing attacks
- Physical attacks
2) Access control for physical building security
Having a good access control system in place is essential to protecting your assets, as it helps keep unauthorized individuals from gaining entry. The fact that many data breaches actually occur in conjunction with a physical breach only highlights how important access control is in securing your building. Access control comes in many different forms, from security guards at the door, to ID badges, to more advanced access technology like smartphone-based credentials. Whether you have an existing access control system, or are installing a brand-new security solution, this security audit checklist will help determine what types of credentials and capabilities are right for your space.
- Analyze all entry points to detect vulnerabilities. Note how many doors need to be protected, and how many people will need access on a regular basis.
- Determine if different permission levels will be needed for certain zones. Make sure the access control system you install has the functionality to set granular permissions per user and location.
- Install door readers at places where you want to limit who has access.
- Choose credentials that are secure and convenient. Mobile credentials have the added benefit of visual verification with digital badging, eliminating the need to carry an ID card.
- Use door schedules to automate your security. For example, set a lobby door to remain open during business hours when there’s a front desk person on duty, and set it to automatically lock and require users to credential in after-hours.
- Choose a cloud-managed access control solution to enable remote access to your security platform. Without the need to be on-site to unlock the door, issue credentials, or change the door schedules, cloud-based access control reduces headcount without compromising security.
3) Surveillance and intrusion detection
If somebody enters the building who isn’t supposed to, how will you know? Especially after-hours when there’s nobody at the building, or during minimal staffing shifts, video surveillance systems and alert systems can help prevent a security breach.
- Install video surveillance cameras at key entry points throughout the building, and anywhere that you need an extra set of eyes. Consider both exterior and interior spaces, including parking garages, IT closets, and spaces where sensitive data might be stored.
- Integrate the VMS with your access control system for enhanced visibility. This lets you associate video footage with entry activity, often in real-time, enabling a faster and more accurate response to situations in your building.
- Certain industries have specific retention standards for security camera footage, so check your local regulations to make sure your system is compliant.
- Set up automatic alerts to notify you of any malicious activity or potential intrusions.
- When door sensors are triggered, a mobile access control system can send out an alert for doors left ajar, a forced entry, or failed unlock attempt.
- Other sensors, such as glass breaking or gunshot detection, can further enhance your building security.
4) Environmental components
Physical security isn’t just guards at the door and alarms. Natural elements, like landscaping, can aid (or hinder) your building’s security. Here’s what to look for as you complete your physical security risk assessment.
- You should be able to clearly see entrances and exits from inside the building. Make sure there’s nothing blocking windows, such as displays, signage or landscaping.
- Install exterior lighting in all parking lots, near entrances, and around pathways. Well-lit grounds can help deter potential criminals.
- Keep interior lights on at night and when the building is empty to deter intruders. For improved efficiency and sustainability, install a lighting system that’s integrated with building management platforms and access control to automatically adjust based on occupancy, the weather, and business hours.
- Make sure trees and bushes are well-maintained around the property.
5) Emergency response readiness
As part of your physical security audit, always check emergency response systems. Your physical security strategy should also include emergency situation planning,
- Ensure you have all necessary alarms per building codes, and that they are tested regularly.
- Create customized lockdown plans for different emergency scenarios. With an access control system like Openpath, you can activate Lockdown plans remotely, directly in the app for a faster response time.
- Install backup power sources for your security systems in case of a power or Internet outage to keep your building secure.
6) Physical security assessment for COVID-19
As a prime example of how quickly security needs can shift, the COVID-19 pandemic presented a new set of challenges for every organization. Use this security audit checklist to determine if your building has the right strategies in place to remain safe and secure during the pandemic.
- Choose security technology that can be managed remotely to minimize the staff needed at the building, and improve visibility without being on-site.
- Utilize occupancy management to adhere to social distancing guidelines. Some access control companies are able to automate and enforce occupancy limits, with real-time occupancy tracking dashboards to keep administrators informed.
- Reduce common touch points with contactless technology. Touchless access control lets people unlock doors and enter the building without having to touch a common reader or credential.
Key takeaways
Taking the time to do a thorough security risk assessment is a proactive step in protecting your building and assets. Whether you’re auditing a small space or performing a physical security risk assessment on an enterprise organization with multiple locations , this checklist can help you pinpoint where your security may be lacking.
Choosing new security technology can be a daunting investment with so many options to choose from. When comparing different solutions, remember that a one-size-fits-all approach to security can leave your building vulnerable, so opt for systems that allow for customizations and seamless integrations to get the best protection possible. While this security audit checklist is a great place to start when it comes to understanding your risk, a security system professional can do a more thorough site walk and recommend the best solutions to ensure your building is protected from all types of threats.

Corey Tyriver
Share post on:
COVID –19 Compliant as a New Year's resolution
Foolish criminals on cctv: the significance of video surveillance for a business.

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
Free Cyber Services #protect2024 Secure Our World Shields Up Report A Cyber Issue
Security Assessment at First Entry
Description.
SAFE is a rapid physical security assessment that assists facility owners and operators in implementing effective security programs. Using SAFE, CISA Protective Security Advisors (PSA) provide a structured review of a facility’s existing security measures and delivers feedback on observed vulnerabilities and options for improving security.
Sign up for CISA's Physical Security Assessment through Your Regional Office. Request a SAFE assessment by reaching out to your local CISA field staff or emailing your regional office.
Contact Your Regional Team
After completing the SAFE visit, the PSA delivers a short report containing:
- A list of existing good practices to sustain: During the assessment, the PSA will make note of existing good practices that are effective and a stakeholder should continue doing.
- A list of vulnerabilities and mitigation options for consideration: The PSA will note any areas that could benefit from additional security mitigation measures. For each identified vulnerability, the assessment will provide one or more mitigation options for owners and operators to consider. These options are purely voluntary, and each facility determines what actions to take given its unique considerations and operating constraints.
- A list of important security points of contact: Who facility owners and operators can reach out to in order to improve a facility’s security posture and readiness.
- Helpful links and references: Resources that provide more information about security options and ways to implement them.
Additional Information
Download a printer-friendly fact sheet for the Security Assessment at First Entry.
Contact Information
To learn more about SAFE assessments, please contact [email protected] .
Related Services
Assist visits, rapid survey, emergency services sector active shooter workshop, infrastructure survey tool (ist).

Manage the Complete Vendor Lifecycle
Easily manage your third-party risk management activities across the vendor lifecycle – onboarding, ongoing management, offboarding.
Take a Product Tour to See Venminder in Action New

Outsource Vendor Control Assessments
Order due diligence assessments on your vendors that include qualified risk ratings and reviews from Venminder experts.

Continuously Monitor with Risk Intelligence
Seamlessly combine risk intelligence data to monitor for risks within cybersecurity, business health, financial viability, privacy, ESG and more.
Venminder experts deliver over 30,000 risk-rated assessments annually. Download samples to see how outsourcing to Venminder can reduce your workload.
Download free samples →
- Create Your Free Account
Quickly get a program in place to manage vendor risks.
Centralize to ensure program requirements are met.
Identify risk then reduce and manage it.
Hand off your document collection, control assessments and tasks.
Meet regulatory agency issued guidance.
Empower vendor owners to mitigate vendor risks.
Risk Categories
Why venminder.
Learn how our customers have managed their vendors and risk with Venminder.
Check out independent research that validates Venminder's market leader position.
See why Venminder is uniquely positioned to help you manage vendors and risk.
Our team is committed to a single goal: a customer experience second to none.
We offer quick and customer-focused implementation for fast ramping.
Learn how to advocate the importance of budget for third-party risk management.
Learn how Venminder helps companies of all sizes and within all industries.
Download complimentary resources to guide you through all the various components of a successful third-party risk management program.
Read Venminder's blog of expert articles covering everything you need to know about third-party risk management.
Earn CPE credit and stay current on the latest best practices and trends in third-party risk management
Register for upcoming webinars →
Watch on-demand webinars →
Join a free community dedicated to third-party risk professionals where you can network with your peers.
Download samples of Venminder’s vendor risk assessments and see how we can help reduce the workload.
Receive the popular Third Party Thursday newsletter into your inbox every Thursday with the latest and greatest updates.

Venminder's State of Third-Party Risk Management 2024 whitepaper provides third-party risk management insight and industry statistics to help you make informed programs decisions. Learn how others are managing third-party risk.

Venminder is the industry's leading third-party risk management solution provider.
Leadership →
We're hiring! Explore career opportunities and learn more about Venminder culture.
Check out the select partners we aligned with to provide additional solutions and services.
Learn how to become a Venminder integration or referral partner.
See how Venminder can enable you to run an efficient third-party risk program.
Get in touch with a member of your team to discuss a question you may have.
Already a Venminder customer? Connect with the Customer Support Team.

Read More →
Gain a 360-degree view of third-party risk by using our SaaS software to centralize, track, automate, assess and report on your vendors.
- New Vendor Onboarding
- Contract Management
- Risk Assessments
- Questionnaires
- Oversight Management
- Oversight Automation
- SLA Management
- Issue Management
- Advanced Workflows
- Business Unit Permissions
Venminder Exchange
- Integrations
Vendor Risk Assessments
Venminder's team of experts can review vendor controls and provide the following risk assessments.
- Initial Vetting Packages
- Financial Health Assessment
- SOC Assessment
- Business Continuity/Disaster Recovery Assessment
- Point-in-Time Cybersecurity Assessment
- Data Protection Assessment
- Information Security and Privacy Assessment
- Contract Compliance Assessment
- Regulatory Compliance and Operational Assessment
- CAIQ Assessment
- SIG Lite Assessment
Managed Services
Let us handle the manual labor of third-party risk management by collaborating with our experts to reduce the workload and mature your program. Overview Document Collection Policy/Program Template/Consulting Virtual Vendor Management Office Vendor Site Audit
Ongoing Monitoring
Let us handle the manual labor of third-party risk management by collaborating with our experts.
- Business Health Monitoring
- Cybersecurity Monitoring

As Venminder completes assessments for clients on new vendors, they are then made available inside the Venminder Exchange for you to preview scores and purchase as you need.

Learn more on how customers are using Venminder to transform their third-party risk management programs.
- Getting started
- Increase program efficiency
- Effectively mitigate vendor risks
- Reduce the due diligence workload
- Comply with regulations
- Drive collaboration across your org
Venminder is used by organizations of all sizes in all industries to mitigate vendor risk and streamline processes
- Financial Services
- Manufacturing
- Real Estate
We focus on the needs of our customers by working closely and creating a collaborative partnership
- What makes us different
- Customer success stories
- Quick implementation
- Commitment to customer experience
- Pricing packages
- Independent research
- Partners & Endorsements

Sample Vendor Risk Assessments
Venminder experts complete 30,000 vendor risk assessments annually. Download samples to see how outsourcing to Venminder can reduce your workload.

Trends, best practices and insights to keep you current in your knowledge of third-party risk.
- Infographics
- Industry Interviews
- Whitepapers
- Sample Work Products
Earn CPE credit and stay current on the latest best practices and trends in third-party risk management.
See Upcoming Webinars
On-Demand Webinars
Join a free community dedicated to third-party risk professionals where you can network with your peers.
- Join Community
Weekly Newsletter
Venminder samples.
Download samples of Venminder's vendor risk assessments and see how we can help reduce the workload.
- Download Samples

State of Third-Party Risk Management 2023!
Venminder's seventh annual whitepaper provides insight from a variety of surveyed individuals into how organizations manage third-party risk today.

Manage the complete vendor lifecycle - onboarding, ongoing management, offboarding.
Order due diligence assessments on your vendors that include qualified risk ratings and reviews.
View Packaging and Pricing ➔
Reduce the workload with customized outsourced services (eg: document collection).
Monitor for risks within cybersecurity, business health, financial viability and more.
Shorten the sales cycle by becoming due diligence ready for prospects and customers.
Access a free library of thousands of vendor risk assessments available for preview and purchase.
Download free samples ➔
Vendor Site Visits
Whether it's in-person or virtual, site visits can provide you with a point-in-time assessment of your organization's critical or high-risk vendors and answers to remaining questions.
In partnership with assurance, accounting, tax and consulting firm, Wipfli, we've put together this handy checklist and infographic to ensure your organization understands how to properly conduct them.
Download the checklist and infographic to learn:
- What to do in each stage of a site visit from planning to concluding
- Why site visits matter
- When to conduct a site visit and example scenarios

Download Now

Workplace Security Inspection Checklist (49 Essentials To Include)

Last week, at work, my colleagues and I received an e-mail from the Security and Operations team, reinforcing security protocol to be followed in the office and emphasizing the need to stay alert to remain safe. This made me think of all the security measures the security department must have to consider, and made me wonder about the specific guidelines and checklist they have to follow.
So, what does a workplace security inspection checklist comprise? It is a set of guidelines and verification questions around all aspects of security in the workplace, meant to regularly check compliance with safety regulations and to keep security policies up to date. A good checklist covers employee personal safety, safety from hazards and from external threats.
Workplace security inspection is an important component of maintaining and improving the existing security system in place. A workplace security inspection checklist helps in pointing out those areas that require immediate attention and in testing out newly implemented security measures as well. The checklist itself must be updated from time to time with changing requirements. Generally, such checklists are created keeping in mind factors such as the country’s workplace safety regulations, location and type of space the office is in, the kind of work done in the office, etc.
.png)
Creating a workplace Security Inspection Checklist – The Process
While creating an ideal security inspection checklist for the workplace, it is important to consider company policies and regulations. The existing security system and protocol for physical as well as cyber security has to be studied and analysed carefully before creating the checklist. Moreover, it might be advisable to have conversations with employees from all levels, especially managers, on the current security measures and how they think these may be improved. It is also wise to remain updated with improving and newly developed security measures such as alarms with sensors, specialized locking systems, automatic doors, etc.
Also, there is the need to assess the kind of information employees possess at the moment of the security system in place, so that the checklist can also be prepared accordingly. Most importantly, while creating the checklist, one should think from the viewpoint of someone visiting the office for the first time, someone who has no prior awareness of such things as the locations of the emergency exits, the entry/exit protocol, etc. That way the checklist will be more thorough and will examine the security system completely.
Once the checklist is made, the inspection can begin. As the inspection proceeds, the team in charge will come across the flaws in the system and will be able to start making the necessary improvements. There are several security audit agencies these days that do a good job inspecting the office security thoroughly and then provide detailed feedback.
49 Essentials to Include in a Workplace Security Inspection Checklist
There are myriad factors that must be kept in mind to create the perfect security inspection checklist. The duty of a security inspector is not easy as they have to take into consideration so many aspects of security and safety, and it is not possible for them to remember all of these by heart. Thus, the checklist must include everything related to the security system of the office, so that all grounds are covered. It is necessary that the security inspection checklist should be shared not just with the concerned team, but also with all the people working in the office, to ensure maximum compliance to, and understanding of the protocol. Here are 49 points that must be included in every workplace security inspection checklist-

2. Next, it is important to ask about monitoring and surveillance. While different workplaces have varying rules regarding privacy and monitoring, it must at least be ensured that entry and exit points must be kept under CCTV surveillance 24/7.
3. Additionally, the checklist must ask about monitoring of cyber systems and all areas of restricted access, as it is important that no unauthorized person should be able to enter these. If not by CCTV surveillance, the checklist should ask if these areas are supervised and patrolled continuously by trained security personnel.
4. Along with this, the checklist should include questions regarding stairways and halls as well. It should be ensured that these spaces where people walk through frequently are free of obstruction in the form of storage boxes, wires, etc.
5. The checklist must question the level of access from outside the office, as well as within the organization. What is the procedure an outsider follows to enter the office? The checklist must include practices such as taking names, details and ID proof of outsiders coming into the office along with verified purpose of visit. If any external agencies such as repair persons and utility staff enter the office premises, their credentials must be verified between the office and the agency.
6. An important question to ask in the checklist regarding access within the company and hence within the office, is about employee identification. The necessary information pertaining to every employee along with a clear photo ID should be available on the company’s database for the security team to peruse when they may need to. Internally, the checklist should ask about the different levels of employees and which level has access to what kind of information and/or access to physical parts of the premises.
7. Regarding employee identification, the checklist must also ensure that employees have ID cards and/or badges that are distinctive and only these can allow the employees access to the office premises and to restricted access locations within. The checklist should also ask about the use of magnetic strips in the ID cards to automatically allow entry, and that such cards are withdrawn from employees after they exit the organization.
8. The checklist should also focus on the aspect of employee training with regards to security and safety. Are all the employees properly trained to assess security threats and protect themselves as well as each other against them as best as possible? For example, are employees trained on what to do in case of a fire? Have employees been briefed on cyber security protection measures and are aware of simple things they can do for safety, such as locking their belongings, shredding confidential papers after use, etc?
9. The checklist must ask about alarm systems. Does the office space, including parking lot, entry, exit, emergency exit and restricted access area, have a functioning alarm system installed? In case of intruders by any chance, such an alarm system will come in use and should be up to date. Fire alarms should also be functional and installed over the office space.

10. It is advisable for the checklist to ask about lighting systems and functionality, particularly in potentially risky areas of the office premises, such as the parking lot. It should be checked that the lighting in such zones is fully functional, not prone to flickering or dying out and is adequate to see well.
11. One highly important part of the checklist must be devoted to the presence and storage of hazardous and potentially dangerous items/material in the office space. Are flammable items marked as such and stored carefully in designated storage to ensure safety? Do utility staff who may work with or near dangerous material have awareness of the hazard and are trained to handle it?
12. It should also be ensured that hazardous material should be kept in secure and locked storage locations where any sort of leakage or spill can be contained easily. The checklist should ask about the measures taken to mitigate the damage caused by such incidents. Further, at workplaces where such materials are in proliferation and stored in large quantities, ideally a list should be available detailing the properties and use of each substance to prevent any form of confusion. This storage should be extremely restricted access in nature to avoid terrible accidents.
13. The checklist should ask about the entry and exit points of the office. Apart from being under surveillance and security guard patrolling, are these areas free from obstruction so people can come and go safely? Are exit doors, particularly emergency exit doors, marked properly and clearly? Are emergency exit signs lit up and devoid of malfunctioning in any way?
15. Stairwells and stairs themselves should be part of the checklist. The checklist should ask if the stairs and walkways are maintained properly and the flooring is in good condition to avoid incidents of people tripping and falling. The inspection should also check if the hand railings of the stairways are properly secured and are present in every stairway.
16. The flooring of the office is another important part of the checklist. The checklist must ask questions regarding the general condition of the floors- are there cracks, damp spots, snags in carpeting, etc, that could be potentially harmful to people walking? Is the flooring slip-resistant and are carpets places properly to avoid slippage? It must also be ensured that dangerous substances such as oil, grease and even water are not spilled across floors, stairs and walkways.
18. Apart from storage of hazardous materials, general storage should also come under the checklist. Are the cupboards and storage cabinets in good condition, with door hinges functioning properly? The sturdiness of storage cabinets should also be checked and ensured that each storage facility contains materials of weight and type, which is meant to be stored in it.
19. The checklist must ask if every item to be stored has an appropriate demarcated spot to be stored in. The storage space should be adequate, not overloaded or overstuffed and not underutilized either. It is equally important to check if the stored material is secured in place to prevent it from slipping, sliding or shifting and consequently spilling out of storage the moment it is opened.

20. Additionally, the checklist must ask if the storage areas are kept clean and free of unnecessary or waste items. The storage must also be organized categorically, which the checklist must ensure.
21. In case of high storage spaces and cabinets, the checklist must ensure that heavy items are not stored at the top as they may fall directly on the head, arms or shoulders of employees and cause injury. Heavy items should be stored at lower height levels for safety. In case the shelves are very high, the checklist must ask what means the company has provided for employees to access such spaces, and if the means are safe.
22. It must be ensured that racks of any sort are arranged carefully so that they don’t have the risk of falling over and causing damage. Fragile items such as those made of glass and breakable material should be kept in secure, immovable spaces.
23. The next aspect a workplace security inspection checklist must cover is lighting and ventilation. Other than parking lot lighting, office lighting is also important. Employees need different kind of lighting for differing purposes, so the checklist must ask about the quality of bulbs used in the offices, particularly over the workstations- is the light LED, and if so, what is the saturation level, and so on. It must be ensured that the lights are all functioning well, not flickering and not going out without reason. The fittings of the lights should also be checked under the inspection. The checklist should ask about reflective glare caused by any lights and also about the maintenance of cleanliness of bulbs and lights.
24. The checklist should inspect the level of ventilation in the office space. Is there enough balance between the air conditioning and/or fans inside and the fresh air outside? Is there enough natural lighting entering the space? The checklist must also ask about the temperature control of the office- whether there is a central system that governs air conditioning/heating and other factors such as humidity, movement of air, and so on.
25. Another necessary aspect to check on is the presence, use and maintenance of electrical equipment in the office. It should be checked that all cables, cords, extensions, sockets etc are in good condition- not torn or exposed. The checklist should ensure that all switches and switchboards are in perfect working condition and none of the switches cause electrical shock or static. It must be checked whether all electrical equipment such as computer systems and other machinery are in good condition and have been maintained as per regulations.
26. For the safety of utility staff who assist with transportation of goods, machines etc, the checklist must ensure that all equipment used to lift/carry/transport are in top condition and are not likely to fall apart. It should also ask that the staffs that use such equipment are adequately trained to do so.
27. The checklist should define the top parameters based on which equipment may be tagged and reported as faulty. It should check if there is such a system in place to report faulty equipment, and if so, what the process for the same is.
28. In terms of appliances and equipment, it is also necessary for the checklist to raise points about the maintenance and cleaning of electronics such as the refrigerator, microwave, kettle, coffee machine, if these are available in the pantry/cafeteria. It should be checked that such appliances are cleaned regularly and are in good working condition.
29. When equipment is considered, it should be checked if items such as photocopiers, printers, shredders, laminators, etc are kept in good condition and are preferably located a bit away from the workstations to avoid disturbing the employees as they work. Additionally, the checklist should question if sound-protection from noisy machinery or equipment is being used by the office. It should be checked that employees are aware of the correct procedures to use such equipment.

30. With regards to facilities for the staff, there must be a separate section in the checklist. The checklist must ask if the washrooms are adequate in number as per the number of employees and that these washrooms are kept clean. The cleanliness standards of the washrooms should be checked with respect to the kind of thorough cleaning that should be done, and the quality of material used for cleaning.
31. It should be checked that the flow of water in the flush of the toilets, in the taps and handheld showers, is proper and regular, and that hot and cold water taps are marked distinctly. The checklist should include questions about the presence of proper disposal bins and sanitary napkin disposal machines as well. It should be checked that waste in bathroom dustbins is cleared regularly.
32. The checklist should enquire about the presence of a well-stocked first-aid kit in the office premises, preferably one in each separate part of the office. The first-aid kit should contain at least the minimal required items such as antiseptic, surgical tape, cotton wool, anti-inflammatory cream, etc., if not, more specialized medicine. The contents of this medical box should be refreshed as and when required and items stocked when needed.
34. It is necessary for the checklist to enquire about the fire extinguishers placed in and around the office. There should be one extinguisher per distinct area and the checklist should ensure that these are in working conditions, are tested regularly for functioning, and that all employees are aware of how to use these if the time comes. Alongside, fire alarms and signs must also be tested out regularly to ensure their functionality.
36. Also important to check is the re-entry process after an evacuation drill. Employees need to be aware of exiting as well as entering the office correctly after such a situation. The checklist needs to ask about this process as well.
37. The workstations and seating arrangements for employees is also an important part of security inspection. The checklist can ask questions regarding the height of the work desk, the comfort and quality of the chairs provided, whether the chairs are adjustable and revolving in nature, etc. Further, points can be raised about the amount of space each desk offers and whether that space is enough for the tasks to be done.
38. Spacing of the workstations also concerns spacing around and between the desks. Do the employees have reasonable space to move around without dashing into something and potentially hurting themselves? On the other hand, the checklist should also focus on whether there is any unused space which can be utilized better.
39. The list must confirm if there is enough storage space with each workstation. Additionally, it must see if the drawers, cabinets and bins are arranged properly and not in such a way that they obstruct movement or take up too much space. There should be a waste bin with each desk space, and it should be emptied on the regular.
40. It will be useful if the checklist asks additional questions about the optimization of the workstation- whether document holders and similar items are present, and if employees have been briefed on organizing their desk spaces well.
41. The checklist should also deal with housekeeping facilities and competence. It should be checked that staff members who work for housekeeping work regularly to keep the workplace tidy and in aesthetic condition. The checklist should also see if housekeeping staff are aware of basic rules and regulations, such as what cleaning material to use on which surface, avoiding disturbance of employees’ personal belongings on their desk, etc.
42. Security is also concerned with the well-being of the employee, both mental and physical. Thus, the checklist must have points regarding whether the computer is located at an appropriate distance from the employee when at the desk, whether anti-glare is used, if the height and angle of the screen is optimized, etc. The height and positions of the chairs should be adjustable, as should the monitor of the screen.
43. When it comes to inspecting internal and personal security, the checklist must ask if employees are aware of such norms as code of conduct, what constitutes personal and professional violation, sexual and racial discrimination, and so on. Detailed documentation must exist on all these grounds, along with procedures on how to complaint or raise an issue if an employee faces any of this at work.
44. Since security also entails taking care of the employee’s personal well-being and ensuring that they have complete peace of mind at the workplace, the checklist may include the provision of mental health avenues for employees. For example, is there a part-time counsellor or therapist who comes in once or twice a week to provide mental support and guidance to employees? Is there a game/recreation room in the office to help employees unwind?
45. The checklist should ask if regular feedback is taken from the employees on their perceptions of how safe and secure they feel at the workplace. Are employees asked to submit anonymous feedback on whether they find cyber and physical security measures adequate? Do they find the workplace a safe and nurturing space to grow professionally and personally?
46. Cyber security is an increasingly important component of workplace safety now. It can be easy for hackers and malicious intentioned persons to break into the organization’s network, so the inspection checklist must outline factors that safeguard against such a security breach. The checklist must ask if there are strong firewalls in place, blocking outsider entry into the company network. It should be enquired if the company has a cloud based control system in place; as such a system is the best protection against external threats.
47. Employees should also be trained to be wary of how they share information online, such as verifying if a certain person sent an important email, not opening suspicious websites or links, and so on. The checklist should also ask if any instances of unauthorized access or attempts of such access are reported immediately and taken action against. It should also be checked what such preventive/protective action entails.
48. It should include points about employee training and orientation on various fronts. For example, are new employees trained on their job and assigned a mentor to guide their progress? Is there a specific set of guidelines pertaining to employee orientation and on-the-job training, and if so, is this document readily accessible and available to all? When an employee is assigned a new job role or responsibility, is fresh training carried out for their growth as well? The checklist should ask if new employees are briefed on everything about the company, their specific job roles, the company culture, prospects of growth, policies such as attendance, hierarchy, dress code, etc. There must be a separate training session for every new task, role and position in the company as well as an orientation every time new technology, equipment/ processes are introduced that the employees are going to use.
49. One of the most important elements of security is transparency and flow of information within the system and a solid wall blocking the contents of this system from external threats. Thus, the checklist should confirm if the designated people within the organization, such as IT and security department, are able to access the security and surveillance (cyber and physical) system required. On the other hand, the system must be sealed tight so that outsider breach is prevented and at worst, detected and combated as quickly as possible.
Related Questions
How can cyber security be further enhanced in a large organization? To protect their data from malicious intruders, employees are encouraged to create strong, customized passwords with symbols and numbers, avoid writing down security keys and such passwords, check email IDS carefully before sending important info and store flash drives, etc in locked spaces.
What measures can employees take to safeguard themselves further at work? It is suggested that employees be alert and practise the buddy system when working late at night, particularly in lonelier areas such as the parking lot. Employees should keep their ID cards with them at all points, should never give out personal info and should report any suspicious activity.
Steve Todd, founder of Open Sourced Workplace and is a recognized thought leader in workplace strategy and the future of work. With a passion for work from anywhere, Steve has successfully implemented transformative strategies that enhance productivity and employee satisfaction. Through Open Sourced Workplace, he fosters collaboration among HR, facilities management, technology, and real estate professionals, providing valuable insights and resources. As a speaker and contributor to various publications, Steve remains dedicated to staying at the forefront of workplace innovation, helping organizations thrive in today's dynamic work environment.
Recent Posts
11 Smart Technologies for the Modern Digital Nomad
The rise of the digital nomad has driven a demand for smart technologies. From essential gadgets to innovative software solutions, the digital nomad lifestyle thrives on these revolutionary...
Remote Jobs at Synctera, Amentum, Goldbelt, Scantron, AOC SF
Remote Job opportunity at Yardi Systems, Inc.: Compliance Auditor Job Descriptions:Yardi Systems, Inc. – Compliance AuditorUse your strong prioritization skills to complete certification...
DataScope Templates

IMAGES
VIDEO
COMMENTS
Site information Summary Risk assessment Management policies Physical security Access control Employee security Information security Material security ... and theft, on-site security breaches, rogue or mentally unstable employees and even terrorism. Whether you own or manage hotels, office space, retail operations
View and download Security Site Inspection v2 for free. Browse the public library of over 100,000 free editable checklists for all industries. ... Free Security Site Inspection v2 Checklist. Use this Template Go digital today! ... Conducted on. Date; Prepared by. Location. Address; Personnel. Site Information. Date and Time of Site Visit. Date ...
On-Site Assessment Checklists. The NIST Handbook 150 series checklists, which correspond to the program-specific handbooks, may be downloaded from NVLAP Interactive Web System (NIWS) Lab portal or Assessor portal. Programs that use the Test Method Review Summary in conjunction with the NIST Handbook 150 Checklists are flagged by an asterisk.
USCIS started the Administrative Site Visit and Verification Program in July 2009 as an additional way to verify information in certain visa petitions. Under this program, immigration officers in the Fraud Detection and National Security Directorate (FDNS) make unannounced site visits to collect information as part of a compliance review.
A site visit provides a good opportunity for one-on-one discussions with individuals, such as the director of information security or call center team leaders. During the visit, you can ask follow up questions related to your findings. ... Checklist. Vendor site visits can provide your organization with an extra layer of protection against ...
View and download SECURITY SITE INSPECTION for free. Browse the public library of over 100,000 free editable checklists for all industries.
We've compiled the most useful free ISO 27001 information security standard checklists and templates, including templates for IT, HR, data centers, and surveillance, as well as details for how to fill in these templates. Included on this page, you'll find an ISO 27001 checklist and an ISO 27001 risk assessment template, as well as an up-to ...
The Site Visit Protocol (SVP) is a guide to the operational site visits (OSVs) we conduct at health centers. It includes what we look for and how we assess compliance. It aligns with the Health Center Program Compliance Manual. Changes made to the SVP. In 2023, we improved the format of the SVP and made it easier to read.
7. Invest in anti-malware software. Action Item: Get anti-malware or malware detector software to protect your site against malware infections, which can result in stolen customer data, lost money, and more. A few trusted malware software providers (both free and paid) include Quttera, SUCURI, and Astra Security.
A site visit analysis is a comprehensive report that summarizes the findings of a physical inspection of a potential development site. It includes information on the site's physical characteristics, location, surrounding area, demographic information, environmental impact, zoning regulations, traffic flow, and recommendations for development.
1) Identify potential security threats. Knowing what you need to protect against will help you identify the best security technology for your building. The most common security threats to businesses include: Theft and vandalism. Insider breach involving sensitive data. Negligent data management. Phishing attacks. Physical attacks.
The Security Assessment at First Entry (SAFE), is a stand-alone assessment, featuring standard language, high level vulnerabilities, and options for ... After completing the SAFE visit, the PSA delivers a short report containing: A list of existing good practices to sustain: During the assessment, the PSA will make note of existing good ...
Vendor Site Visits. Whether it's in-person or virtual, site visits can provide you with a point-in-time assessment of your organization's critical or high-risk vendors and answers to remaining questions. In partnership with assurance, accounting, tax and consulting firm, Wipfli, we've put together this handy checklist and infographic to ensure ...
For all questions related to the Checklist content, please contact the DISA STIG Customer Support Desk at [email protected]. 0 0 cyberx-mw cyberx-mw 2021-08-05 14:44:52 2021-08-05 14:44:52 DISA Has Released the Traditional Security Checklist, V2R1
View and download Monthly Site Visit Report Security for free. Browse the public library of over 100,000 free editable checklists for all industries. ... Free Monthly Site Visit Report Security Checklist. Use this Template Go digital today! Convert your paper checklists into digital forms.
Fragile items such as those made of glass and breakable material should be kept in secure, immovable spaces. 23. The next aspect a workplace security inspection checklist must cover is lighting and ventilation. Other than parking lot lighting, office lighting is also important.
This checklist is adapted from the Coast Guard PIO Job Aid. Use this checklist for accomplishing all public affairs-related tasks before, during and after a VIP/DV visit. Check with the point of contact (POC) and the coordination staff to ensure there are no additional tasks. Prior to the Visit Determine the reason for the visit and obtain ...
Security site inspection checklist - PDF Template. DataScope Templates. PDF Template,
Effective Date: 01-JUL-2017 Site Qualification Visit Page 1 of 4 . SOP-05: Site Qualification Visit . 1. Objective To ensure that the Principal Investigator (PI) and all research team members assisting in the conduct of clinical research are informed about their obligations and responsibilities as they pertain to Good Clinical Practices
Monthly site visit report security checklist - PDF Template. DataScope Templates. PDF Template, Winn's security.
View and download Site Visit Checklist for free. Browse the public library of over 100,000 free editable checklists for all industries. ... Are personnel aware of their company's Security Policy and have they completed their annual training? <br>Interview and verify records for the Security Policy training. Yes. No. N/A.
Sign on to a system with the intention of committing an offence.<br>3. Sign on to a system that your are not authorised to use and then modify any data.<br>4. Deliberately do something that causes a degradation. failure or other adverse impact on a computer system. Safe.
As we prepare to transition to the Defense Information System for Security (DISS), the below information will help guide you through Debriefing and Suspending Access. Permissions/Roles Required: ... AND SECURITY AGENCY Visit Information Example 1. Enter Visit Name. • This is a free text field. 2. Enter Start Date and End Date.